Email - Setting up E-mail clients for SME 8.0
Why This Is Needed
From SME 8.0beta6 onwards, unauthorised access to SMTP on Port 25 has been prevented, by design, even for users in the local network, and replaced with SSL-authorised access on Port 25. The result is that setting-up clients to successfully authorise against SME-Server SMTP has become a little complicated. This Howto is intended to give step-by-step instructions using Microsoft Outlook 2010 as an example. The same procedures should apply to most Email Clients, although the locations of the settings may vary.
Thanks
This Howto could not have been written without the help and advice of 'byte.' He doesn't identify himself in his profile in the forums, but he is owed a pint or two next time he hits rural Suffolk!
Assumptions
This Howto has been tested on systems where the SME server is used as the outgoing SMTP server for the network (ie directly connects to other Internet mail servers), & on systems with a Smarthost configured (ie SME server SMTP mail server sends mail via the ISPs mail server). The fundamental principle is to allow clients to authorise to the SME Server before mail is accepted for transmission.
Things to do in the Server Manager
Configure Common Name for self signed Certificate
With secure connections being made to the SME server for mail & browsing, the domain name presented on the security certificate can cause some devices/users not to allow the connection when presented with "scary" warning messages.
To avoid this, SME server can be configured to present a security certificate to users & devices that matches the real world domain name. It is good practice to change the CommonName setting for the SSL certificate rather than use the default servername.domain.com. The default servername.domain.com does not resolve correctly when used in mail client devices that are external to the LAN, so a better choice is to configure all mail clients, whether they are internal or external, to use the same mail server format of www.mymaindomain.com. These settings allow mobile users to use their devices internally on the LAN or externally without needing to change configuration settings in the devices
Login to the command prompt aa root user or user with root privileges. Issue the following comamnds, where the domain name you use is the main domain name configured in the admin Console, "Configure this server" option eg www.mymaindomain.com
config setprop modSSL CommonName www.mymaindomainname.com expand-template /home/e-smith/ssl.key/key expand-template /home/e-smith/ssl.crt/crt signal-event post-upgrade signal-event reboot
Allow SSMTP
Login to the server manager at http://your_server_address/server-manager and click on the menu item Email. Then click the button labelled 'Change e-mail reception settings.'
Change 'SMTP authentication' to 'Allow both SMTP and SSMTP' and save the new settings.
Things to do in Outlook
Make sure the Fully Qualified Server Name is used
Make sure you change the Common Name setting for the Certificate (as detailed above). This is necessary so that the SME Server's self-signed security certificate uses a name that is legitimate for both internal clients & external clients (LAN & WAN). Servers described by IP addresses will cause Outlook to require that the certificate be accepted again every time the program is restarted and will play havoc with automatic email use. The FQDN should be the publicly accessible domain name for your server eg www.domain.com.
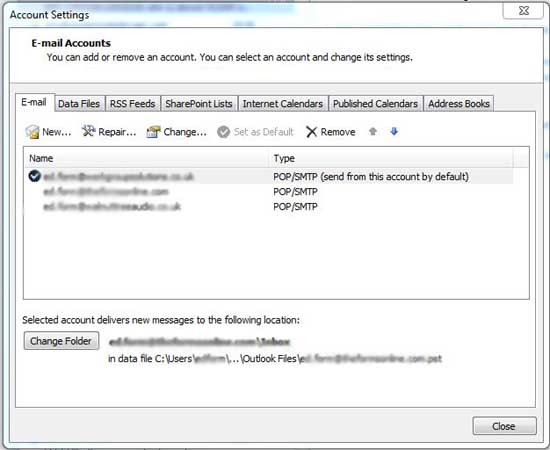
Click 'File' then 'Account Settings' and then the drop-down 'Account Settings' button.
In the 'Account Setings' dialogue, highlight an email account and click the small 'Change' button above.
