Difference between revisions of "SSH Public-Private Keys"
(New page: 27th December 2003 Ian Wells Introduction This is an introduction to using Public-Private Keys as applied to SSH. It has been written in response to questions regarding my CVS How-To. It...) |
|||
| (20 intermediate revisions by 6 users not shown) | |||
| Line 1: | Line 1: | ||
| − | + | Extracted From: http://www.wellsi.com/sme/ssh/ssh.html | |
| − | |||
| − | This is an introduction to using Public-Private Keys as applied to SSH. It has been written in response to questions regarding my CVS How-To. | + | Author: Ian Wells (27th December 2003) |
| + | |||
| + | |||
| + | == Introduction == | ||
| + | |||
| + | |||
| + | This is an introduction to using Public-Private Keys as applied to SSH. It has been written in response to questions regarding my [http://www.wellsi.com/sme/cvs/cvs.html CVS How-To]. | ||
It currently covers the first three steps needed to use Public-Private keys | It currently covers the first three steps needed to use Public-Private keys | ||
| − | + | *Generate Public-Private Key Pairs | |
| − | + | *Installing the Public Key onto the Server | |
| − | + | *Installing the Private Key onto the Clients | |
It also has sections on | It also has sections on | ||
| − | + | *Using public keys for SSH authentication | |
| − | + | *Further Information | |
The following has been tested using a Mitel SME Server, and Windows XP& RedHat 8.0 clients. | The following has been tested using a Mitel SME Server, and Windows XP& RedHat 8.0 clients. | ||
| − | Some sections use PuTTY to connect to the server, it is a free implementation of SSH for Win32 platforms, with extensive online documentation. | + | Some sections use [http://www.chiark.greenend.org.uk/~sgtatham/putty/ PuTTY] to connect to the server, it is a free implementation of SSH for Win32 platforms, with extensive [http://the.earth.li/~sgtatham/putty/latest/htmldoc/ online documentation]. |
| − | Generate Public-Private Key Pairs | + | |
| + | == Generate Public-Private Key Pairs == | ||
This section describes three ways to generate the public-private key pairs, and specifically a SSH protocol 2 RSA key pair. | This section describes three ways to generate the public-private key pairs, and specifically a SSH protocol 2 RSA key pair. | ||
| − | + | *1. On Windows using PuTTY | |
| − | + | *2. On SME Server using OpenSSH | |
| − | + | *3. On RedHat 8.0 using OpenSSH | |
| + | |||
| + | |||
| + | === On Windows using PuTTY PuTTYgen === | ||
| + | |||
| + | |||
| + | [[Image:Putty00.png]] | ||
| − | + | [http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html PuTTYgen] can be used to generate the keys, which is described in detail in [http://the.earth.li/~sgtatham/putty/0.53b/htmldoc/Chapter8.html#8.2 Chapter 8.2] | |
| − | |||
1. Select SSH2 RSA. | 1. Select SSH2 RSA. | ||
| − | 2. Press Generate, and generate the key by moving the mouse. | + | 2. Press '''Generate''', and generate the key by moving the mouse. |
| − | 3. Change the Key comment field to something meaningful such as your name. | + | 3. Change the '''Key comment''' field to something meaningful such as your name. |
4. Enter a passphrase which is used to encrypt the key. | 4. Enter a passphrase which is used to encrypt the key. | ||
5. Save the public key. | 5. Save the public key. | ||
| Line 40: | Line 51: | ||
Then paste the OpenSSH2 version to a file, eg putty.pub. | Then paste the OpenSSH2 version to a file, eg putty.pub. | ||
| − | |||
| − | It is possible to use the SME Server itself to generate the public-private key pairs. This is done by using ssh-keygen. | + | === On SME Server === |
| + | |||
| + | |||
| + | It is possible to use the SME Server itself to generate the public-private key pairs. This is done by using [http://www.openbsd.org/cgi-bin/man.cgi?query=ssh-keygen ssh-keygen]. | ||
