Difference between revisions of "OpenVPN Bridge"
| (125 intermediate revisions by 18 users not shown) | |||
| Line 1: | Line 1: | ||
{{Languages}} | {{Languages}} | ||
| + | {{usefulnote}} | ||
| + | <blockquote style="float: right;">[[File:openvpn.png|250px]]</blockquote><br> | ||
| + | ===Maintainer=== | ||
| + | [mailto:daniel@firewall-services.com][[User:VIP-ire|Daniel B.]] from [http://www.firewall-services.com Firewall Services] | ||
| + | ===Version=== | ||
| − | + | {{#smeversion: smeserver-openvpn-bridge }} | |
| − | |||
| − | |||
| − | |||
| − | + | {{#smeversion: smeserver-bridge-interface}} | |
| − | |||
| − | === Description === | + | ===Description=== |
[http://openvpn.net OpenVPN] is a full-featured open source SSL VPN solution that accommodates a wide range of configurations, including remote access, site-to-site VPNs, Wi-Fi security, and enterprise-scale remote access solutions with load balancing, fail-over, and fine-grained access-controls. Starting with the fundamental premise that complexity is the enemy of security, OpenVPN offers a cost-effective, lightweight alternative to other VPN technologies that is well-targeted for the SME and enterprise markets. | [http://openvpn.net OpenVPN] is a full-featured open source SSL VPN solution that accommodates a wide range of configurations, including remote access, site-to-site VPNs, Wi-Fi security, and enterprise-scale remote access solutions with load balancing, fail-over, and fine-grained access-controls. Starting with the fundamental premise that complexity is the enemy of security, OpenVPN offers a cost-effective, lightweight alternative to other VPN technologies that is well-targeted for the SME and enterprise markets. | ||
| Line 17: | Line 18: | ||
This contrib will help you configuring OpenVPN in bridge mode. With this mode, clients connecting to the VPN from the outside will get an IP in the local subnet, the VPN and the Internal Interface are bridged. There's no routing problem, no additional firewall rules. The downside is that you cannot limit which services VPN clients has access to, they are just treated as locally connected computers. | This contrib will help you configuring OpenVPN in bridge mode. With this mode, clients connecting to the VPN from the outside will get an IP in the local subnet, the VPN and the Internal Interface are bridged. There's no routing problem, no additional firewall rules. The downside is that you cannot limit which services VPN clients has access to, they are just treated as locally connected computers. | ||
| − | === Requirements === | + | ===Requirements=== |
| − | + | ||
*You have to install and enable the [[BridgeInterface|bridge-interface]] contrib | *You have to install and enable the [[BridgeInterface|bridge-interface]] contrib | ||
*You may want to install [[PHPki]] to manage easily your certificates. | *You may want to install [[PHPki]] to manage easily your certificates. | ||
| − | + | ===Installation=== | |
| − | |||
| − | === | + | <tabs container><tab name="For SME 10"> |
| + | /!\ new default cipher = AES-128-CBC and HMAC SHA256, if you have issues check the configuration options | ||
| + | yum --enablerepo=smecontribs install smeserver-openvpn-bridge | ||
| − | + | </tab> | |
| + | <tab name="For SME 9"> | ||
| + | you have to enable the '''[[epel]]''' repository | ||
| + | yum --enablerepo=smecontribs,epel install smeserver-openvpn-bridge | ||
| + | </tab> | ||
| + | <tab name="For SME 8"> | ||
yum --enablerepo=smecontribs install smeserver-openvpn-bridge | yum --enablerepo=smecontribs install smeserver-openvpn-bridge | ||
| + | </tab> | ||
| + | </tabs> | ||
| − | |||
| − | + | ====Configure the certificates==== | |
| + | {{Note box|If you use [[PHPki]] to manage the certificates, you can go [[OpenVPN_Bridge#Using_PHPki_to_manage_the_certificates|here]] for more details. | ||
| + | If you are updating a previous installation, you can go [[OpenVPN_Bridge#Migrate_previous.2Fexisting_OpenVPN_Server_certificates|here]]}} | ||
| − | + | You can now go in the server-manager, you'll find a new OpenVPN-Bridge menu. Here, you will first have to click on the "configure certificates" link and you will need to enter various mandatory information: | |
| − | {{Note box|All the certificates have to be PEM encoded}} | + | {{Note box|All the certificates have to be [http://en.wikipedia.org/wiki/Privacy_Enhanced_Mail PEM] encoded}} |
*An URL where OpenVPN can update the CRL. If you use PHPki on the same server, you can let the default value. | *An URL where OpenVPN can update the CRL. If you use PHPki on the same server, you can let the default value. | ||
{{Note box|If a valid CRL file (in PEM format) is not found at this URL, you'll get an email every hour in the admin mailbox}} | {{Note box|If a valid CRL file (in PEM format) is not found at this URL, you'll get an email every hour in the admin mailbox}} | ||
| + | |||
*A master Certificate (used to verify clients certificates) | *A master Certificate (used to verify clients certificates) | ||
*The server certificate (used by clients to verify the server) | *The server certificate (used by clients to verify the server) | ||
*The server private key associated with the certificate | *The server private key associated with the certificate | ||
*Diffie-Helman parameters (Used to exchange the session key) | *Diffie-Helman parameters (Used to exchange the session key) | ||
| − | *An optional key generate by | + | *An optional key generate by OpenVPN to add TLS authentication |
| − | {{Note box|You can | + | {{Note box|You can leave this field blank if you don't want to use the additional TLS auth}} |
| − | You can use [[PHPki]] contrib to manage this easily. [[PHPki]] doesn't need to be installed on the same server. You can also manage your PKI | + | You can use [[PHPki]] contrib to manage this easily. [[PHPki]] doesn't need to be installed on the same server. You can also manage your PKI manually, or with your own PKI tool if you already use one (for example, [http://tinyca.sm-zone.net/ tinyCA]) |
Once you have enter all the required information, just submit the form. | Once you have enter all the required information, just submit the form. | ||
| Line 59: | Line 70: | ||
With "Certificates are ready" in green. If it's not the case, you have a problem with the certificates configuration. | With "Certificates are ready" in green. If it's not the case, you have a problem with the certificates configuration. | ||
| + | ====Configure the service==== | ||
| + | The second step is to configure the service. In the main page of the panel, click on the "Service configuration" button. Here you can enable the service, choose the authentication mode you want, and configure the IP address range for the clients. Once you submit this form, the service should start. You can check everything is ok with this command: | ||
| + | tailf /var/log/openvpn-bridge/current | ||
| − | |||
| − | + | ====Control the service==== | |
| + | Starting with version 2.0, OpenVPN daemon is now supervised. | ||
| + | You can control (start/stop/restart) the service from the server-manager, and you're advised to do so. But if you want to manually start/stop/restart the service, here are the corresponding commands: | ||
| − | + | *start | |
| − | + | sv u /service/openvpn-bridge | |
| − | + | ||
| + | *stop | ||
| + | |||
| + | sv d /service/openvpn-bridge | ||
| + | |||
| + | *restart | ||
| + | |||
| + | sv t /service/openvpn-bridge | ||
| + | {{Warning box|The script '''/etc/init.d/openvpn''' provided with OpenVPN rpm should not be used with SME. Do not try to use this script to control the service, it will not work due to SME templating system!!}} | ||
| − | === Using PHPki to manage the certificates === | + | ===Using PHPki to manage the certificates=== |
With this new release, you can manage the certificates the way you want, but most of you will use [[PHPki]] for this. | With this new release, you can manage the certificates the way you want, but most of you will use [[PHPki]] for this. | ||
| − | + | ====Initialize your [http://en.wikipedia.org/wiki/Public_key_infrastructure PKI]==== | |
| − | This should already be done as you have installed the contrib following [[PHPki#Installation| | + | This should already be done as you have installed the contrib following this [[PHPki#Installation|how-to]]. |