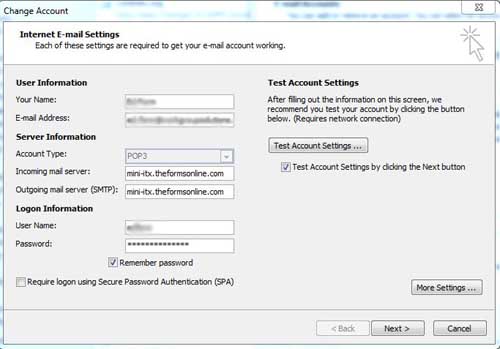
In the first page of the dialogue that results, make sure that both incoming and outgoing servers are entered as the fully qualified name of your server. Recommended good practice is to use the form - 'www.mymaindomainname.com' [ or .co.uk, .org etc.] and will be as shown in the Server Manager Review Configuration screen, towards the bottom of server manager. It is no longer recommended to use servername.domain.com, as that causes problems on clients used externally, whereas www.domain.com will work satisfactorily in all cases.
The Change Account dialogue is shown below with the fully qualified server name in both incoming and outgoing server settings. The Incoming & Outgoing server settings shown in the following screen image, should be changed to www.theformsonline.com. When a new image is available this document will be updated.
Set encryption and authorisation parameters
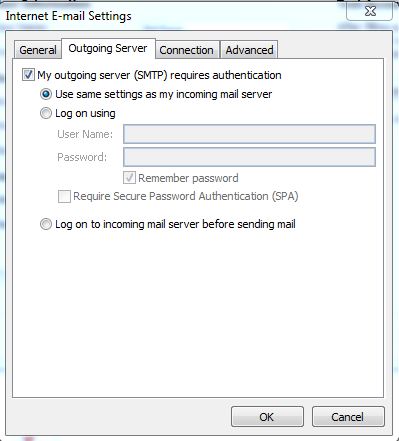
Now take the tick out of the 'Test Account Settings by clicking the Next button' item on this page and click 'More Settings.' Then click the 'Outgoing Server' tab in the resulting dialogue and make it look like the figure below.
Some later versions of Outlook do not allow you to disable the 'Test Account settings'. In this case you need to temporarily turn off the header checks in the smeserver in order that the test email is accepted. This message in the forums has the details of what you should do: http://forums.contribs.org/index.php/topic,50838.msg256671.html#msg256671
Current recommended good practice is to use secure connections eg typically on port 465 (secure SMTP), port 993 (secure IMAP) & port 995 (secure POP), although some situations & protocols require different ports eg 587. Current recommended good practice is to configure email clients to use secure SMTP & secure IMAP, so that users can access their mail from any device (mobile phone, tablet, notebook, desktop etc), anywhere (LAN or WAN), & all changes made on one device will update the mail server, so when using another device the same changes are seen. Use of the POP mail protocol has severely declined with the advent of mobile devices.
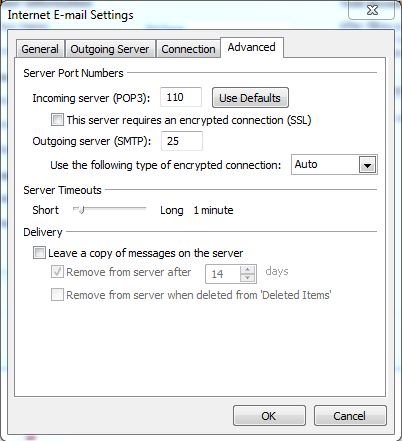
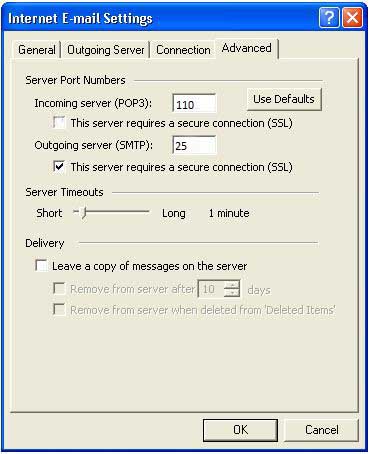
Now click the Advanced tab and change the settings for the Outgoing Server to those shown below - ie Incoming server (POP3) Port 995, Outgoing server Port 465, & if IMAP is being used Incoming server (IMAPS) Port 993, and Auto encryption - and save the settings with 'OK,' 'Next,' 'Finish' and 'Close.' Then shut Outlook down. When a new screen image is available this document will be updated.
Encryption Settings in Older versions of Outlook
Versions of Microsoft Outlook from 2003 and earlier do not have the multiple-choice dropdown for encryption type; instead they have a single tick-box labelled 'This server requires a secure connection (SSL),' Put a tick in the box, as shown below, and it will work perfectly. The following screen image is to be updated to show secure ports, when a new image is available.