By default the pair is written to $HOME/.ssh/id_rsa and $HOME/.ssh/id_rsa.pub | By default the pair is written to $HOME/.ssh/id_rsa and $HOME/.ssh/id_rsa.pub | ||
| − | + | ssh-keygen -t rsa | |
| − | Generating public/private rsa key pair. | + | Generating public/private rsa key pair. |
| − | Enter file in which to save the key (/home/e-smith/files/users/dummy/.ssh/id_rsa): [Enter to accept default] | + | Enter file in which to save the key (/home/e-smith/files/users/dummy/.ssh/id_rsa): ''[Enter to accept default]'' |
| − | Created directory '/home/e-smith/files/users/dummy/.ssh'. | + | Created directory '/home/e-smith/files/users/dummy/.ssh'. |
| − | Enter passphrase (empty for no passphrase): [Your passphrase] | + | Enter passphrase (empty for no passphrase): ''[Your passphrase]'' |
| − | Enter same passphrase again: [Your passphrase] | + | Enter same passphrase again: ''[Your passphrase]'' |
| − | Your identification has been saved in /home/e-smith/files/users/dummy/.ssh/id_rsa. | + | Your identification has been saved in /home/e-smith/files/users/dummy/.ssh/id_rsa. |
| − | Your public key has been saved in /home/e-smith/files/users/dummy/.ssh/id_rsa.pub. | + | Your public key has been saved in /home/e-smith/files/users/dummy/.ssh/id_rsa.pub. |
| − | The key fingerprint is: | + | The key fingerprint is: |
| − | aa:bb:cc:dd:ee:ff:aa:bb:cc:dd:ee:ff:aa:bb:cc:dd dummy@gatekeeper | + | aa:bb:cc:dd:ee:ff:aa:bb:cc:dd:ee:ff:aa:bb:cc:dd dummy@gatekeeper |
| − | On RedHat 8.0 | + | === On RedHat 8.0 === |
| − | To generate the public-private key pair on a RedHat 8.0 box is identical to the SME Server, as both use OpenSSH. | + | To generate the public-private key pair on a RedHat 8.0 box is identical to the SME Server, as both use [http://www.openssh.com/ OpenSSH]. |
| − | In this example I have specified the comment field. | + | In this example I have specified the '''comment field'''. |
| − | + | ssh-keygen -t rsa '''-C dummy@rh8''' | |
| − | Generating public/private rsa key pair. | + | Generating public/private rsa key pair. |
| − | Enter file in which to save the key (/home/dummy/.ssh/id_rsa): | + | Enter file in which to save the key (/home/dummy/.ssh/id_rsa): |
| − | Enter passphrase (empty for no passphrase): | + | Enter passphrase (empty for no passphrase): |
| − | Enter same passphrase again: | + | Enter same passphrase again: |
| − | Your identification has been saved in /home/dummy/.ssh/id_rsa. | + | Your identification has been saved in /home/dummy/.ssh/id_rsa. |
| − | Your public key has been saved in /home/dummy/.ssh/id_rsa.pub. | + | Your public key has been saved in /home/dummy/.ssh/id_rsa.pub. |
| − | The key fingerprint is: | + | The key fingerprint is: |
| − | aa:bb:cc:dd:ee:ff:aa:bb:cc:dd:ee:ff:aa:bb:cc:dd dummy@rh8 | + | aa:bb:cc:dd:ee:ff:aa:bb:cc:dd:ee:ff:aa:bb:cc:dd '''dummy@rh8''' |
| − | Installing the Public Key onto the Server | + | == Installing the Public Key onto the Server == |
To make use of the Public-Private Key pair the Public keys must be put onto the server that will be accessed. The Public Key file and its contents do not need to be kept secret. | To make use of the Public-Private Key pair the Public keys must be put onto the server that will be accessed. The Public Key file and its contents do not need to be kept secret. | ||
| − | The Public Key needs to be saved in the file $HOME/.ssh/authorized_keys . For the user dummy on an SME Server it would be: | + | The Public Key needs to be saved in the file $HOME/.ssh/authorized_keys . For the user '''dummy''' on an SME Server it would be: |
| − | /home/e-smith/files/users/dummy/.ssh/authorized_keys | + | /home/e-smith/files/users/'''dummy'''/.ssh/authorized_keys |