| − | + | ====Create a certificate for the server==== | |
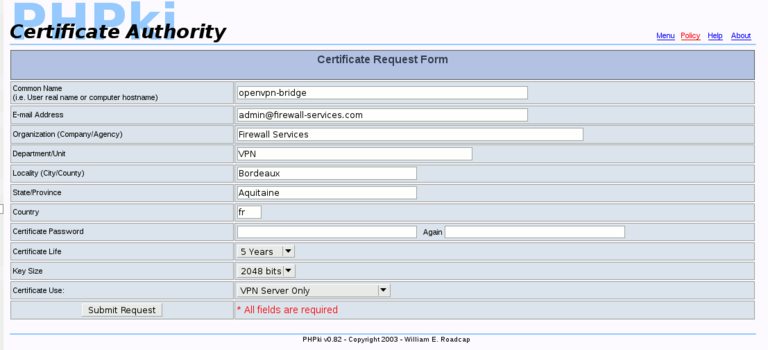
| − | Now you need to create a certificate for OpenVPN on the server. For this, go in PHPki interface, then "create a new certificate". Here, you'll have to enter some informations about the certificate: | + | Now you need to create a certificate for OpenVPN on the server. For this, go in [[PHPki]] interface, then "create a new certificate". Here, you'll have to enter some informations about the certificate: |
| − | * | + | *'''Common Name''': this is the name of the certificate. You can enter what you want, for example "openvpn-bridge" |
| − | * | + | *'''Email address''': the email address of the technical contact (this field is not used, you can enter what you want as long as it's a valid email address), for example admin@domain.tld |
| − | * | + | *'''Organization''', '''Department''', '''Locality''', '''State and Country''' fields should have the values you entered when you have created your PKI. You can let those values. |
| − | * | + | *'''Password''': '''This field must be blank'''. Remember that OpenVPN daemon starts without human intervention when the server boots, so it need to have access to the certificate key without being prompted for a password. |
| − | * | + | *'''Certificate life''': How-long the certificate will be valid. Enter what you want, but remember, when the certificate expires, you'll have to create another one, and update it in OpenVPN Bridge panel. |
| − | * | + | *'''Key size''': you can enter what you want (I use 2048 in general). The bigger, the stronger, but will use a bit more CPU power when the session key is negotiated (at the connection, and once an hour) |
| − | * | + | *'''Certificate Use''': you should use "VPN Server Only". '''This is important'''. If you don't choose this type of certificates, clients may be unable to connect, or you may be unable to proceed as some other certificate uses won't allow an empty password. |
| + | Here's an example: | ||
| + | [[File:Phpki_ovpn_bridge_server_crt.png|768px|thumb|center|Create a new certificate for the server side]] | ||
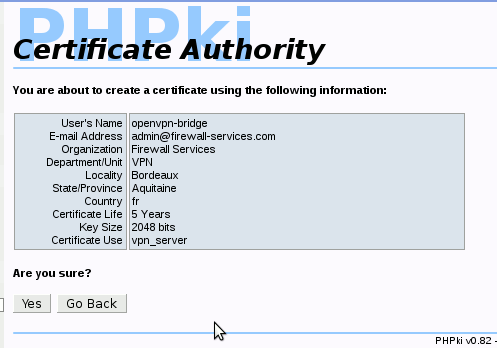
| + | Now, confirm you want to create this certificate: | ||
| + | [[File:Phpki_confirm_crt.png|768px|thumb|center|Confirm the creation of the new certificate]] | ||
| + | ====Configure OpenVPN with the newly created certificates==== | ||
| − | + | {{Note box|If you update an existing smeserver-openvpn-bridge installation, you can skip this part, and go directly [[OpenVPN_Bridge#Upgrade_from_smeserver-openvpn-bridge-fws-1.1-2|here]]}} | |
| − | |||
Now, you can configure OpenVPN with your certificates. Go in the server-manager->OpenVPN-Bridge->certificates configuration. | Now, you can configure OpenVPN with your certificates. Go in the server-manager->OpenVPN-Bridge->certificates configuration. | ||
| Line 99: | Line 126: | ||
Here you have some fields to setup: | Here you have some fields to setup: | ||
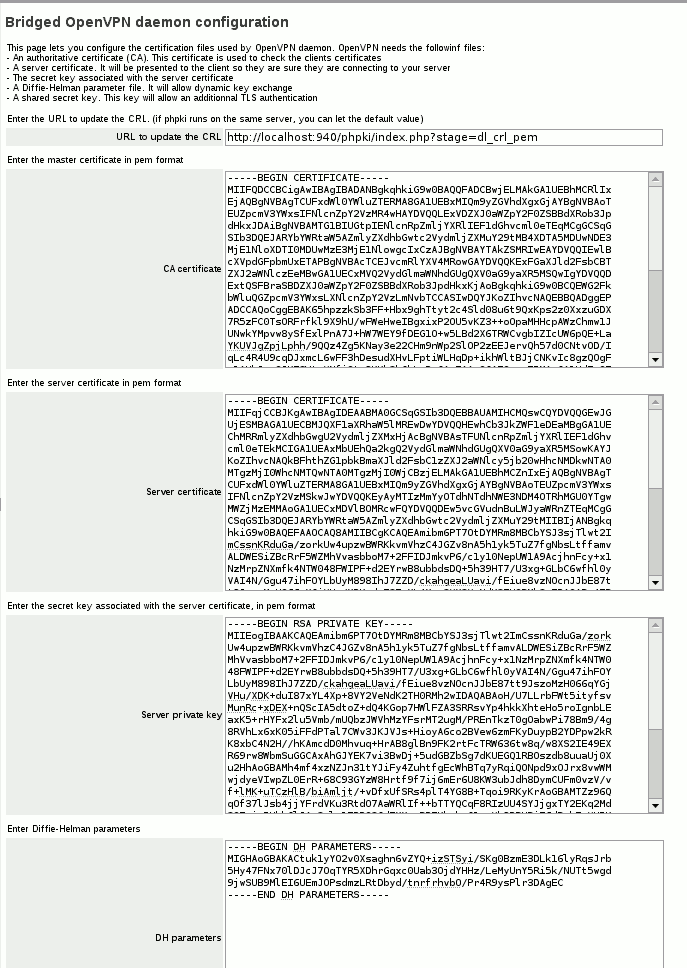
| − | * | + | *'''URL to update the CRL''': you should let the default: http://localhost:940/phpki/index.php?stage=dl_crl_pem unless [[PHPki]] is installed on another server (or if you use another PKI tool) |
| − | * | + | *'''CA certificate''': You should put here the Root certificate in PEM format. You can get it in [[PHPki]], by clicking on the link "Display the Root Certificate (PEM Encoded)" Copy and paste this data into the "CA certificate" box. |
| − | * | + | *'''Server certificate''': You should put here the certificate of the server. You can get it in [[PHPki]], manage certificates, click on the download link corresponding to the certificate you have created for the server ("openvpn-bridge" in the example), choose PEM certificate in the drop-down menu, download it. You can open this file with a text editor. Copy and paste this text into the "Server certificate" window. |
| − | * | + | *'''Server private key''': This is the private key associated with the server's certificate. To get it, follow the same steps as above, but choose "PEM Key" in the drop-down menu instead of "PEM Certificate" and paste the text into the "Server private key" window. |
| − | * | + | *'''DH Parameters''': To get the DH Parameters, click on the "Display the Diffie-Hellman parameters" link in [[PHPki]] and paste the text into the "DH parameters" window. |
| − | * | + | *'''Static Key''': This is optional. You can get it using the "Display the static pre-shared key" link in [[PHPki]]. Note that if you enter this key on the server, you'll have to deploy it on each client. |
| + | You can now submit the request. "Certificates are ready" should be displayed. | ||
| + | Here's an example: | ||
| + | [[File:Ovpn_bridge_config_crt.png|768px|thumb|center|Copy the certificates and keys in OpenVPN Bridge panel]] | ||
| − | + | ===Upgrade from smeserver-openvpn-bridge-fws-1.1-2=== | |
| − | + | If you was using the previous version of the contrib, follow this part. It will migrate the certificate configuration from the previous installation. | |
| − | + | ====Install the [[PHPki]] contrib==== | |
| − | |||
| − | |||
First, you'll have to install [[PHPki]]. Be sure to follow the [[PHPki#Migrate_Certificates_from_previous_OpenVPN-Bridge_contrib_installations|migration step]] | First, you'll have to install [[PHPki]]. Be sure to follow the [[PHPki#Migrate_Certificates_from_previous_OpenVPN-Bridge_contrib_installations|migration step]] | ||
| − | + | ====Install the latest OpenVPN contrib==== | |
yum --enablerepo=smecontribs install smeserver-openvpn-bridge | yum --enablerepo=smecontribs install smeserver-openvpn-bridge | ||
You can configure the bridge-interface contrib now. You can follow this [[BridgeInterface|how-to]] | You can configure the bridge-interface contrib now. You can follow this [[BridgeInterface|how-to]] | ||
| − | + | ====Migrate previous/existing OpenVPN Server certificates==== | |
Now, you should install the old certificates in the new location | Now, you should install the old certificates in the new location | ||
For this, you can use this script: | For this, you can use this script: | ||
| Line 135: | Line 163: | ||
OLDDIR=/etc/openvpn/easy-rsa/keys/bridge/ | OLDDIR=/etc/openvpn/easy-rsa/keys/bridge/ | ||
OVPNNEWDIR=/etc/openvpn/bridge | OVPNNEWDIR=/etc/openvpn/bridge | ||
| + | SRVCN=$(db configuration getprop openvpn-bridge localCN) | ||
convert_cert_to_rule_entries(){ | convert_cert_to_rule_entries(){ | ||
DBNAME='openvpn-bridge' | DBNAME='openvpn-bridge' | ||
| − | # The new | + | # The new OpenVPN contrib doesn't use cert entries but rules ones |
# So we need to convert it | # So we need to convert it | ||
if [ -e /home/e-smith/db/$DBNAME ]; then | if [ -e /home/e-smith/db/$DBNAME ]; then | ||
| Line 149: | Line 178: | ||
REDIR=$(/sbin/e-smith/db $DBNAME.$TIME getprop $CERT redirectGW) | REDIR=$(/sbin/e-smith/db $DBNAME.$TIME getprop $CERT redirectGW) | ||
IP=$(/sbin/e-smith/db $DBNAME.$TIME getprop $CERT ip) | IP=$(/sbin/e-smith/db $DBNAME.$TIME getprop $CERT ip) | ||
| − | # Blank out the IP if | + | # Blank out the IP if defined as 'undef' |
if [ $IP == 'undef' ]; then | if [ $IP == 'undef' ]; then | ||
| − | IP= | + | IP= |
fi | fi | ||
/sbin/e-smith/db $DBNAME set $CERT rule comment "$COM" redirectGW "$REDIR" ip "$IP" | /sbin/e-smith/db $DBNAME set $CERT rule comment "$COM" redirectGW "$REDIR" ip "$IP" | ||
| Line 160: | Line 189: | ||
install_cert_in_new_dir(){ | install_cert_in_new_dir(){ | ||
| − | # Here, we install the old certificates used by | + | # Here, we install the old certificates used by OpenVPN daemon to the new location |
mkdir -p $OVPNNEWDIR/{priv,pub} | mkdir -p $OVPNNEWDIR/{priv,pub} | ||
cat $OLDDIR/$SRVCN.crt > $OVPNNEWDIR/pub/cert.pem | cat $OLDDIR/$SRVCN.crt > $OVPNNEWDIR/pub/cert.pem | ||
| Line 173: | Line 202: | ||
# Restrict access | # Restrict access | ||
chown -R root:root $OVPNNEWDIR | chown -R root:root $OVPNNEWDIR | ||
| − | chmod -R o-rwx $OVPNNEWDIR | + | chmod -R o-rwx $OVPNNEWDIR/priv |
} | } | ||
| Line 182: | Line 211: | ||
Save this script and run it as root. | Save this script and run it as root. | ||
| − | === Configuration rules === | + | ===Configuration rules=== |
| + | |||
