Difference between revisions of "PHPki/fr"
(Created page with "{{Languages|PHPki}} === Mainteneur === [mailto:daniel@firewall-services.comDaniel B.] from [http://www.firewall-services.com Firewall Services] === Version ...") |
|||
| Line 2: | Line 2: | ||
=== Mainteneur === | === Mainteneur === | ||
| − | [mailto:daniel@firewall-services.com[[User:VIP-ire|Daniel B.]]] | + | [mailto:daniel@firewall-services.com[[User:VIP-ire|Daniel B.]]] de [http://www.firewall-services.com Firewall Services] |
=== Version === | === Version === | ||
| Line 9: | Line 9: | ||
{{ #smeversion: phpki }} | {{ #smeversion: phpki }} | ||
| − | + | Veuillez suivre les instructions d'installation ci-dessous, ils satisferont toutes les dépendances et les dernières versions des 2 RPMs qui seront installés automatiquement. | |
=== Description === | === Description === | ||
| − | [http://sourceforge.net/projects/phpki/ PHPki] | + | [http://sourceforge.net/projects/phpki/ PHPki] est une application OpenSource pour gérer a multi-agency PKI conforme HIPAA. Avec ça, vous pouvez gérer de manière centralisé les certificats X.509 utilisés avec S/MIME activé sur les clients e-mail, Serveurs SSL, et applications VPN. PHPki est maintenant utilisé pour gérer les certificats avec la dernière version de la contrib [[OpenVPN_Bridge|SME Server OpenVPN Bridge]]. |
| − | + | Vous pouvez voir la démo d'installation [http://phpki.sourceforge.net/phpki/ ici] | |
=== Pré-requis === | === Pré-requis === | ||
*SME Server 7.X | *SME Server 7.X | ||
| − | + | Vérifié sur : | |
SME Server 7.4 - [[User:RequestedDeletion|RequestedDeletion]] | SME Server 7.4 - [[User:RequestedDeletion|RequestedDeletion]] | ||
| Line 26: | Line 26: | ||
{{Warning box|This version of PHPki is a slightly modified version, so it can be used with certificates generated with previous release of smeserver-openvpn-bridge, plus some others minor modifications. | {{Warning box|This version of PHPki is a slightly modified version, so it can be used with certificates generated with previous release of smeserver-openvpn-bridge, plus some others minor modifications. | ||
}} | }} | ||
| + | |||
| + | |||
| + | Cette version de PHPki est une version légèrement modifiée, de sorte qu'elle puisse être utilisé avec les certificats générés avec la version précédente de [[OpenVPN_Bridge|SME Server OpenVPN Bridge]], ainsi que quelques autres de modifications mineures. | ||
=== Installation === | === Installation === | ||
| Line 31: | Line 34: | ||
==== SME Server 7, SME Server 8, SME Server 9 ==== | ==== SME Server 7, SME Server 8, SME Server 9 ==== | ||
| − | + | Pour sme8 | |
| − | * | + | *Installer les RPMs : |
yum --enablerepo=smecontribs install smeserver-phpki | yum --enablerepo=smecontribs install smeserver-phpki | ||
| − | * | + | *Puis redémmarer les services : |
expand-template /etc/httpd/conf/httpd.conf | expand-template /etc/httpd/conf/httpd.conf | ||
expand-template /etc/httpd/pki-conf/httpd.conf | expand-template /etc/httpd/pki-conf/httpd.conf | ||
| Line 41: | Line 44: | ||
sv u /service/httpd-pki | sv u /service/httpd-pki | ||
| − | * | + | *Sinon, il est aussi possible de redemmarer le serveur : |
signal-event post-upgrade; signal-event reboot | signal-event post-upgrade; signal-event reboot | ||
| − | + | Pour sme9 | |
| − | + | Vous devez activé le dépôt [[epel]] | |
| − | * | + | *Installer les RPMs : |
yum --enablerepo=smecontribs,epel install smeserver-phpki | yum --enablerepo=smecontribs,epel install smeserver-phpki | ||
| − | * | + | *Puis redémmarer les services : |
expand-template /etc/httpd/conf/httpd.conf | expand-template /etc/httpd/conf/httpd.conf | ||
expand-template /etc/httpd/pki-conf/httpd.conf | expand-template /etc/httpd/pki-conf/httpd.conf | ||
| Line 56: | Line 59: | ||
sv u /service/httpd-pki | sv u /service/httpd-pki | ||
| − | * | + | *Sinon, il est aussi possible de redemmarer le serveur : |
signal-event post-upgrade; signal-event reboot | signal-event post-upgrade; signal-event reboot | ||
Revision as of 14:29, 14 August 2014
Mainteneur
Daniel B. de Firewall Services
Version
Veuillez suivre les instructions d'installation ci-dessous, ils satisferont toutes les dépendances et les dernières versions des 2 RPMs qui seront installés automatiquement.