Thats all of the settings done. Now you have to link Outlook to your server's self-issued security certificate.
A Question of Security
What to do about your Security Certificate
A workaround to enter the self signed security certifcate onto your client, is to open a browser, in this case as the email client Outlook is a Microsoft product, then open Microsoft Internet Explorer (or equivalent MS browser) & go to https://www.yourmaindomainname.com & accept the certificate for the first time. The certificate is entered into the trusted store & during further use you will not be challenged for an untrusted certificate. There are a lot of changes currently happening with Microsoft operating systems etc, & browsers are changing, so this workaround may no longer apply on newer systems. Obviously when using other mail clients eg Thunderbird, then follow appropriate instructions.
For Outlook, use the following instructions where necessary.
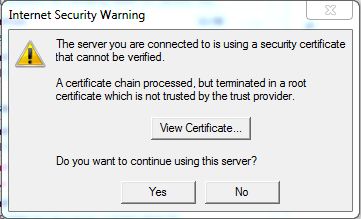
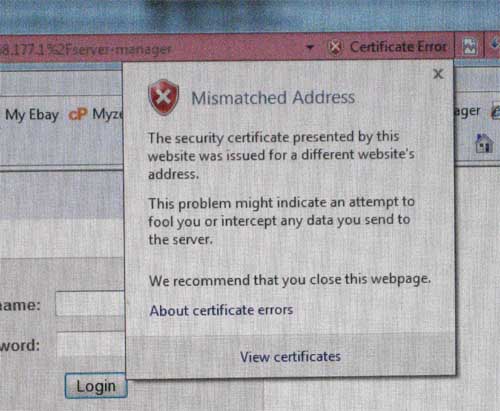
The next time you start Outlook, compose a new email and run 'Send and Receive,' Outlook will ask you whether you are happy to use the server: the dialogue is shown below...
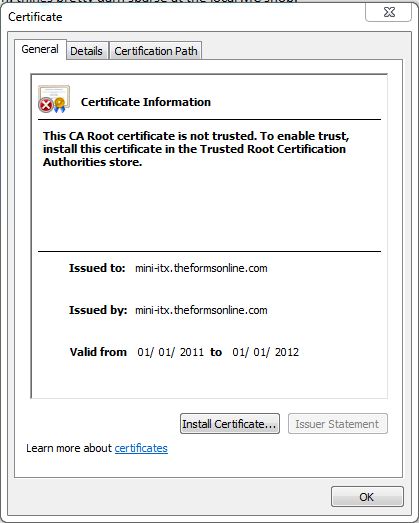
Click 'View Certificate' and a Window like this will appear... Note that the screen image to be updated, should show www.theformsonline.com
Note that the fully qualified server name appears twice.
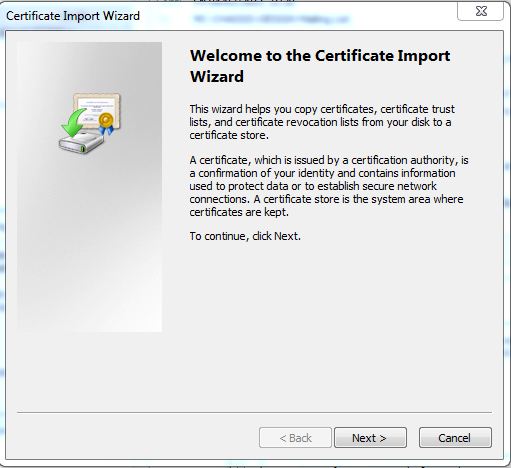
Click 'Install Certificate' to get this dialogue...
Click 'Next' and you will see...
Don't change any settings. Just click 'Next' - it gives this dialogue...
Click 'Finish' to go to this result... Note that the screen image to be updated, should show www.theformsonline.com
And tell it you want to do it anyway by clicking 'yes,' which will install the certificate and report the result...
At this stage the 'Do you want to use this server' dialogue may have timed out and given you a send-failure notice. Not to worry! Just hit 'Send and receive' again [F9], and say 'Yes' to the 'Do you want to use this server' question.
That's it! Outlook can now authenticate itself to your SME SMTP Server and send emails.