| + | The configuration rules is the new way to apply specific configuration to a client. As now the certificates are managed separately, you have to create rules separately. It's still quite simple, just add a new rule, enter the common name to match, a comment, choose an optional fixed IP, choose to enable/disable the gateway redirection, or even block a specific client. Then save, and you're done. | ||
| + | |||
| + | ===Client Configuration=== | ||
| + | |||
| + | OpenVPN runs on most platforms. | ||
| + | In any case, the first step will always be the same: you have to create a new certificate for the client. | ||
| + | |||
| + | ====Create the certificate with PHPki==== | ||
| + | |||
| + | If you use your own PKI tool, you should be able to do it yourself ;) | ||
| + | If you use [[PHPki]], here are the steps to follow | ||
| + | |||
| + | *In [[PHPki]] administrative interface, click on the "Create a new certificate" link. | ||
| + | |||
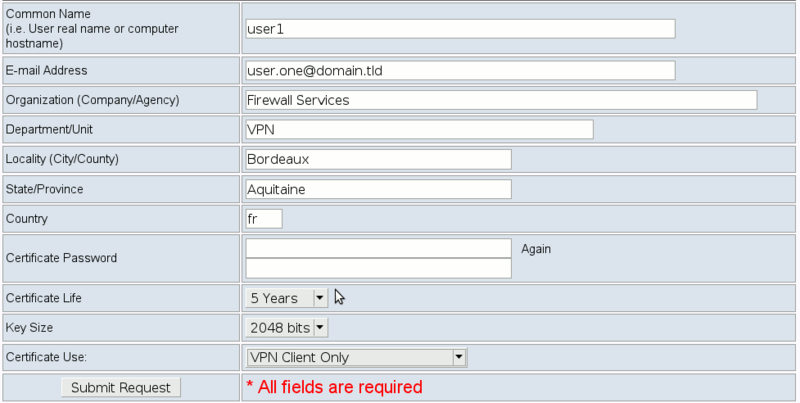
| + | Here, you'll have to enter several informations. Most of them are up to you. Here's an example: | ||
| + | [[File:Phpki_ovpn_bridge_create_client_crt.png|800px|thumb|center|Create a new certificate for the client]] | ||
| + | |||
| + | {{Warning box|Valid certificate uses for OpenVPN Bridge are | ||
| + | *Email, SSL Client | ||
| + | *Email, SSL Client, Code Signing | ||
| + | *VPN Client Only | ||
| + | *VPN Client, VPN Server | ||
| + | |||
| + | Email, SSL Client and Email, SSL Client, Code Signing require a password to protect the key, so you'll have to enter an additional password when connecting.}} | ||
| + | |||
| + | {{Note box|If you plan to use this certificate only for the VPN, the recommended usage is VPN Client Only}} | ||
| − | The | + | {{Note box|The Certificate Life is useful if you want to grant someone a VPN access for a limited periode of time. Once the certificate has expired, the server will reject it (without the need to manually revoke it)}} |
| − | + | {{Note box|Even if PHPki accepts a lot of characters for the common name, I personally recommend to use simple characters (lowercase, numbers, underscore, dash)}} | |
| − | On the | + | Once you have submitted this form, you'll have a confirmation page. Then your certificate will be ready. |
| − | + | ||
| + | Now, go in the "Manage Certificates" menu in [[PHPki]] and click on the Download link corresponding to your certificate, then choose the PKCS#12 bundle format (OpenVPN also accept pem encoded certificate, but the PKCS#12 bundle has the advantage of combining the CA, the certificate and the key in one file). | ||
| + | |||
| + | If you have configured and shared secret key on the server, you also need to download it. | ||
| + | |||
| + | ====Windows==== | ||
| + | For Windows systems, you should download the OpenVPN GUI stable release 2.4.4 from https://openvpn.net/index.php/download/community-downloads.html. OpenVPN includes the Windows GUI in the installer. | ||
| + | |||
| + | On Windows, the configuration directory for OpenVPN is C:\Program Files\OpenVPN\config | ||
| + | Here you can put all the needed files, or create sub-directories if you want to configure several connexions. | ||
| + | Put here (either in the config directory or in a sub folder) the PKCS#12 file you have downloaded earlier, and the shared secret key if you used one on the server. | ||
| + | Now create a text file, and change the extension to be .ovpn (the name isn't important). Edit it with your favorite text editor. | ||
| + | Now, go in the panel of OpenVPN-Bridge and click on the link "Display a functional client configuration file". Copy and past this in your config file (.ovpn), and just change the pkcs12 directive to match your certificate name. Save this file. | ||
| + | Now your client should be able to connect with the OpenVPN GUI. | ||
| + | |||
| + | ====Linux with Network Manager==== | ||
| + | {{Incomplete}} | ||
| + | You can see french page for Debian. | ||
| + | =====Ubuntu 12.10 64bit===== | ||
| + | (Not tested in 32bit but will most likely work) | ||
| + | If possible follow the above windows tutorial first to test that you have configured openvpn correctly for server and client. | ||
| + | |||
| + | *'''Install openvpn for network manager''' | ||
| + | |||
| + | sudo apt-get install network-manager-openvpn | ||
| + | Under Ubuntu 16.04 64bit, we also needed to install "network-manager-openvpn-gnome": | ||
| + | sudo apt-get install network-manager-openvpn-gnome | ||
| + | |||
| + | *Create folder called e.g. "openvpn" (can be anything) in your home directory (could be any directory). | ||
| + | *Assuming that phpki is being used. In browser go to '''server-manager panel > certificate management''' and download the relevant client's "PCKS#12 Bundle" and place it in the "openvpn" folder. | ||
| + | *Go to '''server-manager panel > openvpn-bridge''' click on "Display a functional client configuration file". Copy and paste this into a text editor and save with '''.ovpn''' extension into the "openvpn" folder. Make sure user.p12 is replaced with the name of the .p12 (PCKS#12 Bundle) client file downloaded previously. Also check that the '''remote''' (gateway) is the correct server url. | ||
| + | *In ubuntu go to '''Network Manager > VPN Connections > Configure VPN'''. Click '''import''' then in the explorer navigate to the openvpn folder in the home directory and select the .ovpn file created previously. This should automatically load all settings into network manager. | ||
| + | *Add username and password of client, then you have to give the path of the '''user.p12''' key of your user and set the Private key password (the password set during the certificate creation in phpki). | ||
| + | *After that you have to select the 'advanced' panel and go to 'TLS authentication'. Enable the use of TLS authentication, give the path or your '''takey.pem''' and select the key direction to 1. (if needed) | ||
| + | *As a note, when connected successfully to the vpn, browsing the internet may not work in tandem, therefore go to '''ipv4 settings''' tab when editing the vpn connection. Click on "Routes" and check "Use this connection only for resources on its network". Also try adding 8.8.4.4 to "Additional DNS Servers" (This is google's dns servers). | ||
| + | |||
| + | =====Fedora 16 / 17 64bit===== | ||
| + | (Not tested in 32bit but will most likely work) | ||
| + | |||
| + | Note: server set as user/pass + certificate | ||
| + | |||
| + | *'''Install openvpn for network manager''' | ||
| + | |||
| + | yum install NetworkManager-openvpn | ||
| + | |||
| + | |||
| + | ======manual settings====== | ||
| + | |||
| + | *Assuming that phpki is being used. In browser go to '''server-manger panel > certificate management''' and download the relevant client's "PCKS#12 Bundle" and place it into one convenient folder. | ||
| + | *go to '''yournuserame > System Settings > Network''' click on little '''+''' sign on bottom left | ||
| + | *in the new pop-up window select '''VPN''' then push Create | ||
| + | *select '''OpenVPN''' and push Create | ||
| + | *select password with certificate (or any other method you set on server) | ||
| + | *put credentials for user and private key password | ||
| + | *set the gateway as your ''server.domain.tld '' | ||
| + | *at advanced check ''Use LZO data compression'' | ||
| + | *at advanced check '' Use a TAP device'' | ||
| + | *at TLS authentication, give the path of the takey.pem and enable it with the direction 1 (if needed) | ||
| + | *click on the small folder near the first certificate and go to the bundle certificate downloaded into convenient folder - all certificates should be filled up | ||
| + | *Note: I recommend to check also in '''IPv4 > route''' ''Use this connection only for resources on its network"'' | ||
| + | *save and test | ||
| + | |||
| + | ======import settings====== | ||
| + | |||
| + | *Create folder called e.g. ".openVPN" (can be anything) in your home directory (could be any directory). | ||
| + | *Assuming that phpki is being used. In browser go to '''server-manger panel > certificate management''' and download the relevant client's "PCKS#12 Bundle" and place it in the ".openVPN" folder. | ||