The directory .ssh should have permissions 700 and the file authorized_keys should have permissions either 644 or 600. If the directory does not exist it can be created as follows, which presumes that you are logged in as yourself, not root. | The directory .ssh should have permissions 700 and the file authorized_keys should have permissions either 644 or 600. If the directory does not exist it can be created as follows, which presumes that you are logged in as yourself, not root. | ||
| − | + | cd | |
| − | + | mkdir .ssh | |
| − | + | chmod 700 .ssh | |
| − | + | ls -al | |
| − | drwx------ 2 dummy dummy 4096 Feb 18 11:23 .ssh | + | drwx------ 2 dummy dummy 4096 Feb 18 11:23 .ssh |
The authorized_keys file can store multiple public keys, one on each line, so the following examples always append to the end of the file. | The authorized_keys file can store multiple public keys, one on each line, so the following examples always append to the end of the file. | ||
| − | Public key from OpenSSH | + | |
| + | === Public key from OpenSSH === | ||
Copying the Public Key generated by ssh-keygen, $HOME/.ssh/id_rsa.pub | Copying the Public Key generated by ssh-keygen, $HOME/.ssh/id_rsa.pub | ||
This example presumes that the key was generated on the server, or has been copied into the $HOME/.ssh directory. | This example presumes that the key was generated on the server, or has been copied into the $HOME/.ssh directory. | ||
| − | + | cat id_rsa.pub >> authorized_keys | |
| − | + | ls -l | |
| − | -rw-r--r-- 1 dummy dummy 225 Feb 18 11:26 authorized_keys | + | -rw-r--r-- 1 dummy dummy 225 Feb 18 11:26 authorized_keys |
| − | Public key from PuTTYgen | + | === Public key from PuTTYgen === |
| − | There are two main ways of doing this, they each require that the "Public key for pasting into authorized_keys file" is copied to the clipboard (see Step 7 on the figure above). For more details read the PuTTY manual. | + | There are two main ways of doing this, they each require that the "Public key for pasting into authorized_keys file" is copied to the clipboard (see Step 7 on the figure above). For more details read the [http://the.earth.li/~sgtatham/putty/0.53b/htmldoc/Chapter8.html#8.2 PuTTY manual]. |
| − | One method is to paste the key into a file (putty.pub in the example below). | + | One method is to paste the key into a file ('''putty.pub''' in the example below). |
Then copy this file into the $HOME/.ssh directory on the server. This file can then be appended to the authorized_keys file. | Then copy this file into the $HOME/.ssh directory on the server. This file can then be appended to the authorized_keys file. | ||
| − | + | cat '''putty.pub''' >> authorized_keys | |
The other method is simpler but more complicated to explain. | The other method is simpler but more complicated to explain. | ||
| − | + | *Open a PuTTY terminal to the server | |
| − | + | *Open the $HOME/.ssh/authorized_keys file with your favourite text editor (vi, pico etc) | |
| − | + | *Paste in the public key from the clipboard | |
| − | Installing the Private Key onto the Clients | + | == Installing the Private Key onto the Clients == |
The Private Key needs to be accessible from the clients that you use. The Private Key file should be kept secure, and should be protected by a pass phrase. | The Private Key needs to be accessible from the clients that you use. The Private Key file should be kept secure, and should be protected by a pass phrase. | ||
Private Key files cannot be directly shared between PuTTY and OpenSSH, however PuTTYgen can convert the files. | Private Key files cannot be directly shared between PuTTY and OpenSSH, however PuTTYgen can convert the files. | ||
| − | |||
| − | 1. Either press Load, or from the Conversions menu select Import Key. | + | === Converting the OpenSSH Private Key to work with PuTTY === |