Older versions of Outlook and Certificates
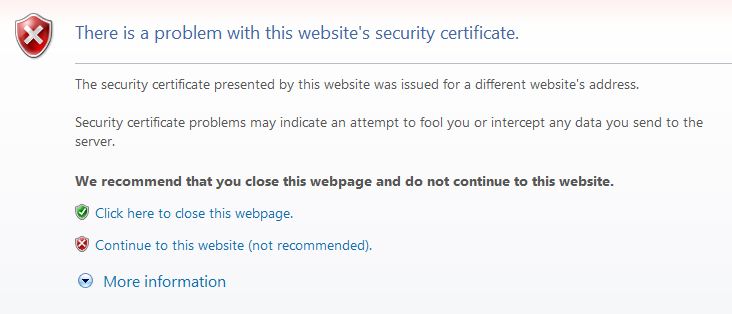
Older versions of Microsoft Outlook - 2003 and earlier - do not have the ability to install certificates, so you will only see a 'Do you want to use this server' query and would have to answer it every time you try to send email after restarting the program. To get round this you need to install the certificate directly into Internet Explorer because it is the certificate routine from IE that is used by Outlook. To do this: open Internet Explorer and type in the URL for your server manager - https://www.mymaindomainname.com/server-manager [in this case https://www.theformsonline.com/server-manager]. This will give a security challenge screen...
Click 'Continue to this website (not recommended).' and you will reach the Server Manager login screen. The address bar at the top of this window will be pink coloured, with a notice button at the right hand end saying 'Certificate error.'
Click it and you will see a very similar certificate installation routine to the one described in Section 6.1, 'What to do about your Security Certificate,'
above - the dialogues look a little different but they follow exactly the same sequence.
Windows 10 and Self-Signed Certificates
Windows 10 Mail gives this error connecting to a SME server using a self-signed certificate:
Security Certificate on the server is not valid. Error 0x80072F0D
Additionaly, Internet Explorer, Edge, and Chrome will require users to bypass a security warning every time they browse to your server.
To eliminate these errors you must install your server's certificate into each workstation's 'Trusted Root Certification Authorities' certificate store. Even then, users will continue to receive security warnings if they access your server using a name or address that differs from the CommonName used in the certificate itself.
To install a certificate in Windows 10:
Start the Certificate Import Wizard
- Open Internet Explorer (Edge does not offer the option to install certificates)
- Browse to any secure url on your SME server - eg https://your.smeserver.tld/webmail
- Select Continue to this website (not recommended)
- Click on Certificate error in the Internet Explorer address bar and select 'View certificates'
- Click Install Certificate
IMPORTANT:
My stand-alone Windows 10 workstation required the extra steps below. My domain-connected Windows 10 workstation did not.
If Install Certificate is not available, close Internet Explorer and restart the process using Run as administrator
- Click the Windows Button
- Type iexplore (don't press enter!)
- Right-click on Internet Explorer in the search results and select Run as administrator
Certificate Import Wizard
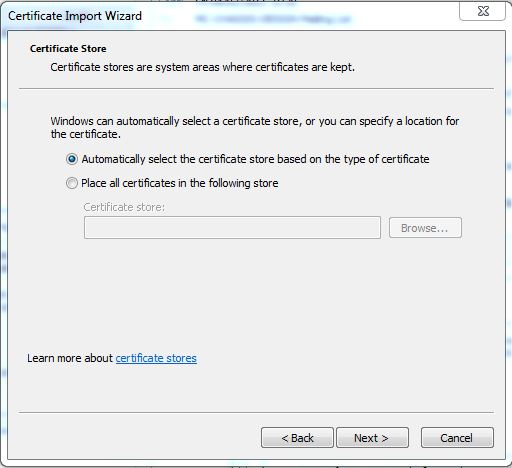
- Select Local Machine (the default is "Current User") and click Next
- Select Place all certificates in the following store (the default is "Automatically select...")