| + | *Go to '''server-manager panel > openvpn-bridge''' click on "Display a functional client configuration file". Copy and paste this into a text editor and save with '''.ovpn''' extension into the "openVPN" folder (the name of the file will be the visible name in network manager to select VPN connection). Make sure user.p12 is replaced with the name of the .p12 (PCKS#12 Bundle) client file downloaded previously. Also check that the '''remote''' (gateway) is the correct server url. | ||
| + | *In fedora ALT+F2 enter ''nm-connection-editor'' and ENTER | ||
| + | *go to '''Network Connections > VPN '''. Click '''Import''' then in the explorer navigate to the openvpn folder in the home directory and select the .ovpn file created previously. This should automatically load all settings into network manager. | ||
| + | *Add username and password of client. Private key password which could differ from the user pass (and will not change if user/admin will change user password in ''server-manager'' or ''server-user''. it is the password set during the certificate creation). Now give also the path of certificate '''user.p12''' | ||
| + | *at Advanced/TLS authentication, give the path of the takey.pem and enable it with the direction 1 (if needed) | ||
| + | *Note: I recommend to check also in '''IPv4 > route''' ''Use this connection only for resources on its network'' (unless you use the "Redirect Gateway" functionality) | ||
| + | *save and test | ||
| + | |||
| + | =====Fedora 19 64bit===== | ||
| + | (Not tested in 32bit but will most likely work) | ||
| + | |||
| + | the import feature apparently does not work | ||
| + | |||
| + | also the ""bundle" does not work | ||
| + | |||
| + | you'll need to | ||
| + | |||
| + | *Assuming that phpki is being used. In browser go to '''server-manager panel > certificate management''' and download the relevant client's cacert.pem user.pem user-key.pem and place them into one convenient place. | ||
| + | *go to '''yournuserame > System Settings > Network''' click on little '''+''' sign on bottom left | ||
| + | *in the new pop-up window select '''VPN''' then push Create | ||
| + | *select '''OpenVPN''' and push Create | ||
| + | *select password with certificate (or any other method you set on server) | ||
| + | *put credentials for user and private key password | ||
| + | *set the gateway as your ''server.domain.tld '' | ||
| + | *at advanced check ''Use LZO data compression'' | ||
| + | *at advanced check '' Use a TAP device'' | ||
| + | *click on the small folder near the first certificate and go to the user.pem certificate downloaded into convenient folder | ||
| + | *click on the small folder near the second certificate and go to the cacert.pem certificate downloaded into convenient folder | ||
| + | *click on the small folder near the third certificate and go to the user-key.pem certificate downloaded into convenient folder | ||
| + | **Note: I recommend to check also in '''IPv4 > route''' ''Use this connection only for resources on its network"'' | ||
| + | *save and test | ||
| + | |||
| + | ====Linux==== | ||
| + | {{Incomplete}} | ||
| + | ====Mac OS X==== | ||
| + | {{Incomplete}} | ||
| + | OpenVPN works great with [http://code.google.com/p/tunnelblick/ Tunnelblick]. | ||
| + | |||
| + | Download the PKCS#12 file to a convenient location. In that same location, create a text file using TextEdit or any other text editor. Name it anything you choose, with a file extension of .ovpn (for example, user.ovpn). | ||
| + | Now, go in the panel of OpenVPN-Bridge and click on the link "Display a functional client configuration file". Copy and paste this into your config file (.ovpn), and change the pkcs12 directive to match your certificate name, like this: | ||
pkcs12 user.p12 | pkcs12 user.p12 | ||
| − | + | If you want to be able to connect to the VPN server without entering a username and password, comment out the line that says "auth-user-pass", like this: | |
| − | + | #auth-user-pass | |
| − | |||
| − | # | ||
| − | + | Save the .ovpn file, then double-click on it. This will open Tunnelblick and import your configuration. You can then use the Tunnelblick menu to connect to your server. | |
| − | === Advanced configuration === | + | ====iOS==== |
| + | |||
| + | if you plan to connect to Open vpn you can either jailbreak and use GuizmoVPN. | ||
| + | |||
| + | Otherwise you could use the newly available OpenVPN app. However it does not have any tun driver and it needs a server configuration to work : | ||
| + | mkdir -p /etc/e-smith/templates-custom/etc/openvpn/bridge/openvpn.conf/ | ||
| + | echo 'push "topology subnet"' >/etc/e-smith/templates-custom/etc/openvpn/bridge/openvpn.conf/66topology | ||
| + | expand-template /etc/openvpn/bridge/openvpn.conf | ||
| + | service openvpn-bridge restart | ||
| + | |||
| + | ====Android==== | ||
| + | |||
| + | You cannot use TAP mode, and therefore openvpn-bridge, with Android. | ||
| + | |||
| + | Please read this for more: | ||
| + | |||
| + | https://openvpn.net/faq/why-does-the-app-not-support-tap-style-tunnels/ | ||
| + | |||
| + | You can use openvpn-routed: | ||
| + | |||
| + | https://wiki.contribs.org/OpenVPN_Routed | ||
| + | |||
| + | ===Advanced configuration=== | ||
Some advanced options are not presented in the panel. The goal was to keep the panel as simple as possible as most installations won't need to change advanced settings. But advanced options are still available with some DB keys: | Some advanced options are not presented in the panel. The goal was to keep the panel as simple as possible as most installations won't need to change advanced settings. But advanced options are still available with some DB keys: | ||
| − | *'''ConfigRequired''': (enabled|disabled). If set to enable, clients will be rejected | + | *'''ConfigRequired''': (enabled|disabled). If set to enable, clients will be rejected unless a configuration rule match the common name of their certificate. This can be useful if you use just one CA to sign a lot of different certificates, but only want a limited number of certificates to connect to the VPN |
*'''UDPPort''': (number) Change the port the server listen to when running in UDP mode | *'''UDPPort''': (number) Change the port the server listen to when running in UDP mode | ||
| Line 211: | Line 392: | ||
*'''access''': (private|public) you should let this to public as running a VPN server just for the local network make no sens | *'''access''': (private|public) you should let this to public as running a VPN server just for the local network make no sens | ||
| − | *'''cipher''': (valid cipher name) You can force the cipher to use. If you put auto | + | *'''cipher''': (valid cipher name) You can force the cipher to use. Starting SME 10, default is AES-128-CBC . If you put auto ( or delete this key, for SME9 and before ) the default will be the current of openvpn wich is as per 2.4 : BF-CBC. Also when both client and server are at least version 2.4, they will negotiate the stronger cipher both side support. SME10 enforce the following authorized ciphers: --ncp-ciphers AES-256-GCM:AES-128-GCM:AES-256-CBC:AES-128-CBC:BF-CBC . To have the list of the supported cipher, issue the command |
| + | |||
openvpn --show-ciphers | openvpn --show-ciphers | ||
*'''clientToClient''': (enabled|disabled) If you want to prevent two clients to communicate, you should enable this option | *'''clientToClient''': (enabled|disabled) If you want to prevent two clients to communicate, you should enable this option | ||
| + | |||
| + | *'''duplicateCN''': (enabled|disabled) If you want to allow several clients to connect simultaneously using the same certificate, you need to enable this option (default is disabled) | ||
*'''compLzo''': (enabled|disabled) This option control the usage of real time LZO compression. Enabling it usually improve the performance at no cost. It uses an adaptive algorithm, if data sent over the tunnel are uncompress-able, the compression will automatically be disabled. You may want to disable it on small hardware. | *'''compLzo''': (enabled|disabled) This option control the usage of real time LZO compression. Enabling it usually improve the performance at no cost. It uses an adaptive algorithm, if data sent over the tunnel are uncompress-able, the compression will automatically be disabled. You may want to disable it on small hardware. | ||