| − | 2. Change the Files of Type to All Files | + | |
| + | 1. Either press ''Load'', or from the ''Conversions'' menu select ''Import Key''. | ||
| + | 2. Change the ''Files of Type'' to ''All Files'' | ||
3. Select the Private Key, id_rsa, that was created with ssh-keygen. | 3. Select the Private Key, id_rsa, that was created with ssh-keygen. | ||
4. Enter the passphrase to load the key. | 4. Enter the passphrase to load the key. | ||
| − | 5. The Key comment may be changed at this time. | + | 5. The ''Key comment'' may be changed at this time. |
6. Save the private key. | 6. Save the private key. | ||
| − | Converting the PuTTY Private Key to work with OpenSSH | + | === Converting the PuTTY Private Key to work with OpenSSH === |
| − | 1. Press Load and select the Private Key that was created with PuTTYgen. | + | 1. Press ''Load'' and select the Private Key that was created with PuTTYgen. |
2. Enter the passphrase to load the key. | 2. Enter the passphrase to load the key. | ||
| − | 3. From the Conversions menu select export OpenSSH key | + | 3. From the ''Conversions'' menu select export OpenSSH key |
4. Save the private key. | 4. Save the private key. | ||
| − | Using public keys for SSH authentication | + | == Using public keys for SSH authentication == |
In these examples the server is the SME Server, and the clients will be Windows and RedHat 8.0 | In these examples the server is the SME Server, and the clients will be Windows and RedHat 8.0 | ||
| − | |||
| − | + | === In use with PuTTY === | |
| − | To use the Private Key go to the PuTTY Configuration and select the | + | To start using PuTTY with SME Server see [http://www.carrollweb.net/putty/putty-howto.html Tom Carroll's HowTo] (Link broken 12-30-2023). [https://www.techtarget.com/searchsecurity/tutorial/How-to-use-PuTTY-for-SSH-key-based-authentication How To Use Putty] is a basic tutorial. |
| − | Then in the Private key file for authentication: enter the path to the private key file, or find it using Browse. | + | |
| + | To use the Private Key go to the PuTTY Configuration and select the Connectio/n - SSH - Auth. | ||
| + | Then in the ''Private key file for authentication'': enter the path to the private key file, or find it using ''Browse''. | ||
When starting the PuTTY terminal the following is shown. You will need to enter the passphrase, if one was set. | When starting the PuTTY terminal the following is shown. You will need to enter the passphrase, if one was set. | ||
| − | Using username "dummy". | + | Using username "dummy". |
| − | Authenticating with public key "dummy@homepc" Using the private key generated on my windows machine | + | Authenticating with public key "dummy@homepc" '''Using the private key generated on my windows machine''' |
| − | Passphrase for key "dummy@homepc": | + | Passphrase for key "dummy@homepc": |
| − | Welcome to the Mitel Networks SME Server. | + | Welcome to the Mitel Networks SME Server. |
| − | Using username "dummy". | + | Using username "dummy". |
| − | Authenticating with public key "dummy@gatekeeper" Using the private key generated on my SME Server | + | Authenticating with public key "dummy@gatekeeper" '''Using the private key generated on my SME Server''' |
| − | Passphrase for key "dummy@gatekeeper": | + | Passphrase for key "dummy@gatekeeper": |
| − | Welcome to the Mitel Networks SME Server. | + | Welcome to the Mitel Networks SME Server. |
| − | In use with OpenSSH | + | === In use with OpenSSH === |
This brief example shows the start of a SSH session where the username is specified using the -l option. | This brief example shows the start of a SSH session where the username is specified using the -l option. | ||
| − | + | ssh -l dummy gatekeeper | |
| − | Enter passphrase for key '/home/dummy/.ssh/id_rsa': | + | Enter passphrase for key '/home/dummy/.ssh/id_rsa': |
