Difference between revisions of "Openfire"
m (Removed hashes in front of shell commands) |
m (Removed hashes in front of shell commands) |
||
| Line 69: | Line 69: | ||
== SME Server specific configuration == | == SME Server specific configuration == | ||
| − | + | config set openfire service TCPPorts '5222,5223,7777' access public status enabled | |
| − | + | signal-event remoteaccess-update | |
Add startup link: | Add startup link: | ||
| − | + | ln -s /etc/rc.d/init.d/e-smith-service /etc/rc.d/rc7.d/S99openfire | |
== Optional == | == Optional == | ||
Revision as of 10:52, 26 November 2007
Description
Openfire (formerly Wildfire) is a real time collaboration (RTC) server dual-licensed under the Open Source GPL and commercially. It uses the only widely adopted open protocol for instant messaging, XMPP (also called Jabber). Openfire is incredibly easy to setup and administer, but offers rock-solid security and performance.
Download and install java runtime
Download jre-6u3-linux-i586-rpm.bin & Openfire 3.4.1
Go to http://www.java.com/en/download/linux_manual.jsp and download the Linux RPM (self-extracting file)
chmod a+x jre-6u1-linux-i586-rpm.bin sh ./jre-6u1-linux-i586-rpm.bin
Download and install Openfire
Go to http://www.igniterealtime.org/downloads/index.jsp and click on linux, download the latest openfire rpm and install:
# yum localinstall openfire-3.4.1-1.i386.rpm
Create the Database
To create the Openfire Database, you'll need to perform each of the following steps:
mysqladmin create openfiredb mysql -e "grant all privileges on openfiredb.* to openfireuser@localhost identified by 'yourpassword'" mysql -e "flush privileges" cd /opt/openfire/resources/database mysql openfiredb < openfire_mysql.sql
Access MySQL from the local network
To use the MySQL database you will need to run a script to make port 3306 available to the Openfire Instant Messaging Server.
/sbin/e-smith/config setprop mysqld LocalNetworkingOnly no /sbin/e-smith/expand-template /etc/my.cnf /etc/rc.d/rc7.d/S50mysqld restart
Start the Openfire Messaging Server
/etc/rc.d/init.d/openfire start
Visit admin web page to complete Openfire configuration
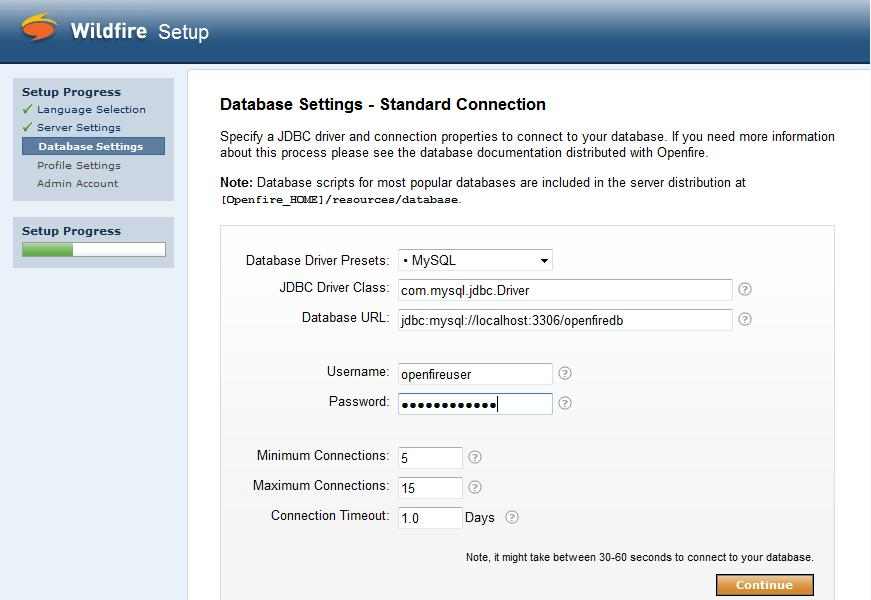
Go to http://yourserver:9090 (insecure) or https://yourserver:9091 (secure)and follow through the setup via the browser. The only area that may be confusing is the database setup area. See example configuration below.
Database Driver Presets: MySql
JDBC Driver Class: com.mysql.jdbc.Driver
Database URL: jdbc:mysql://localhost:3306/openfiredb
Username: openfireuser
Password: yourpassword
SME Server specific configuration
config set openfire service TCPPorts '5222,5223,7777' access public status enabled signal-event remoteaccess-update
Add startup link:
ln -s /etc/rc.d/init.d/e-smith-service /etc/rc.d/rc7.d/S99openfire
Optional
If you would like to have web access to the openfire documentation has been installed on your server, this section will show you how to make an e-smith custom template.
Make the custom-template directory:
mkdir -p /etc/e-smith/templates-custom/etc/httpd/conf/httpd.conf cd /etc/e-smith/templates-custom/etc/httpd/conf/httpd.conf
Create and edit a file called "99openfire"
pico -w 99openfire
(add the code shown below to the template) (you can select and copy then paste in PuTTY with right click)
# Openfire instant messaging server
Alias /openfire /opt/openfire
<Directory /opt/openfire>
AddType application/x-httpd-php .php .php3 .phtml
Options Indexes +Includes FollowSymLinks
order deny,allow
deny from all
allow from all
</Directory>
# end of Openfire fragment
ctrl-x to save, y to agree, and [Enter] to exit the PICO editor
Expand the template
expand-template /etc/httpd/conf/httpd.conf
/etc/rc.d/init.d/httpd-e-smith restart
access your documentation at:
http://yourservername-or-IP/openfire/documentation/
To reiterate, this is NOT an essential step in the installation process and only provides local access to the documentation.
Uninstalling Openfire
Commands to remove openfire
/etc/rc.d/init.d/openfire stop yum remove openfire rm -Rf /opt/openfire mysqladmin drop openfiredb config delete openfire signal-event remoteaccess-update