Description
PHPki est une application OpenSource pour gérer a multi-agency PKI conforme HIPAA. Avec ça, vous pouvez gérer de manière centralisé les certificats X.509 utilisés avec S/MIME activé sur les clients e-mail, Serveurs SSL, et applications VPN. PHPki est maintenant utilisé pour gérer les certificats avec la dernière version de la contrib SME Server OpenVPN Bridge.
Vous pouvez voir la démo d'installation ici
Pré-requis
- SME Server 7.X
Vérifié sur : SME Server 7.4 - RequestedDeletion
Cette version de PHPki est une version légèrement modifiée, de sorte qu'elle puisse être utilisé avec les certificats générés avec la version précédente de SME Server OpenVPN Bridge, ainsi que quelques autres de modifications mineures.
Installation
SME Server 7, SME Server 8, SME Server 9
Pour sme8
- Installer les RPMs :
yum --enablerepo=smecontribs install smeserver-phpki
- Puis redémmarer les services :
expand-template /etc/httpd/conf/httpd.conf expand-template /etc/httpd/pki-conf/httpd.conf sv t /service/httpd-e-smith sv u /service/httpd-pki
- Sinon, il est aussi possible de redemmarer le serveur :
signal-event post-upgrade; signal-event reboot
Pour sme9
Vous devez activé le dépôt epel
- Installer les RPMs :
yum --enablerepo=smecontribs,epel install smeserver-phpki
- Puis redémmarer les services :
expand-template /etc/httpd/conf/httpd.conf expand-template /etc/httpd/pki-conf/httpd.conf sv t /service/httpd-e-smith sv u /service/httpd-pki
- Sinon, il est aussi possible de redemmarer le serveur :
signal-event post-upgrade; signal-event reboot
Configurer le nouveau PKI
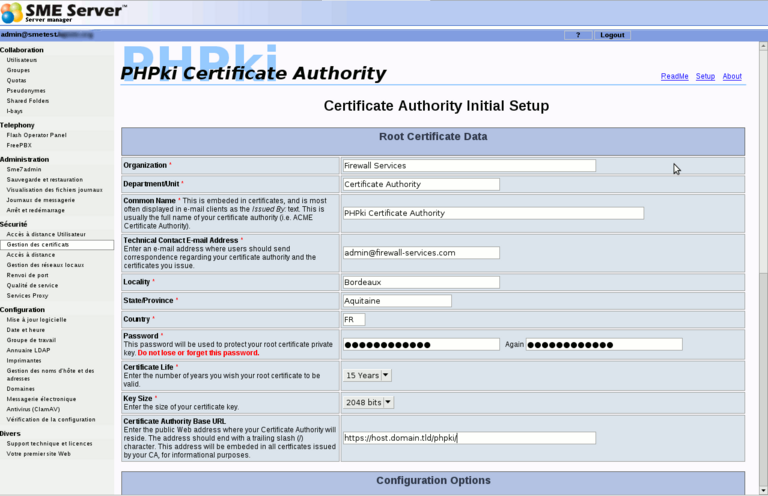
Go in the server-manager, you'll find a new "Manage Certificates" menu (or you can use the URL https://server.domain.tld/phpki/ca) Here you have to enter the following informations:
- Organisation
- Department
- Common Name of the Master CA
- E-mail (technical contact)
- City
- State
- Country Code
- Password (to protect the private key of the Master CA)
- Validity of the CA
- Keys size
- URL of your PKI (https://my.domain.tld/phpki)
This screenshot illustrate the first (and the most important) part of this configuration page:
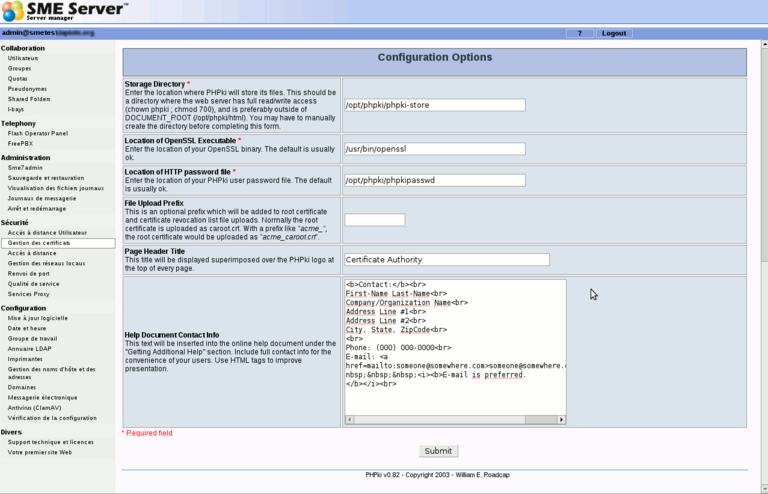
The second part is like this:
The default settings should be OK for most installations. You may just want to change the "Help Document Contact Info" part.