| − | Last login: Tue Feb 18 11:38:43 2003 from somewhere | + | Last login: Tue Feb 18 11:38:43 2003 from somewhere |
| − | Welcome to the Mitel Networks SME Server. | + | Welcome to the Mitel Networks SME Server. |
| − | bash-2.05a$ | + | bash-2.05a$ |
| + | |||
| + | |||
| + | == Changes on remote-access panel == | ||
| + | -access SERVER-MANAGER | ||
| + | -click REMOTE ACCESS (on left-hand side) | ||
| + | -change "Secure Shell Access" to ALLOW PUBLIC ACCESS | ||
| + | -change "Allow administrative command line..." to YES | ||
| + | -change "Allow secure shell using..." to NO | ||
| + | |||
| + | == Further Information == | ||
| + | |||
| − | + | === OpenSSH Files === | |
| − | OpenSSH Files | ||
| − | Files used by OpenSSH, full details can be found from the ssh-keygen (1) and sshd (8) manual pages. | + | Files used by [http://www.openssh.com/ OpenSSH], full details can be found from the [http://www.openbsd.org/cgi-bin/man.cgi?query=ssh-keygen ssh-keygen (1)] and [http://www.openbsd.org/cgi-bin/man.cgi?query=sshd sshd (8)] manual pages. |
| − | $HOME/.ssh/id_rsa | + | '''$HOME/.ssh/id_rsa''' |
This is the private key, it contains the protocol version 2 RSA authentication identity of the user. This file should not be readable by anyone but the user. | This is the private key, it contains the protocol version 2 RSA authentication identity of the user. This file should not be readable by anyone but the user. | ||
| − | $HOME/.ssh/id_rsa.pub | + | '''$HOME/.ssh/id_rsa.pub''' |
Contains the protocol version 2 RSA public key for authentication. The contents of this file should be added to the authorized_keys file on all machines where the user wishes to log in using public key authentication. There is no need to keep the contents of this file secret. | Contains the protocol version 2 RSA public key for authentication. The contents of this file should be added to the authorized_keys file on all machines where the user wishes to log in using public key authentication. There is no need to keep the contents of this file secret. | ||
| − | $HOME/.ssh/authorized_keys | + | '''$HOME/.ssh/authorized_keys''' |
Lists the public keys that can be used to log into the user's account. This file must be readable by root. It is recommended that it not be accessible by others. | Lists the public keys that can be used to log into the user's account. This file must be readable by root. It is recommended that it not be accessible by others. | ||
| − | Each line of the file contains one key (empty lines and lines starting with a `#' are ignored as comments). Each protocol version 2 public key consists of: options, key-type, base64 encoded key, comment. The comment field is not used for anything (but may be convenient for the user to identify the key). | + | Each line of the file contains one key (empty lines and lines starting with a `#' are ignored as comments). Each protocol version 2 public key consists of: options, key-type, base64 encoded key, comment. The comment field is not used for anything (but may be convenient for the user to identify the key)./ |
| − | Changing the passphrase | + | |
| + | === Changing the passphrase === | ||
| + | |||
| + | '''OpenSSH''' | ||
| − | |||
You can change the passphrase at any time by using the -p option of ssh-keygen. | You can change the passphrase at any time by using the -p option of ssh-keygen. | ||
| − | + | ssh-keygen -p | |
| − | Enter file in which the key is (/home/e-smith/files/users/dummy/.ssh/id_rsa): [Enter to accept default key file] | + | |
| − | Enter old passphrase: [Old passphrase] | + | Enter file in which the key is (/home/e-smith/files/users/dummy/.ssh/id_rsa): '''[Enter to accept default key file]''' |
| − | Key has comment '/home/e-smith/files/users/dummy/.ssh/id_rsa' | + | Enter old passphrase: '''[Old passphrase]''' |
