Difference between revisions of "Wireguard"
Unnilennium (talk | contribs) (Created page with "{{Languages}} <!-- here we define the contrib name variable --> <!-- we get the page title, remove suffix for translated version; if needed you can define there with the value...") |
Unnilennium (talk | contribs) |
||
| (13 intermediate revisions by 3 users not shown) | |||
| Line 8: | Line 8: | ||
{{Infobox contribs | {{Infobox contribs | ||
|name={{#var:contribname}} | |name={{#var:contribname}} | ||
| − | |image= | + | |image=Wireguard_logo.svg |
|description_image= {{#var:contribname}} logo | |description_image= {{#var:contribname}} logo | ||
|maintainer= Unnilennium | |maintainer= Unnilennium | ||
|licence= GPLv2 for kernel modules, MIT, BSD, Apache 2.0, or GPL for other parts | |licence= GPLv2 for kernel modules, MIT, BSD, Apache 2.0, or GPL for other parts | ||
|url= https://www.wireguard.com/ | |url= https://www.wireguard.com/ | ||
| − | |category= | + | |category= VPN,security |
|tags=VPN,security,network,remote | |tags=VPN,security,network,remote | ||
| − | }} | + | |video=}} |
===Maintainer=== | ===Maintainer=== | ||
| Line 21: | Line 21: | ||
[[User:Unnilennium|Jean-Philippe Pialasse]] | [[User:Unnilennium|Jean-Philippe Pialasse]] | ||
| − | === Version === | + | ===Version=== |
<!-- keep this first element as is, you can add some if needed --> | <!-- keep this first element as is, you can add some if needed --> | ||
{{#smeversion: {{#var:smecontribname}} }} | {{#smeversion: {{#var:smecontribname}} }} | ||
| − | |||
| − | === Description === | + | ===Description=== |
| − | + | As always we worked to make it Simple and Stupid. Wireguard is the easiest VPN server to set, but we managed to make it even easier for you ! | |
| + | according to WireGuard website: | ||
| − | === Installation === | + | WireGuard® is an extremely simple yet fast and modern VPN that utilizes state-of-the-art cryptography. It aims to be faster, simpler, leaner, and more useful than IPsec, while avoiding the massive headache. It intends to be considerably more performant than OpenVPN. WireGuard is designed as a general purpose VPN for running on embedded interfaces and super computers alike, fit for many different circumstances. Initially released for the Linux kernel, it is now cross-platform (Windows, macOS, BSD, iOS, Android) and widely deployable. It is currently under heavy development, but already it might be regarded as the most secure, easiest to use, and simplest VPN solution in the industry. |
| − | <tabs container | + | |
| − | + | ===Installation=== | |
| − | + | <tabs container=""><tab name="For SME 10"> | |
| − | |||
| − | |||
| − | |||
| − | |||
yum --enablerepo=smecontribs install {{#var:smecontribname}} | yum --enablerepo=smecontribs install {{#var:smecontribname}} | ||
| − | + | then log to your server-manager to start adding clients. | |
| − | |||
</tab></tabs> | </tab></tabs> | ||
| − | === Configuration === | + | ===Configuration=== |
| + | |||
| + | ==== using server-manager ==== | ||
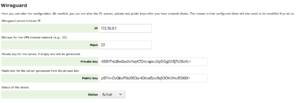
| + | [[File:Wireguard-panel.png|none|thumb|main panel]] | ||
| + | On the main panel you can see at a glance, server configuration, connected clients, and configured clients. | ||
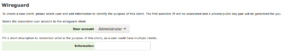
| + | [[File:Wireguard-config.png|none|thumb|configure the server]] | ||
| + | You can adjust the server configuration: disable the service, change the server main Ip and mask. Default will generate a class B network for more than 1000 device connected, looking that all your users might want a dedicated client for every devices (phone, pad, laptop...). 172.* class B tends to be less commonly used than 192.168.* class C network or 10.+ class A network, so this also should limit collision for your clients behind a LAN when launching their VPN session. | ||
| + | |||
| + | The private and public key are generated upon installation, but if you have specific needs, go ahead and play with them. | ||
| + | <br /> | ||
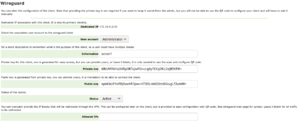
| + | [[File:Wireguard-add-client.png|none|thumb|add a new client]] | ||
| + | To add a new client simply press the button, and select a user that will be associated to this client, and give some information about this client. IF you want to create a client for the phone of the admin, simply type "phone", then press create button and private"/public key will be generated and first available ip will be associated to the client. | ||
| + | <br /> | ||
| + | [[File:Wireguard-qrcode.png|none|thumb|get client configuration and qrcode]] | ||
| + | You can easily configure your client using a qrcode or a generated configuration. | ||
| + | <br /> | ||
