SME Server talk:Documentation:Administration Manual:Chapter11/fr
Sécurité
Accés à distance
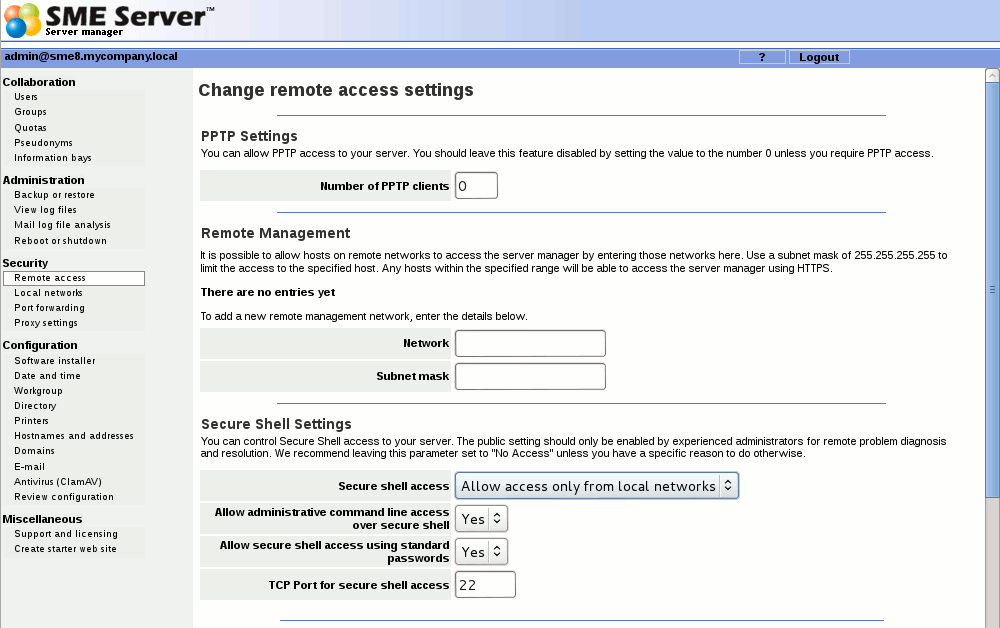
Si vous êtes un utilisateur avancé, le SME Server fournie plusieurs façons différentes d'accéder au système d'exploitation Linux, soit à partir d'un ordinateur de votre réseau interne ou depuis un ordinateur en dehors de votre entreprise, à partir d'Internet. En outre, vous avez la possibilité d'accéder à votre réseau informatique en toute sécurité à partir d'un ordinateur distant. Toutes ces opérations sont configurés à partir de l'écran ci-dessous dans le gestionnaire de serveur.
Chacune de ces méthodes d'accès distant est décrite ci-dessous.
PPTP (VPN)
Le Point-to-Point Tunnelling Protocol (PPTP) est utilisé pour créer des connections des clients vers le serveur par des réseaux privés virtuels (VPN) et a été développé par le Forum PPTP, un groupe d'industriels qui comprenait Microsoft et plusieurs autres sociétés. Un VPN est un réseau privé d'ordinateurs qui utilise l'Internet pour se connecter à des nœuds. PPTP permet aux utilisateurs de se connecter à leurs réseaux d'entreprise au travers d'Internet.
L'implémentation de PPTP par Microsoft est largement utilisé dans le monde de Windows pour fournir un accès à distance à travers l'Internet. Si vous avez un système Windows distant (par exemple, un ordinateur portable ou un ordinateur à la maison) qui a accès à Internet, vous pouvez également accéder aux informations stockées sur le serveur de votre entreprise.
Si vous souhaitez activer l'accès VPN, vous devez décider combien de clients PPTP individuels seront autorisé à se connecter simultanément à votre serveur, et entrez le nombre ici. La méthode la plus simple est d'entrer le nombre total de clients suceptible de se connecter à distance par PPTP dans votre organisation. Alternativement, si vous avez une connexion lente à Internet et que vous ne voulez pas que l'ensemble de ces clients PPTP puissent se connecter en même temps, vous pouvez saisir un nombre inférieur ici. Par exemple, si vous avez cinq utilisateurs qui de temps en temps utilisent le VPN PPTP pour se connecter à distance, en entrant ici le nombre de 5, cela permettra à chacun d'eux de se connecter à tout moment. La saisie de 2 permettra seulement à deux utilisateurs de se connecter à n'importe quel moment donné. Cependant si un troisième utilisateur tente de se connecter, il ou elle recevra un message d'erreur et il ne sera pas capable de se connecter jusqu'à ce que l'un des autres utilisateurs se déconnectent. Si, en revanche, vous avez entré 0, aucune connexion PPTP sera autorisé.