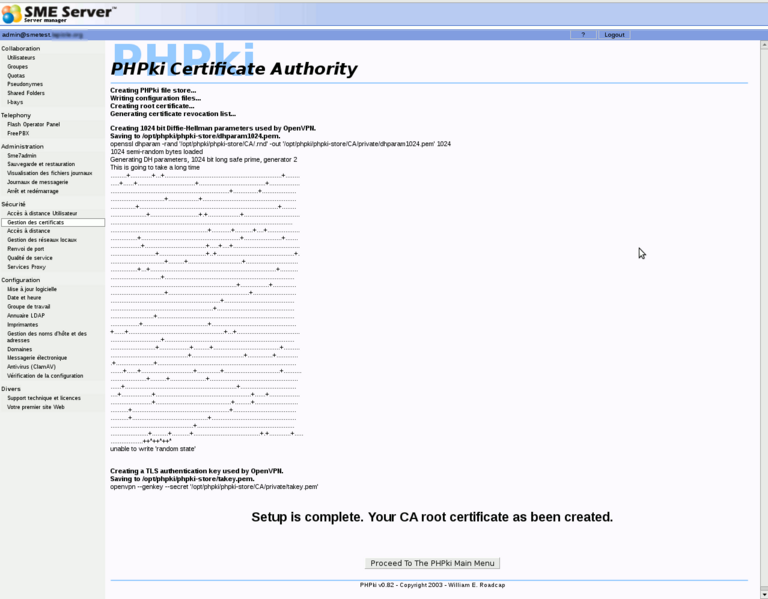
Once you have submitted this form (which can take several minutes, as generating dh parameters can take a long time), you should have something like this:
Now you'll be able to start using PHPki. It's quite easy to use.
The administrative interface is available on the server-manager or directly https://my.domain.tld/phpki/ca
There's also a public interface, available only from the local networks, but without password at https://my.domain.tld/phpki. Here, users can download the Master CA certificate, the CRL, or search for certificates of other users (public part only of course).
Migration des certificats pour l'installation des versions précédentes de la contribs OpenVPN-Bridge
If you are installing this phpki contrib because you have used OpenVPN_Bridge before and have already certificates, follow the instructions below. If you have a fresh and new install of OpenVPN_Bridge, skip the below instructions for you do not have 'old' certificates!
PHPki is now the certificate manager recommended to manage OpenVPN_Bridge certificates. This part will explain how-to import your certificates created with openvpn-bridge into PHPki
- First, you need to install the contribs as it's explain on this page (you can enter anything for the configuration of the CA, all your old parameters will be restored)
- Second, you need to copy this script on your server (for example as /root/migrate.sh) and execute it as root.