| + | [[File:Wireguard-edit-client.png|none|thumb|client modification]] | ||
| + | |||
| + | |||
| + | If you want to alter the client configuration you can do so on this screen, you can even remove the private key if you do not want it on the server, or set your own public key without revealing the private key, it is only needed to generate the qrcode, not to allow you to connect. | ||
| + | |||
| + | ==== advanced manual configuration ==== | ||
you can list the available configuration with the following command : | you can list the available configuration with the following command : | ||
| − | config show | + | config show wg-quick@wg0 |
Some of the properties are not shown, but are defaulted in a template or a script. Here a more comprehensive list with default and expected values : | Some of the properties are not shown, but are defaulted in a template or a script. Here a more comprehensive list with default and expected values : | ||
| Line 54: | Line 70: | ||
! | ! | ||
|- | |- | ||
| − | | | + | |UDPPort |
| − | | | + | |51820 |
|string | |string | ||
| − | | | + | |should keep this one as default, but free to do as you want |
|- | |- | ||
| − | | | + | |mask |
| − | | | + | |22 |
| + | |network mask bit | ||
| + | |the default allow 1024 hosts | ||
| + | |- | ||
| + | |ip | ||
| + | |172.X.0.1 | ||
| + | |IP v4 | ||
| + | |one class B IP is generated on installation, feel free to set as you want | ||
| + | |- | ||
| + | |private | ||
| + | | | ||
|string | |string | ||
| − | | | + | |private key, generated |
|- | |- | ||
| − | | | + | |public |
| − | | | + | | |
|string | |string | ||
| − | | | + | |public key, generated |
|- | |- | ||
|access | |access | ||
| Line 80: | Line 106: | ||
| + | You can also check the configured clients: | ||
| + | db wireguard show 172.X.0.2 | ||
| + | |||
| + | <br /> | ||
| + | {| class="wikitable" | ||
| + | !property | ||
| + | !default | ||
| + | !values | ||
| + | ! | ||
| + | |- | ||
| + | |allowedips | ||
| + | | | ||
| + | |list of ip/mask | ||
| + | |default is empty for all 0.0.0.0/0 | ||
| + | |- | ||
| + | |info | ||
| + | | | ||
| + | |string | ||
| + | |name or information about the client | ||
| + | |- | ||
| + | |ip | ||
| + | |172.X.0.Y | ||
| + | |IP v4 | ||
| + | |should be part of wg0 network | ||
| + | |- | ||
| + | |private | ||
| + | | | ||
| + | |string | ||
| + | |private key, generated | ||
| + | |- | ||
| + | |public | ||
| + | | | ||
| + | |string | ||
| + | |public key, generated | ||
| + | |- | ||
| + | |status | ||
| + | |enabled | ||
| + | |enabled,disabled | ||
| + | | | ||
| + | |} | ||
| + | |||
| + | |||
| + | ===Sources of information=== | ||
| − | = | + | *https://www.subnet-calculator.com/subnet.php?net_class=B |
| − | + | *https://github.com/pirate/wireguard-docs | |
| + | *https://manpages.debian.org/unstable/wireguard-tools/wg.8.en.html | ||
| + | *https://www.linuxbabe.com/centos/wireguard-vpn-server-centos | ||
| + | * | ||
| − | === Bugs === | + | <br /> |
| + | ===Uninstall=== | ||
| + | yum remove {{#var:smecontribname}} {{#var:contribname}} wireguard-tools kmod-wireguard | ||
| + | |||
| + | ===Bugs=== | ||
Please raise bugs under the SME-Contribs section in {{BugzillaFileBug|product=|component=|title= bugzilla}} | Please raise bugs under the SME-Contribs section in {{BugzillaFileBug|product=|component=|title= bugzilla}} | ||
and select the {{#var:smecontribname}} component or use {{BugzillaFileBug|product=SME%20Contribs|component={{#var:smecontribname}}|title=this link}} | and select the {{#var:smecontribname}} component or use {{BugzillaFileBug|product=SME%20Contribs|component={{#var:smecontribname}}|title=this link}} | ||
| Line 93: | Line 169: | ||
Only released version in smecontrib are listed here. | Only released version in smecontrib are listed here. | ||
| − | {{ #smechangelog: {{#var:smecontribname}} }} | + | {{#smechangelog: {{#var:smecontribname}} }} |
<!-- list of category you want to see this page in --> | <!-- list of category you want to see this page in --> | ||
[[Category: Contrib]] | [[Category: Contrib]] | ||
| − | |||
<!-- Please keep there the template revision number as is --> | <!-- Please keep there the template revision number as is --> | ||
| − | |||
| − | |||
Latest revision as of 12:19, 9 May 2023
 | |
| wireguard logo | |
| Maintainer | Unnilennium |
|---|---|
| Url | https://www.wireguard.com/ |
| Licence | GPLv2 for kernel modules, MIT, BSD, Apache 2.0, or GPL for other parts |
| Category | |
| Tags | VPN, security, network, remote |
Maintainer
Version
Description
As always we worked to make it Simple and Stupid. Wireguard is the easiest VPN server to set, but we managed to make it even easier for you !