Avant que le serveur ne soit prêt à accepter les connexions PPTP, chaque utilisateur doit être autorisé à acceder au VPN PPTP par l'onglet "Acces par client VPN" dans le panneau Utilisateur du server-manager.
Pour vous connecter à distance avec l'aide PPTP, le protocole doit être installé sur chaque client Windows. Généralement, cela se fait par le panneau de configuration du réseau (vous pourriez avoir besoin de votre CD d'installation Windows d'origine). Après qu'il soit installé (un redémarrage de votre système Windows peut être nécessaire), vous pouvez créer de nouvelles connexions via le panneau de réglages réseau en saisissant l'adresse IP externe du serveur auquel vous souhaitez vous connecter. Une fois que vous avez terminé, vous devriez être en mesure d'établir une connexion PPTP en double-cliquant sur l'icône appropriée dans la fenêtre de réglages réseaux. Lorsque vous ouvrez la fenêtre de Voisinage réseau de votre explorateur windows, vous devriez voir votre groupe de travail du serveur s'afficher.
Paramétrage à distance
Pour permettre l'accès au server-manager à partir des réseaux distants ajoutez les adresses IP autorisées à la section de gestion à distance.
Pour permettre à un seul ordinateur (ou un réseau d'ordinateurs derrière un pare-feu) ajouter son adresse IP et le masque suivant.
223.102.19.24 255.255.255.255
SSH
If you need to connect directly to your server and login from a remote system belonging to you, we strongly encourage you to use ssh. In addition to UNIX and Linux systems, ssh client software is now also available for Windows and Macintosh systems. (See the section below.)
If you do not have any reason to allow remote access, we suggest you set this to No access.
SSH (secure shell) provides a secure, encrypted way to login to a remote machine across a network or to copy files from a local machine to a server. Many people do not realize that many programs such as telnet and ftp transmit your password in plain, unencrypted text across your network or the Internet. ssh and its companion program scp provide a secure way to login or copy files. The ssh protocol was originally invented by SSH Communications Security which sells commercial ssh servers, clients, and other related products. The protocol itself has two versions - SSH1 and SSH2 - both of which are supported by most clients and servers today. For more information about SSH Communications Security and its commercial products, visit http://www.ssh.com/.
OpenSSH, included with the SME Server, is a free version of the ssh tools and protocol. The server provides the ssh client programs as well as an ssh server daemon and supports both the SSH1 and SSH2 protocols. For more information about OpenSSH, visit http://www.openssh.com/.
Once ssh is enabled, you should be able to connect to your server simply by launching the ssh client on your remote system and ensuring that it is pointed to the external domain name or IP address for your server. In the default configuration, you should next be prompted for your user name. After you enter admin and your administrative password, you will be in the server console. From here you can change the server configuration, access the server manager through a text browser or perform other server console tasks.
If you do enable ssh access, you have additional configuration options:
- Allow administrative command line access over ssh - This allows someone to connect to your server and login as "root" with the administrative password. The user would then have full access to the underlying operating system. This can be useful if someone is providing remote support for your system. In most cases we recommend setting this to No.
- Allow ssh using standard passwords - If you choose Yes (the default), users will be able to connect to the server using a standard user name and password. This may be a concern from a security point of view, in that someone wishing to break into your system could connect to your ssh server and repeatedly enter user names and passwords in an attempt to find a valid combination. A more secure way to allow ssh access is called RSA Authentication and involves the copying of an ssh key from the client to the server. See the User Manual for details
- TCP Port for secure shell access - Change the port the ssh client connects to the server, choose a random free port eg. 822 This provides some protection from attacks on the usual port of 22.
- SSH clients
A number of different free software programs provide ssh clients for use in a Windows, Macintosh or Linux environment. Several are extensions of existing telnet programs that include ssh functionality. Two different lists of known clients can be found online at http://www.openssh.com/windows.html and http://www.freessh.org/.
A commercial ssh client is available from SSH Communications Security at: http://www.ssh.com/products/ssh/download.html. Note that the client is free for evaluation, academic and certain non-commercial uses.