- Click Browse and select Trusted Root Certification Authorities
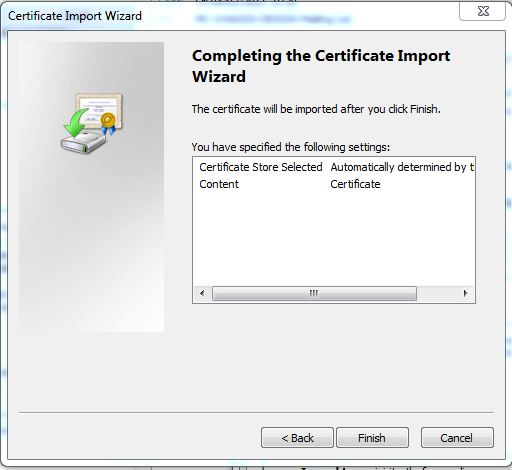
- Click Next
- Click Finish
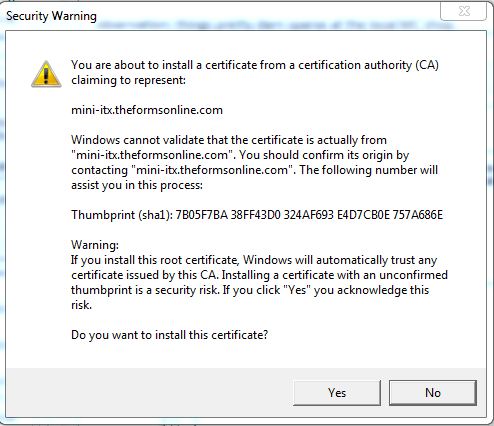
- You will get a Security Warning saying "Windows cannot validate that the certificate is actually from...". Click Yes
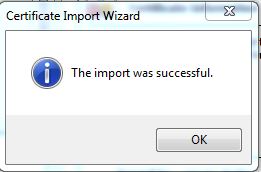
- You should get a message saying "The import was successful". Click OK
- Click OK to close the Certificate window.
Certificate name mis-match
If the server name stored in your certificate (self-signed or otherwise) does not match the name or IP address that your device uses to access the server, you will still get certificate name mis-match errors.
Edge & Internet Explorer will allow users to access the site, but will display a red "Certificate error" message. Chrome will still require users to click "Advanced", and "Proceed to ... (unsafe)"
Email clients usually require an extra confirmation that it's OK to use the mis-matched certificate:
- Windows 10 Mail
- Click on the error icon (a triangle with an exclamation mark) next to your account name
- Select Proceed
- Outlook
- Untested.
- Former Windows/Outlook combinations required you to accept the certificate mis-match every time outlook starts.
Testing
If you have successfully imported your certificate and if the the CommonName of your certificate matches the hostname you are using to access your server, users should get a secure connection indicator from software that uses the Windows certificate store:
- Microsoft Internet Explorer: grey padlock at the right of the address bar
- Microsoft Edge: padlock at the left of the address bar
- Chrome: Green padlock + green "https:" at the left of the address bar
- Windows 10 Mail: no error messages
- Windows 10 / Outlook 2010: no warnings or errors
(Firefox uses its own certificate store, and won't accept your certificate until you have added it there, too.)
Other Domains
Repeat as required
If you have more than one domain on your server, with accounts set up in Outlook, you will need to change the settings shown in 'Section 5,' 'Things to do in Outlook,' for each of them.
Things to Follow-Up
Self-signed certificates have dates incorporated. Does this mean that the installation of the Security Certificate will need to be repeated annually? If so it's a pain, especially for administrators with a lot of workstations to look after.
Perhaps it would be better for SME Server to switch to Port 587 transmission, which the is the recommended port in the SMTP standards and does not require client installation of certificates in order to function.
Disable encryption/authentication of mail when relaying
Bugzilla: 6523, Bugzilla:6522
Change the configuration of the system from the default, so that it no longer requires encryption/authentication before allowing relaying of mail.
config setprop qpsmtpd RelayRequiresAuth disabled signal-event email-update
Configuring Thunderbird clients
Here are the basic abbreviated configuration settings you need for Thunderbird, refer
http://forums.contribs.org/index.php/topic,50554.msg254632.html#msg254632
& numerous other forum posts for additional details
Setting up IMAP accounts in Thunderbird works satisfactorily (as of December 2013), using the following generic procedure:
Configure SME server CommonName setting for Certificate in the form of www.mymaindomainname.com
Use manual setup (instead of automatic)
Specify Connection Security = SSL/TLS
Specify the SSL ports ie IMAPS = 993, SMTPS = 465 (instead of relying on TLS for correct settings)
Specify authentication method = Normal Password
At some point accept the server's self-signed certificate. Make sure you previously configured the CommonName setting for the certificate, see the section "Configure Common Name for self signed Certificate" at start of this article.