| − | *'''management''': (<ip to bind to>:<port>:password) this key control the management interface of | + | *'''management''': (<ip to bind to>:<port>:<password>) this key control the management interface of OpenVPN. The default is to listen only on the loopback interface. It's used to display connected clients. You can allow the access on the local network to get some more statistics using for example: http://www.mertech.com.au/mertech-products-openvpnusermanager.aspx |
*'''maxClients''': (number) maximum number of clients connected at a time | *'''maxClients''': (number) maximum number of clients connected at a time | ||
| Line 231: | Line 415: | ||
| + | Also you can also set the property PushRoute "disabled" to any network in networks db to avoid the contrib to push the network to the client. | ||
Once you have configured the service like you want, just run the command | Once you have configured the service like you want, just run the command | ||
signal-event openvpn-bridge-update | signal-event openvpn-bridge-update | ||
| − | === Uninstall === | + | ===Uninstall=== |
To remove the contrib, just run: | To remove the contrib, just run: | ||
yum remove smeserver-openvpn-bridge | yum remove smeserver-openvpn-bridge | ||
| Line 242: | Line 427: | ||
yum remove smeserver-phpki phpki smeserver-bridge-interface perl-Net-OpenVPN-Manage perl-Net-Telnet | yum remove smeserver-phpki phpki smeserver-bridge-interface perl-Net-OpenVPN-Manage perl-Net-Telnet | ||
| − | === Bugs === | + | ===Notes=== |
| + | ====OpenVPN and SME installed in virtual machine - VMWare promiscuous mode==== | ||
| + | By default for all version of ESX(i) starting from 3.5 to 7.0 (current in february 2020) VMWare rejects packets in promiscuous mode on the vSwitch, which will cause trouble with OpenVPN in bridge mode. The main symptom is that after successful authentication from your remote client you can ping/reach only the OpenVPN server while any other ip address on the LAN can't be pinged/reached. To correct this in VMWare set: | ||
| + | Configuration > Networking > your vSwitch: Properties > Ports-tab > vSwitch > Edit > Security-tab > Promiscuous mode: accept | ||
| + | For ESXI hypervisor still working with vSphere client: | ||
| + | |||
| + | [[File:Promiscuous_mode_-_Esxi.jpg|786x786px]] | ||
| + | |||
| + | For ESXI greater than 6.5 using webui client: | ||
| + | |||
| + | [[File:Promiscuous mode - Webui.jpg|border|frameless|784x784px]] | ||
| + | |||
| + | ====OpenVPN and SME installed in virtual machine - Virtualbox promiscuous mode==== | ||
| + | |||
| + | There is the same thing in virtualbox, you need to give the argument "allow all" in the network tab configuration. | ||
| + | |||
| + | virtual machine > configuration > network > adapter 1 | ||
| + | |||
| + | choose adapter type "intel pro 1000....." | ||
| + | |||
| + | then put attached to on "bridged adapter" on your default NIC | ||
| + | |||
| + | click on advanced | ||
| + | |||
| + | then put promiscuous mode on "allow all" | ||
| + | |||
| + | [[Image:virtualbox-Sme8-Settings.png]]<br /> | ||
| + | |||
| + | ====OpenVPN and SME installed in virtual machine - Other hypervisors==== | ||
| + | It's documented that you can experience such problems in other hypervisors like OVirt, Proxmox, XEN or others. Keep in mind to search for equivalent settings concerning "promiscuous mode" of vSwitch. | ||
| + | |||
| + | ====Transparent proxy settings==== | ||
| + | {{Note box|Keep in mind you need to disabled your transparent proxy else your host can no longer browse the http protocol.}} | ||
| + | |||
| + | go to the server-manager>Proxy services and disabled http and smtp proxy | ||
| + | |||
| + | |||
| + | [[Image:proxy-setting.png|width|800px]]<br /> | ||
| + | |||
| + | ===Workarounds and known issues=== | ||
| + | if you migrate from SME8 to SME9 and are not able to connect after correctly migrating your certificates, this might be related to not secure enough algorithm. CentOS 6.9 release notes state that "Support for insecure cryptographic protocols and algorithms has been dropped. This affects usage of MD5, SHA0, RC4 and DH parameters shorter than 1024 bits." Of course real solution would be to migrate all your certs to better algorithm. | ||
| + | |||
| + | workaround :<syntaxhighlight lang="bash" line="1"> | ||
| + | echo -e "LegacySigningMDs md2 md5\nMinimumDHBits 512\n" >> /etc/pki/tls/legacy-settings | ||
| + | service openvpn-bridge restart | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | ===Bugs=== | ||
Please raise bugs under the SME-Contribs section in [http://bugs.contribs.org/enter_bug.cgi bugzilla] | Please raise bugs under the SME-Contribs section in [http://bugs.contribs.org/enter_bug.cgi bugzilla] | ||
and select the smeserver-openvpn-bridge component or use {{BugzillaFileBug|product=SME%20Contribs|component=smeserver-openvpn-bridge|title=this link}} | and select the smeserver-openvpn-bridge component or use {{BugzillaFileBug|product=SME%20Contribs|component=smeserver-openvpn-bridge|title=this link}} | ||
| + | |||
| + | |||
| + | {{#bugzilla:columns=id,product,version,status,summary |sort=id |order=desc |component=smeserver-openvpn-bridge|noresultsmessage="No open bugs found."}} | ||
| + | ===Changelog=== | ||
| + | Only versions released in smecontrib are listed here. | ||
| + | |||
| + | {{#smechangelog: smeserver-openvpn-bridge}} | ||
| + | |||
| + | ==Other articles in this category== | ||
| + | {{#ask: [[Category:VPN]]}} | ||
---- | ---- | ||
[[Category:Contrib]] | [[Category:Contrib]] | ||
| + | [[Category:Administration:VPN]] | ||
| + | [[Category:VPN]] | ||
Latest revision as of 08:32, 10 November 2023
Is this article helpful to you?
Please consider donating or volunteering
Thank you!
Maintainer
[1]Daniel B. from Firewall Services
Version
Description
OpenVPN is a full-featured open source SSL VPN solution that accommodates a wide range of configurations, including remote access, site-to-site VPNs, Wi-Fi security, and enterprise-scale remote access solutions with load balancing, fail-over, and fine-grained access-controls. Starting with the fundamental premise that complexity is the enemy of security, OpenVPN offers a cost-effective, lightweight alternative to other VPN technologies that is well-targeted for the SME and enterprise markets.
This contrib will help you configuring OpenVPN in bridge mode. With this mode, clients connecting to the VPN from the outside will get an IP in the local subnet, the VPN and the Internal Interface are bridged. There's no routing problem, no additional firewall rules. The downside is that you cannot limit which services VPN clients has access to, they are just treated as locally connected computers.
Requirements
- You have to install and enable the bridge-interface contrib
- You may want to install PHPki to manage easily your certificates.
Installation
/!\ new default cipher = AES-128-CBC and HMAC SHA256, if you have issues check the configuration options
yum --enablerepo=smecontribs install smeserver-openvpn-bridge
you have to enable the epel repository
yum --enablerepo=smecontribs,epel install smeserver-openvpn-bridge
yum --enablerepo=smecontribs install smeserver-openvpn-bridge
Configure the certificates
You can now go in the server-manager, you'll find a new OpenVPN-Bridge menu. Here, you will first have to click on the "configure certificates" link and you will need to enter various mandatory information:
- An URL where OpenVPN can update the CRL. If you use PHPki on the same server, you can let the default value.
- A master Certificate (used to verify clients certificates)
- The server certificate (used by clients to verify the server)
- The server private key associated with the certificate
- Diffie-Helman parameters (Used to exchange the session key)
- An optional key generate by OpenVPN to add TLS authentication
You can use PHPki contrib to manage this easily. PHPki doesn't need to be installed on the same server. You can also manage your PKI manually, or with your own PKI tool if you already use one (for example, tinyCA)
Once you have enter all the required information, just submit the form.
You should then see the message:
Certificates status Certificates are ready
With "Certificates are ready" in green. If it's not the case, you have a problem with the certificates configuration.