FTP
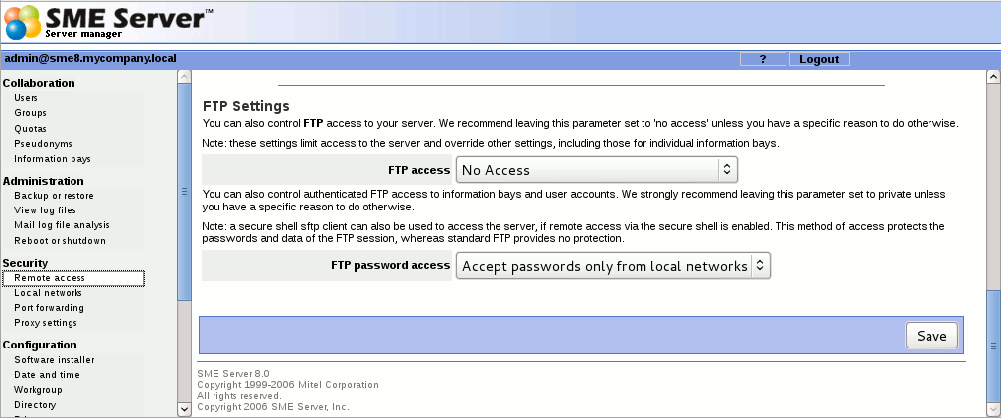
Another way to upload or download files to and from your server is to enable a protocol called FTP, or "file transfer protocol". This screen enables you to set your policy for FTP. Note that allowing liberal FTP access to your server does reduce your security. You have two options that you can set here.
FTP user account access: Private FTP access allows only people on your internal network to write files to your server. Public FTP access allows users both inside and outside your local network to read or write files on your server, provided they have an account and password. If, for example, you want to be able to update your web site from home using FTP, you would choose the "Public" setting. We strongly recommend you leave this as Private unless you have a specific reason to do so.
FTP access limits: This allows you to set an overall site-wide policy for FTP access. The setting you choose here will override all other FTP settings on your server . For example, if you choose "Disable public FTP access" here and then later configure an i-bay to allow public FTP access from the Internet, such access will be forbidden. Note that one of the choices here allows you to completely disable any use of FTP.
Telnet
Telnet has traditionally been one of the tools used to login remotely to other systems across a network or the Internet. However, when you use telnet, all user names and passwords are transmitted without any kind of encryption, dramatically reducing the security of your server. Because ssh usage has increased to an acceptable level, telnet access has been removed from the SME Server
Local networks
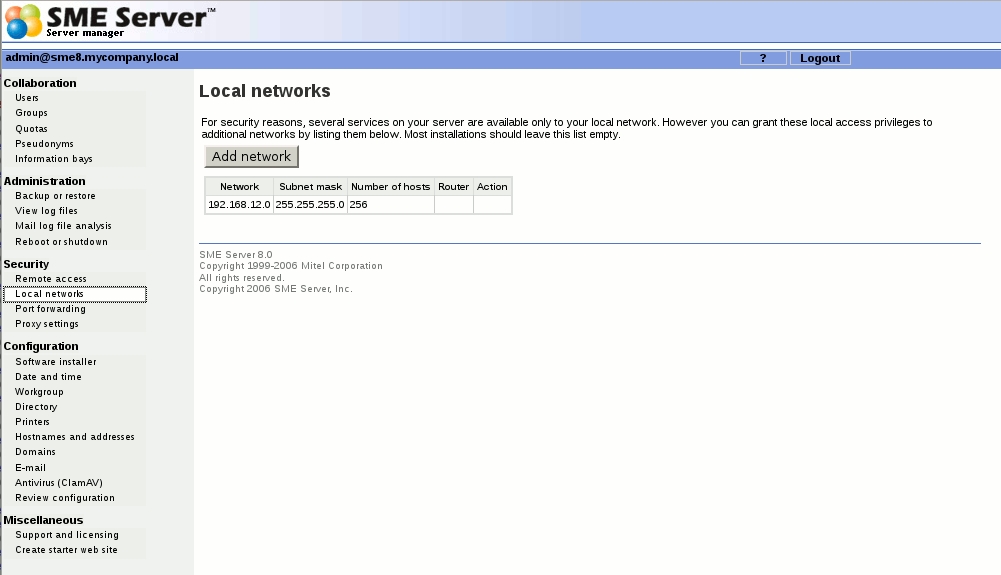
Your SME Server provides services to machines on the local network and it gives machines on that network special privileges and access. For example, only machines connected to the local network can access the mail server on your server to send mail. When you configured your server, you provided it with sufficient information to deduce its own local network. Machines on the network are automatically identified by the server as being eligible for these privileges and access.
If your company only has one network that is being serviced by the server, you do not need to add any information here.
Some advanced users may wish to extend privileges to more than one network of computers. If you would like your server to identify one or more additional networks for those privileges, you will be asked to enter those network IDs and the subnet mask for each network here.