according to WireGuard website:
WireGuard® is an extremely simple yet fast and modern VPN that utilizes state-of-the-art cryptography. It aims to be faster, simpler, leaner, and more useful than IPsec, while avoiding the massive headache. It intends to be considerably more performant than OpenVPN. WireGuard is designed as a general purpose VPN for running on embedded interfaces and super computers alike, fit for many different circumstances. Initially released for the Linux kernel, it is now cross-platform (Windows, macOS, BSD, iOS, Android) and widely deployable. It is currently under heavy development, but already it might be regarded as the most secure, easiest to use, and simplest VPN solution in the industry.
Installation
yum --enablerepo=smecontribs install smeserver-wireguard
then log to your server-manager to start adding clients.
Configuration
using server-manager
On the main panel you can see at a glance, server configuration, connected clients, and configured clients.
You can adjust the server configuration: disable the service, change the server main Ip and mask. Default will generate a class B network for more than 1000 device connected, looking that all your users might want a dedicated client for every devices (phone, pad, laptop...). 172.* class B tends to be less commonly used than 192.168.* class C network or 10.+ class A network, so this also should limit collision for your clients behind a LAN when launching their VPN session.
The private and public key are generated upon installation, but if you have specific needs, go ahead and play with them.
To add a new client simply press the button, and select a user that will be associated to this client, and give some information about this client. IF you want to create a client for the phone of the admin, simply type "phone", then press create button and private"/public key will be generated and first available ip will be associated to the client.
You can easily configure your client using a qrcode or a generated configuration.
If you want to alter the client configuration you can do so on this screen, you can even remove the private key if you do not want it on the server, or set your own public key without revealing the private key, it is only needed to generate the qrcode, not to allow you to connect.
advanced manual configuration
you can list the available configuration with the following command :
config show wg-quick@wg0
Some of the properties are not shown, but are defaulted in a template or a script. Here a more comprehensive list with default and expected values :
| property | default | values | |
|---|---|---|---|
| UDPPort | 51820 | string | should keep this one as default, but free to do as you want |
| mask | 22 | network mask bit | the default allow 1024 hosts |
| ip | 172.X.0.1 | IP v4 | one class B IP is generated on installation, feel free to set as you want |
| private | string | private key, generated | |
| public | string | public key, generated | |
| access | private | private, public | |
| status | enabled | enabled,disabled |
You can also check the configured clients:
db wireguard show 172.X.0.2
| property | default | values | |
|---|---|---|---|
| allowedips | list of ip/mask | default is empty for all 0.0.0.0/0 | |
| info | string | name or information about the client | |
| ip | 172.X.0.Y | IP v4 | should be part of wg0 network |
| private | string | private key, generated | |
| public | string | public key, generated | |
| status | enabled | enabled,disabled |
Sources of information
- https://www.subnet-calculator.com/subnet.php?net_class=B
- https://github.com/pirate/wireguard-docs
- https://manpages.debian.org/unstable/wireguard-tools/wg.8.en.html
- https://www.linuxbabe.com/centos/wireguard-vpn-server-centos
Uninstall
yum remove smeserver-wireguard wireguard wireguard-tools kmod-wireguard
Bugs
Please raise bugs under the SME-Contribs section in bugzilla
and select the smeserver-wireguard component or use this link
Below is an overview of the current issues for this contrib:
| ID | Product | Version | Status | Summary (7 tasks) ⇒ |
|---|---|---|---|---|
| 12492 | SME Contribs | 10.0 | RESOLVED | Error in SM2 wireguard panel |
| 11767 | SME Contribs | Futur | CONFIRMED | Change Smeserver (Wireguard) external IP address in Wireguard configuration for clients |
| 11732 | SME Contribs | 10.0 | CONFIRMED | NFR: allow SME to connect to remote server |
| 11729 | SME Contribs | 10.0 | CONFIRMED | delete unused network |
| 11728 | SME Contribs | 10.0 | CONFIRMED | NFR: add custom DNS field |
| 11727 | SME Contribs | 10.0 | CONFIRMED | NFR: easy AllowedIPs configuration |
| 11726 | SME Contribs | 10.0 | CONFIRMED | NFR: userpanel |
Changelog
Only released version in smecontrib are listed here.
- Edit SM2 Menu entry to conform to new arrangements [SME: 12493]
- remove masquerade and forward directive on startup [SME: 12288]
- apply locale 2022-11-11 patch
2022/05/29 Jean-Philippe Pialasse 1.0-16.sme
- improve check and tidying for non local network type [SME: 11771]
- Fix typos in templates