Configure the service
The second step is to configure the service. In the main page of the panel, click on the "Service configuration" button. Here you can enable the service, choose the authentication mode you want, and configure the IP address range for the clients. Once you submit this form, the service should start. You can check everything is ok with this command:
tailf /var/log/openvpn-bridge/current
Control the service
Starting with version 2.0, OpenVPN daemon is now supervised. You can control (start/stop/restart) the service from the server-manager, and you're advised to do so. But if you want to manually start/stop/restart the service, here are the corresponding commands:
- start
sv u /service/openvpn-bridge
- stop
sv d /service/openvpn-bridge
- restart
sv t /service/openvpn-bridge
Using PHPki to manage the certificates
With this new release, you can manage the certificates the way you want, but most of you will use PHPki for this.
Initialize your PKI
This should already be done as you have installed the contrib following this how-to.
Create a certificate for the server
Now you need to create a certificate for OpenVPN on the server. For this, go in PHPki interface, then "create a new certificate". Here, you'll have to enter some informations about the certificate:
- Common Name: this is the name of the certificate. You can enter what you want, for example "openvpn-bridge"
- Email address: the email address of the technical contact (this field is not used, you can enter what you want as long as it's a valid email address), for example admin@domain.tld
- Organization, Department, Locality, State and Country fields should have the values you entered when you have created your PKI. You can let those values.
- Password: This field must be blank. Remember that OpenVPN daemon starts without human intervention when the server boots, so it need to have access to the certificate key without being prompted for a password.
- Certificate life: How-long the certificate will be valid. Enter what you want, but remember, when the certificate expires, you'll have to create another one, and update it in OpenVPN Bridge panel.
- Key size: you can enter what you want (I use 2048 in general). The bigger, the stronger, but will use a bit more CPU power when the session key is negotiated (at the connection, and once an hour)
- Certificate Use: you should use "VPN Server Only". This is important. If you don't choose this type of certificates, clients may be unable to connect, or you may be unable to proceed as some other certificate uses won't allow an empty password.
Here's an example:
Now, confirm you want to create this certificate:
Configure OpenVPN with the newly created certificates
Now, you can configure OpenVPN with your certificates. Go in the server-manager->OpenVPN-Bridge->certificates configuration.
Here you have some fields to setup:
- URL to update the CRL: you should let the default: http://localhost:940/phpki/index.php?stage=dl_crl_pem unless PHPki is installed on another server (or if you use another PKI tool)
- CA certificate: You should put here the Root certificate in PEM format. You can get it in PHPki, by clicking on the link "Display the Root Certificate (PEM Encoded)" Copy and paste this data into the "CA certificate" box.
- Server certificate: You should put here the certificate of the server. You can get it in PHPki, manage certificates, click on the download link corresponding to the certificate you have created for the server ("openvpn-bridge" in the example), choose PEM certificate in the drop-down menu, download it. You can open this file with a text editor. Copy and paste this text into the "Server certificate" window.
- Server private key: This is the private key associated with the server's certificate. To get it, follow the same steps as above, but choose "PEM Key" in the drop-down menu instead of "PEM Certificate" and paste the text into the "Server private key" window.
- DH Parameters: To get the DH Parameters, click on the "Display the Diffie-Hellman parameters" link in PHPki and paste the text into the "DH parameters" window.
- Static Key: This is optional. You can get it using the "Display the static pre-shared key" link in PHPki. Note that if you enter this key on the server, you'll have to deploy it on each client.
You can now submit the request. "Certificates are ready" should be displayed.
Here's an example:
Upgrade from smeserver-openvpn-bridge-fws-1.1-2
If you was using the previous version of the contrib, follow this part. It will migrate the certificate configuration from the previous installation.
Install the PHPki contrib
First, you'll have to install PHPki. Be sure to follow the migration step
Install the latest OpenVPN contrib
yum --enablerepo=smecontribs install smeserver-openvpn-bridge
You can configure the bridge-interface contrib now. You can follow this how-to
Migrate previous/existing OpenVPN Server certificates
Now, you should install the old certificates in the new location For this, you can use this script:
#!/bin/bash
# Store the actual time in $TIME
TIME=$(date +%d%m%Y%H%M%S)
OPENSSL=/usr/bin/openssl
OLDDIR=/etc/openvpn/easy-rsa/keys/bridge/
OVPNNEWDIR=/etc/openvpn/bridge
SRVCN=$(db configuration getprop openvpn-bridge localCN)
convert_cert_to_rule_entries(){
DBNAME='openvpn-bridge'
# The new OpenVPN contrib doesn't use cert entries but rules ones
# So we need to convert it
if [ -e /home/e-smith/db/$DBNAME ]; then
mv /home/e-smith/db/$DBNAME /home/e-smith/db/$DBNAME.$TIME
for CERT in $(/sbin/e-smith/db $DBNAME.$TIME keys); do
# If the entry is a cert and cert-type=client
if [ $(/sbin/e-smith/db $DBNAME.$TIME gettype $CERT) == 'cert' ]&&[ $(/sbin/e-smith/db $DBNAME.$TIME getprop $CERT cert-type) == 'client' ]; then
COM=$(/sbin/e-smith/db $DBNAME.$TIME getprop $CERT comment)
REDIR=$(/sbin/e-smith/db $DBNAME.$TIME getprop $CERT redirectGW)
IP=$(/sbin/e-smith/db $DBNAME.$TIME getprop $CERT ip)
# Blank out the IP if defined as 'undef'
if [ $IP == 'undef' ]; then
IP=
fi
/sbin/e-smith/db $DBNAME set $CERT rule comment "$COM" redirectGW "$REDIR" ip "$IP"
fi
done
fi
}
install_cert_in_new_dir(){
# Here, we install the old certificates used by OpenVPN daemon to the new location
mkdir -p $OVPNNEWDIR/{priv,pub}
cat $OLDDIR/$SRVCN.crt > $OVPNNEWDIR/pub/cert.pem
cat $OLDDIR/$SRVCN.key > $OVPNNEWDIR/priv/key.pem
cat $OLDDIR/dh.pem > $OVPNNEWDIR/pub/dh.pem
cat $OLDDIR/ca.crt > $OVPNNEWDIR/pub/cacert.pem
cat $OLDDIR/ta.key > $OVPNNEWDIR/priv/takey.pem
cat $OLDDIR/crl.pem > $OVPNNEWDIR/pub/cacrl.pem
}
perms(){
# Restrict access
chown -R root:root $OVPNNEWDIR
chmod -R o-rwx $OVPNNEWDIR/priv
}
convert_cert_to_rule_entries
install_cert_in_new_dir
perms
Save this script and run it as root.
Configuration rules
The configuration rules is the new way to apply specific configuration to a client. As now the certificates are managed separately, you have to create rules separately. It's still quite simple, just add a new rule, enter the common name to match, a comment, choose an optional fixed IP, choose to enable/disable the gateway redirection, or even block a specific client. Then save, and you're done.
Client Configuration
OpenVPN runs on most platforms. In any case, the first step will always be the same: you have to create a new certificate for the client.
Create the certificate with PHPki
If you use your own PKI tool, you should be able to do it yourself ;) If you use PHPki, here are the steps to follow
- In PHPki administrative interface, click on the "Create a new certificate" link.
Here, you'll have to enter several informations. Most of them are up to you. Here's an example:
Once you have submitted this form, you'll have a confirmation page. Then your certificate will be ready.
Now, go in the "Manage Certificates" menu in PHPki and click on the Download link corresponding to your certificate, then choose the PKCS#12 bundle format (OpenVPN also accept pem encoded certificate, but the PKCS#12 bundle has the advantage of combining the CA, the certificate and the key in one file).
If you have configured and shared secret key on the server, you also need to download it.
Windows
For Windows systems, you should download the OpenVPN GUI stable release 2.4.4 from https://openvpn.net/index.php/download/community-downloads.html. OpenVPN includes the Windows GUI in the installer.
On Windows, the configuration directory for OpenVPN is C:\Program Files\OpenVPN\config Here you can put all the needed files, or create sub-directories if you want to configure several connexions. Put here (either in the config directory or in a sub folder) the PKCS#12 file you have downloaded earlier, and the shared secret key if you used one on the server. Now create a text file, and change the extension to be .ovpn (the name isn't important). Edit it with your favorite text editor. Now, go in the panel of OpenVPN-Bridge and click on the link "Display a functional client configuration file". Copy and past this in your config file (.ovpn), and just change the pkcs12 directive to match your certificate name. Save this file. Now your client should be able to connect with the OpenVPN GUI.
Linux with Network Manager
You can see french page for Debian.
Ubuntu 12.10 64bit
(Not tested in 32bit but will most likely work) If possible follow the above windows tutorial first to test that you have configured openvpn correctly for server and client.
- Install openvpn for network manager
sudo apt-get install network-manager-openvpn
Under Ubuntu 16.04 64bit, we also needed to install "network-manager-openvpn-gnome":
sudo apt-get install network-manager-openvpn-gnome
- Create folder called e.g. "openvpn" (can be anything) in your home directory (could be any directory).
- Assuming that phpki is being used. In browser go to server-manager panel > certificate management and download the relevant client's "PCKS#12 Bundle" and place it in the "openvpn" folder.