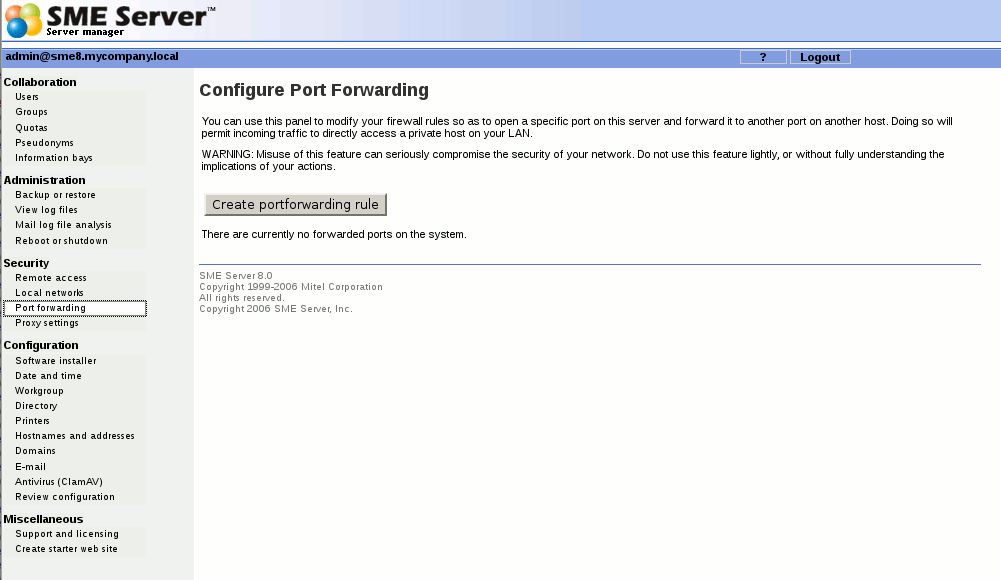
Port forwarding
Your SME Server provides the ability to forward its ports to other machines.
You can use the panel shown above to modify your firewall rules so as to open a specific port (or range of ports) on this server and forward it to another port on another host. Doing so will permit incoming traffic to directly access a private host on your LAN.
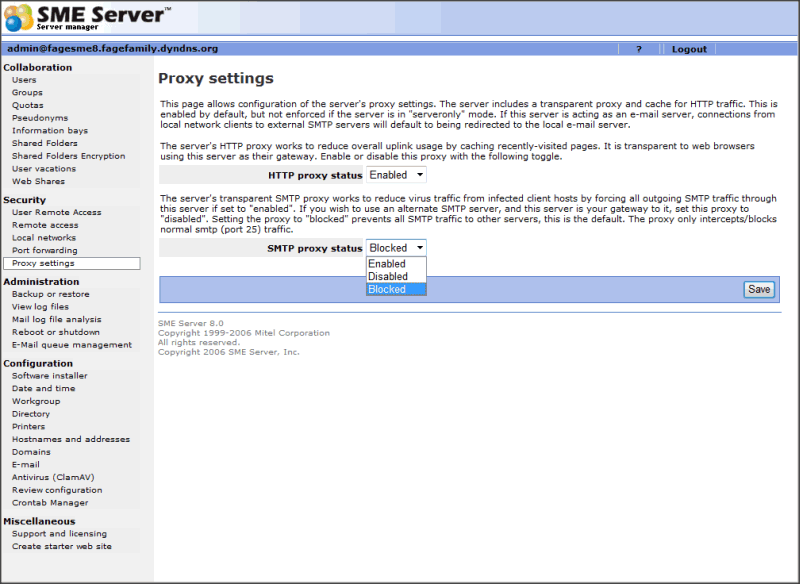
Proxy settings
Your SME Server has a transparent HTTP and SMTP proxy.
HTTP Proxy
The server's HTTP proxy works to reduce overall uplink usage by caching recently-visited pages. It is transparent to web browsers using this server as their gateway.
SMTP Proxy
The server's transparent SMTP proxy works to reduce virus traffic from infected client hosts by forcing all outgoing SMTP traffic through this server. If you wish to use an alternate SMTP server, and this server is your gateway to it, disable this proxy.
- Disabled. Clients behind SME Server are allowed to connect to any SMTP server anywhere in the world (that allow them to).
- Blocked. This forces all SMTP traffic to go through the server and be authenticated. All attempts to connect to any SMTP Server other than the SME Server will be blocked and treated as if there is no SMTP server on the other end. (This is the new default)
- Enabled. Any attempt to connect to an SMTP Server other than the SME Server will be redirected to the SME Server. If someone attempts to connect to an external smtp server (gmail for example) it will be redirected to the sme server. If they then have it set to authenticate to that external server instead of passing the user/pass to the external server it will pass it to the sme server and fail. (This is the old default)
Note: The server (by default) now requires email clients (other than webmail) to authenticate and will not allow auth to occur over an unsecure link. If for example you are using thunderbird then you must set the authentication method to normal password. Leave the connection security at starttls or ssl/tls.