#!/bin/bash
# Read Openvpn-Bridge DB
ORGNAME=$(/sbin/e-smith/db openvpn-bridge getprop default_config organizationName)
COUNTRY=$(/sbin/e-smith/db openvpn-bridge getprop default_config countryCode)
STATE=$(/sbin/e-smith/db openvpn-bridge getprop default_config countryName)
LOC=$(/sbin/e-smith/db openvpn-bridge getprop default_config localityName)
DEP=$(/sbin/e-smith/db openvpn-bridge getprop default_config sectionName)
KEYSIZE=$(/sbin/e-smith/db openvpn-bridge getprop default_config keySize)
EMAIL=$(/sbin/e-smith/db openvpn-bridge getprop default_config mailAddress)
OPENSSL=/usr/bin/openssl
OLDDIR=/etc/openvpn/easy-rsa/keys/bridge/
NEWDIR=/opt/phpki/phpki-store/CA/
# Store the actual time in $TIME
TIME=$(date +%d%m%Y%H%M%S)
# Create needed directories
prepare_dir(){
mkdir -p $NEWDIR/{certs,newcerts,requests,pfx,private}
}
# Migrate the certificates to phpki store
migrate_certs(){
cd $OLDDIR
# Copy the old index.txt and serial
cat $OLDDIR/index.txt > $NEWDIR/index.txt
cat serial > $NEWDIR/serial
# Copy the cacert related files
cat ca.crt > $NEWDIR/certs/cacert.pem
cat ca.key > $NEWDIR/private/cakey.pem
# Now, for each file ending with .crt
for CERT in $(ls ./*.crt); do
CERT=$(basename $CERT .crt)
ISININDEX=$(grep -c "/CN=$CERT/" $NEWDIR/index.txt)
# If the current cert isn't referenced in the index,
# or the corresponding key or csr file dosn't exists, then skip it
# This can happen in some situation where the serial has been corrupted
if [ $ISININDEX -gt 0 ]&&[ -s $CERT.key ]&&[ -s $CERT.csr ]; then
# Retrieve the serial number as reported by openssl
SERIAL=$(openssl x509 -noout -serial -in $CERT.crt | cut -d"=" -f 2)
# Create the pem only cert in the new dir
$OPENSSL x509 -in $CERT.crt -inform PEM -outform PEM -out $NEWDIR/newcerts/$SERIAL.pem
# Create the der formated cert
$OPENSSL x509 -in $CERT.crt -inform PEM -outform DER -out $NEWDIR/certs/$SERIAL.der
# And the pkcs12 bundle (cert+key+ca)
$OPENSSL pkcs12 -export -in $CERT.crt -inkey $CERT.key -certfile ca.crt -caname $ORGNAME -passout pass: -out $NEWDIR/pfx/$SERIAL.pfx
# Copy the private key
cat $CERT.key > $NEWDIR/private/$SERIAL-key.pem
# And the cert request
cat $CERT.csr > $NEWDIR/requests/$SERIAL-req.pem
fi
done
}
perms(){
# Restrict access
chown -R phpki:phpki $NEWDIR
chmod -R o-rwx $NEWDIR
}
phpki_conf(){
# Retrieve the common name of our CA with openssl command
CACN=$($OPENSSL x509 -subject -noout -in $OLDDIR/ca.crt | cut -d'=' -f 8 | cut -d'/' -f 1)
if [ -e /opt/phpki/phpki-store/config/config.php ]; then
# Move the actual phpki configuration file
mv /opt/phpki/phpki-store/config/config.php /opt/phpki/phpki-store/config/config.php.$TIME
# And use sed to configure it properly
sed -e "s/config\['organization'\].*/config\['organization'\] = '$ORGNAME';/" \
-e "s/config\['unit'\].*/config\['unit'\] = '$DEP';/" \
-e "s/config\['contact'\].*/config\['contact'\] = '$EMAIL';/" \
-e "s/config\['locality'\].*/config\['locality'\] = '$LOC';/" \
-e "s/config\['province'\].*/config\['province'\] = '$STATE';/" \
-e "s/config\['country'\].*/config\['country'\] = '$COUNTRY';/" \
-e "s/config\['common_name'\].*/config\['common_name'\] = '$CACN';/" \
-e "s/config\['ca_pwd'\].*/config\['ca_pwd'\] = '';/" \
-e "s/config\['keysize'\].*/config\['keysize'\] = '$KEYSIZE';/" \
/opt/phpki/phpki-store/config/config.php.$TIME \
> /opt/phpki/phpki-store/config/config.php
fi
}
migrate_var(){
# Here, we just migrate dhparam and ta to phpki store
if [ -e $OLDDIR/dh.pem ]; then
cat $OLDDIR/dh.pem > $NEWDIR/private/dhparam1024.pem
fi
if [ -e $OLDDIR/ta.key ]; then
cat $OLDDIR/ta.key > $NEWDIR/private/takey.pem
fi
}
prepare_dir
migrate_certs
phpki_conf
migrate_var
perms
Now, go in the server-manager, in "Manage Certificates" and check your old certificates are here.
Désintallation
To uninstall the contrib from your server, just run the following commands:
yum remove smeserver-phpki phpki expand-template /etc/httpd/conf/httpd.conf sv t /service/httpd-e-smith
Certificates and PKI configuration are stored in /opt/phpki/phpki-store, php files are in /opt/phpki/html
Ré-installation
If you have removed the contrib, and want to re-install it, you'll need to follow these steps after you have installed the rpms:
cd /opt/phpki/html/ rm -f index.php rm -f setup.php ln -s main.php index.php cat config.php.rpmsave > config.php cd ca rm -f index.php ln -s main.php index.php
Bugs
Please raise bugs under the SME-Contribs section in bugzilla and select the smeserver-phpki component or use this link