- Go to server-manager panel > openvpn-bridge click on "Display a functional client configuration file". Copy and paste this into a text editor and save with .ovpn extension into the "openvpn" folder. Make sure user.p12 is replaced with the name of the .p12 (PCKS#12 Bundle) client file downloaded previously. Also check that the remote (gateway) is the correct server url.
- In ubuntu go to Network Manager > VPN Connections > Configure VPN. Click import then in the explorer navigate to the openvpn folder in the home directory and select the .ovpn file created previously. This should automatically load all settings into network manager.
- Add username and password of client, then you have to give the path of the user.p12 key of your user and set the Private key password (the password set during the certificate creation in phpki).
- After that you have to select the 'advanced' panel and go to 'TLS authentication'. Enable the use of TLS authentication, give the path or your takey.pem and select the key direction to 1. (if needed)
- As a note, when connected successfully to the vpn, browsing the internet may not work in tandem, therefore go to ipv4 settings tab when editing the vpn connection. Click on "Routes" and check "Use this connection only for resources on its network". Also try adding 8.8.4.4 to "Additional DNS Servers" (This is google's dns servers).
Fedora 16 / 17 64bit
(Not tested in 32bit but will most likely work)
Note: server set as user/pass + certificate
- Install openvpn for network manager
yum install NetworkManager-openvpn
manual settings
- Assuming that phpki is being used. In browser go to server-manger panel > certificate management and download the relevant client's "PCKS#12 Bundle" and place it into one convenient folder.
- go to yournuserame > System Settings > Network click on little + sign on bottom left
- in the new pop-up window select VPN then push Create
- select OpenVPN and push Create
- select password with certificate (or any other method you set on server)
- put credentials for user and private key password
- set the gateway as your server.domain.tld
- at advanced check Use LZO data compression
- at advanced check Use a TAP device
- at TLS authentication, give the path of the takey.pem and enable it with the direction 1 (if needed)
- click on the small folder near the first certificate and go to the bundle certificate downloaded into convenient folder - all certificates should be filled up
- Note: I recommend to check also in IPv4 > route Use this connection only for resources on its network"
- save and test
import settings
- Create folder called e.g. ".openVPN" (can be anything) in your home directory (could be any directory).
- Assuming that phpki is being used. In browser go to server-manger panel > certificate management and download the relevant client's "PCKS#12 Bundle" and place it in the ".openVPN" folder.
- Go to server-manager panel > openvpn-bridge click on "Display a functional client configuration file". Copy and paste this into a text editor and save with .ovpn extension into the "openVPN" folder (the name of the file will be the visible name in network manager to select VPN connection). Make sure user.p12 is replaced with the name of the .p12 (PCKS#12 Bundle) client file downloaded previously. Also check that the remote (gateway) is the correct server url.
- In fedora ALT+F2 enter nm-connection-editor and ENTER
- go to Network Connections > VPN . Click Import then in the explorer navigate to the openvpn folder in the home directory and select the .ovpn file created previously. This should automatically load all settings into network manager.
- Add username and password of client. Private key password which could differ from the user pass (and will not change if user/admin will change user password in server-manager or server-user. it is the password set during the certificate creation). Now give also the path of certificate user.p12
- at Advanced/TLS authentication, give the path of the takey.pem and enable it with the direction 1 (if needed)
- Note: I recommend to check also in IPv4 > route Use this connection only for resources on its network (unless you use the "Redirect Gateway" functionality)
- save and test
Fedora 19 64bit
(Not tested in 32bit but will most likely work)
the import feature apparently does not work
also the ""bundle" does not work
you'll need to
- Assuming that phpki is being used. In browser go to server-manager panel > certificate management and download the relevant client's cacert.pem user.pem user-key.pem and place them into one convenient place.
- go to yournuserame > System Settings > Network click on little + sign on bottom left
- in the new pop-up window select VPN then push Create
- select OpenVPN and push Create
- select password with certificate (or any other method you set on server)
- put credentials for user and private key password
- set the gateway as your server.domain.tld
- at advanced check Use LZO data compression
- at advanced check Use a TAP device
- click on the small folder near the first certificate and go to the user.pem certificate downloaded into convenient folder
- click on the small folder near the second certificate and go to the cacert.pem certificate downloaded into convenient folder
- click on the small folder near the third certificate and go to the user-key.pem certificate downloaded into convenient folder
- Note: I recommend to check also in IPv4 > route Use this connection only for resources on its network"
- save and test
Linux
Mac OS X
OpenVPN works great with Tunnelblick.
Download the PKCS#12 file to a convenient location. In that same location, create a text file using TextEdit or any other text editor. Name it anything you choose, with a file extension of .ovpn (for example, user.ovpn). Now, go in the panel of OpenVPN-Bridge and click on the link "Display a functional client configuration file". Copy and paste this into your config file (.ovpn), and change the pkcs12 directive to match your certificate name, like this:
pkcs12 user.p12
If you want to be able to connect to the VPN server without entering a username and password, comment out the line that says "auth-user-pass", like this:
#auth-user-pass
Save the .ovpn file, then double-click on it. This will open Tunnelblick and import your configuration. You can then use the Tunnelblick menu to connect to your server.
iOS
if you plan to connect to Open vpn you can either jailbreak and use GuizmoVPN.
Otherwise you could use the newly available OpenVPN app. However it does not have any tun driver and it needs a server configuration to work :
mkdir -p /etc/e-smith/templates-custom/etc/openvpn/bridge/openvpn.conf/ echo 'push "topology subnet"' >/etc/e-smith/templates-custom/etc/openvpn/bridge/openvpn.conf/66topology expand-template /etc/openvpn/bridge/openvpn.conf service openvpn-bridge restart
Android
You cannot use TAP mode, and therefore openvpn-bridge, with Android.
Please read this for more:
https://openvpn.net/faq/why-does-the-app-not-support-tap-style-tunnels/
You can use openvpn-routed:
https://wiki.contribs.org/OpenVPN_Routed
Advanced configuration
Some advanced options are not presented in the panel. The goal was to keep the panel as simple as possible as most installations won't need to change advanced settings. But advanced options are still available with some DB keys:
- ConfigRequired: (enabled|disabled). If set to enable, clients will be rejected unless a configuration rule match the common name of their certificate. This can be useful if you use just one CA to sign a lot of different certificates, but only want a limited number of certificates to connect to the VPN
- UDPPort: (number) Change the port the server listen to when running in UDP mode
- TCPPort: (number) Change the port the server listen to when running in TCP mode
- access: (private|public) you should let this to public as running a VPN server just for the local network make no sens
- cipher: (valid cipher name) You can force the cipher to use. Starting SME 10, default is AES-128-CBC . If you put auto ( or delete this key, for SME9 and before ) the default will be the current of openvpn wich is as per 2.4 : BF-CBC. Also when both client and server are at least version 2.4, they will negotiate the stronger cipher both side support. SME10 enforce the following authorized ciphers: --ncp-ciphers AES-256-GCM:AES-128-GCM:AES-256-CBC:AES-128-CBC:BF-CBC . To have the list of the supported cipher, issue the command
openvpn --show-ciphers
- clientToClient: (enabled|disabled) If you want to prevent two clients to communicate, you should enable this option
- duplicateCN: (enabled|disabled) If you want to allow several clients to connect simultaneously using the same certificate, you need to enable this option (default is disabled)
- compLzo: (enabled|disabled) This option control the usage of real time LZO compression. Enabling it usually improve the performance at no cost. It uses an adaptive algorithm, if data sent over the tunnel are uncompress-able, the compression will automatically be disabled. You may want to disable it on small hardware.
- management: (<ip to bind to>:<port>:<password>) this key control the management interface of OpenVPN. The default is to listen only on the loopback interface. It's used to display connected clients. You can allow the access on the local network to get some more statistics using for example: http://www.mertech.com.au/mertech-products-openvpnusermanager.aspx
- maxClients: (number) maximum number of clients connected at a time
- mtuTest: (enabled|disabled) When using UDP as transport protocol, mtu-test will measure the best MTU for the virtual interface. You should let it enabled unless you know what you're doing
- protocol: (udp|tcp) The transport protocol to use. UDP is recommended for both security and performance, but there are situations where you'll need to use TCP. If you use TCP, you should set TCPPort directive to set the port the daemon will listen on (instead of UDPPort)
- redirectGW: (perClient|always) The default is to enable the gateway redirection on a per client basis. But if you want the redirection to be always enabled, you can set this key to "always". This way, you won't have to create a new rule for each client.
- tapIf: (tap interface) use this tap interface. You should use a free tap interface enslaved in the bridge interface (configured with the bridge-interface contrib). Do not change this setting unless you know what you're doing
Also you can also set the property PushRoute "disabled" to any network in networks db to avoid the contrib to push the network to the client.
Once you have configured the service like you want, just run the command
signal-event openvpn-bridge-update
Uninstall
To remove the contrib, just run:
yum remove smeserver-openvpn-bridge
You may also want to remove some other dependencies if you don't use them anymore
yum remove smeserver-phpki phpki smeserver-bridge-interface perl-Net-OpenVPN-Manage perl-Net-Telnet
Notes
OpenVPN and SME installed in virtual machine - VMWare promiscuous mode
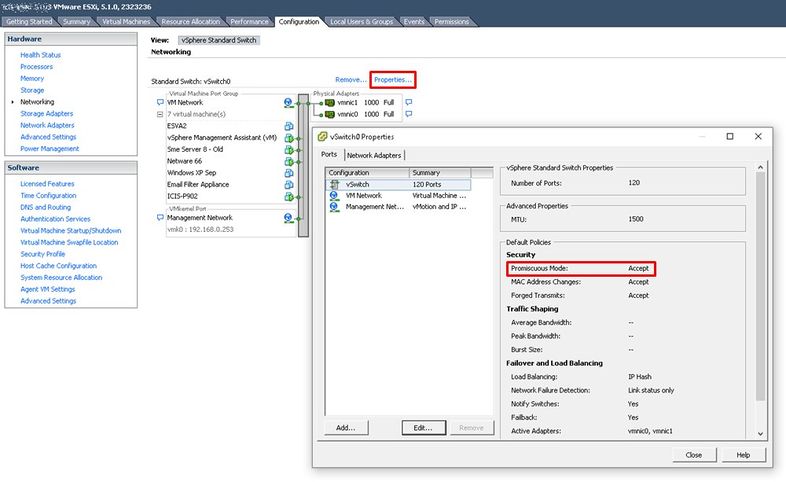
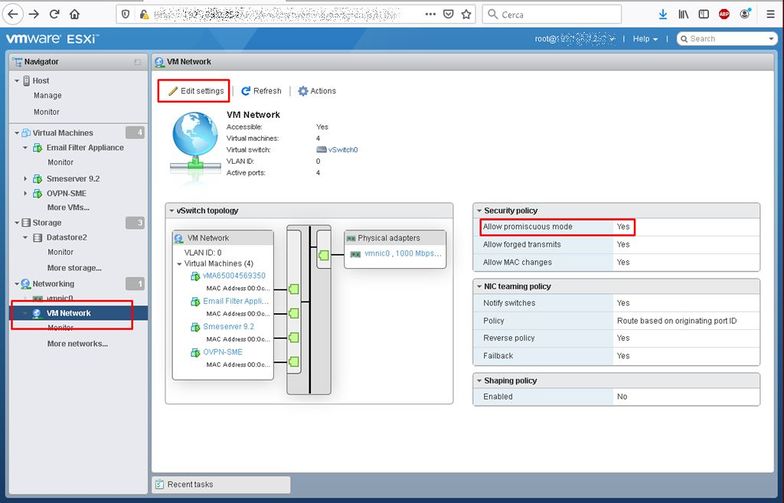
By default for all version of ESX(i) starting from 3.5 to 7.0 (current in february 2020) VMWare rejects packets in promiscuous mode on the vSwitch, which will cause trouble with OpenVPN in bridge mode. The main symptom is that after successful authentication from your remote client you can ping/reach only the OpenVPN server while any other ip address on the LAN can't be pinged/reached. To correct this in VMWare set:
Configuration > Networking > your vSwitch: Properties > Ports-tab > vSwitch > Edit > Security-tab > Promiscuous mode: accept
For ESXI hypervisor still working with vSphere client:
For ESXI greater than 6.5 using webui client:
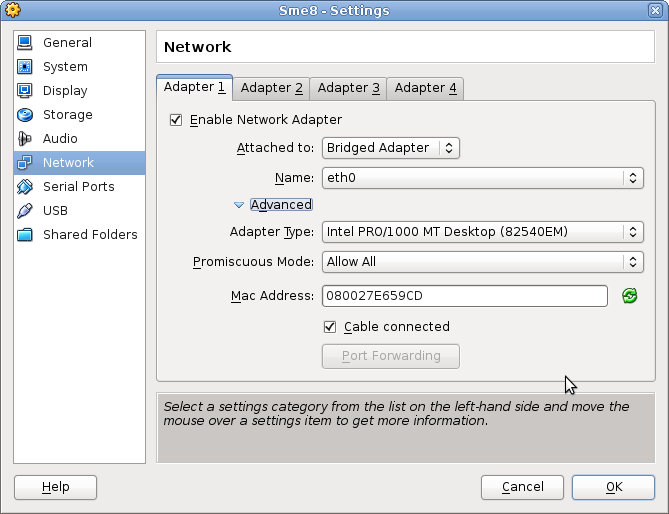
OpenVPN and SME installed in virtual machine - Virtualbox promiscuous mode
There is the same thing in virtualbox, you need to give the argument "allow all" in the network tab configuration.
virtual machine > configuration > network > adapter 1
choose adapter type "intel pro 1000....."
then put attached to on "bridged adapter" on your default NIC
click on advanced
then put promiscuous mode on "allow all"
OpenVPN and SME installed in virtual machine - Other hypervisors
It's documented that you can experience such problems in other hypervisors like OVirt, Proxmox, XEN or others. Keep in mind to search for equivalent settings concerning "promiscuous mode" of vSwitch.
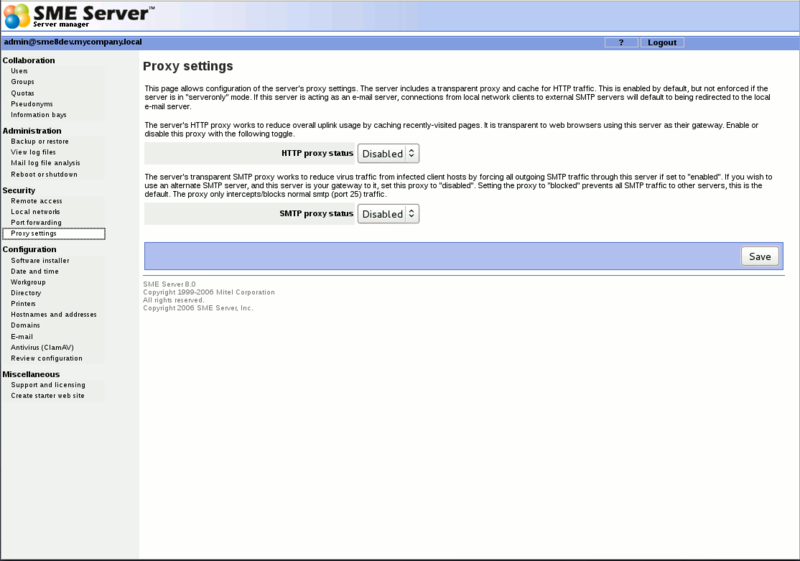
Transparent proxy settings
go to the server-manager>Proxy services and disabled http and smtp proxy
Workarounds and known issues
if you migrate from SME8 to SME9 and are not able to connect after correctly migrating your certificates, this might be related to not secure enough algorithm. CentOS 6.9 release notes state that "Support for insecure cryptographic protocols and algorithms has been dropped. This affects usage of MD5, SHA0, RC4 and DH parameters shorter than 1024 bits." Of course real solution would be to migrate all your certs to better algorithm.
workaround :
1echo -e "LegacySigningMDs md2 md5\nMinimumDHBits 512\n" >> /etc/pki/tls/legacy-settings
2service openvpn-bridge restart
Bugs
Please raise bugs under the SME-Contribs section in bugzilla and select the smeserver-openvpn-bridge component or use this link
| ID | Product | Version | Status | Summary (6 tasks) ⇒ |
|---|---|---|---|---|
| 12500 | SME Contribs | 10.0 | CONFIRMED | update default config file |
| 12437 | SME Contribs | 10.0 | CONFIRMED | initial install unable to connect after configuration |
| 12435 | SME Contribs | 10.0 | CONFIRMED | failure to download crl |
| 10914 | SME Contribs | 9.2 | UNCONFIRMED | OpenVPN kicking connections generate an error and does not disconnect |
| 10913 | SME Contribs | 9.2 | UNCONFIRMED | OpenVPN connections status showing time in non-human readable format |
| 6914 | SME Contribs | 8.0 | UNCONFIRMED | Can not access internet after switch serveronly to servergateway and back again |
Changelog
Only versions released in smecontrib are listed here.
2022/11/23 Jean-Philippe Pialasse 2.1-22.sme
- log to dedicated file [SME: 12242]
- apply locale 2022-11-1 patch
- add Provides perl(esmith::FormMagick::Panel::openvpnbridge)
- Re-build and link to latest devtools [SME: 11997]
- add to core backup [SME: 12018]
Other articles in this category
Ipsec, Libreswan, Libreswan-xl2tpd, OpenVPN, OpenVPN Bridge, OpenVPN Bridge/fr, OpenVPN Routed, OpenVPN SiteToSite, SME Server wishlist, SoftEther VPN, Softethervpn-server, VPN, Wireguard