| − | Enter new passphrase (empty for no passphrase): [New passphrase] | + | Key has comment '/home/e-smith/files/users/dummy/.ssh/id_rsa' |
| − | Enter same passphrase again: [New passphrase] | + | Enter new passphrase (empty for no passphrase): '''[New passphrase]''' |
| − | Your identification has been saved with the new passphrase. | + | Enter same passphrase again: '''[New passphrase]''' |
| + | Your identification has been saved with the new passphrase. | ||
| + | |||
| + | '''PuTTY''' | ||
| − | |||
To change the passphrase of a PuTTY key use PuTTYgen. | To change the passphrase of a PuTTY key use PuTTYgen. | ||
| − | + | 1. Load the Private Key | |
| − | + | 2. Type the new passphrase into Key Passphrase and Confirm Passphrase | |
| − | + | 3. Save the Private Key | |
Copyright © 2003 Ian Wells : The original can be found from http://www.wellsi.com/sme : Please send additions & corrections to me. | Copyright © 2003 Ian Wells : The original can be found from http://www.wellsi.com/sme : Please send additions & corrections to me. | ||
| + | |||
| + | ---- | ||
Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Text and no Back-Cover Text. A copy of the GNU Free Documentation License is available from the Free Software Foundation at http://www.fsf.org/copyleft/fdl.html. | Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Text and no Back-Cover Text. A copy of the GNU Free Documentation License is available from the Free Software Foundation at http://www.fsf.org/copyleft/fdl.html. | ||
| + | |||
| + | ---- | ||
| + | [[Category:Howto]] | ||
| + | [[Category:Administration:Remote Access]] | ||
Latest revision as of 00:18, 31 December 2023
Extracted From: http://www.wellsi.com/sme/ssh/ssh.html
Author: Ian Wells (27th December 2003)
Introduction
This is an introduction to using Public-Private Keys as applied to SSH. It has been written in response to questions regarding my CVS How-To.
It currently covers the first three steps needed to use Public-Private keys
- Generate Public-Private Key Pairs
- Installing the Public Key onto the Server
- Installing the Private Key onto the Clients
It also has sections on
- Using public keys for SSH authentication
- Further Information
The following has been tested using a Mitel SME Server, and Windows XP& RedHat 8.0 clients.
Some sections use PuTTY to connect to the server, it is a free implementation of SSH for Win32 platforms, with extensive online documentation.
Generate Public-Private Key Pairs
This section describes three ways to generate the public-private key pairs, and specifically a SSH protocol 2 RSA key pair.
- 1. On Windows using PuTTY
- 2. On SME Server using OpenSSH
- 3. On RedHat 8.0 using OpenSSH
On Windows using PuTTY PuTTYgen
PuTTYgen can be used to generate the keys, which is described in detail in Chapter 8.2
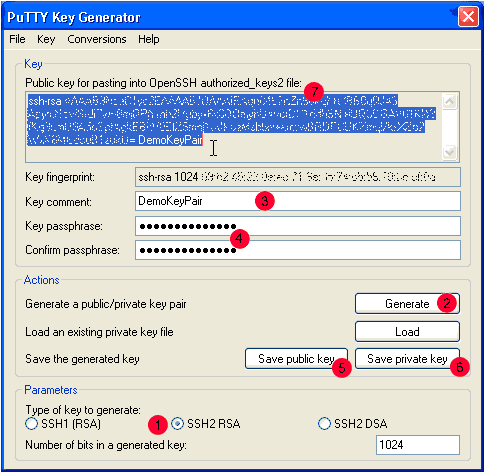
1. Select SSH2 RSA.
2. Press Generate, and generate the key by moving the mouse.
3. Change the Key comment field to something meaningful such as your name.
4. Enter a passphrase which is used to encrypt the key.
5. Save the public key.
6. Save the private key.
7. To save the public key in the OpenSSH2 format.
Select all of the text as shown, and copy to the clipboard
(CTRL-C, or CTRL-Insert or Right-Click Copy).
Then paste the OpenSSH2 version to a file, eg putty.pub.
On SME Server
It is possible to use the SME Server itself to generate the public-private key pairs. This is done by using ssh-keygen. By default the pair is written to $HOME/.ssh/id_rsa and $HOME/.ssh/id_rsa.pub
ssh-keygen -t rsa
Generating public/private rsa key pair. Enter file in which to save the key (/home/e-smith/files/users/dummy/.ssh/id_rsa): [Enter to accept default] Created directory '/home/e-smith/files/users/dummy/.ssh'. Enter passphrase (empty for no passphrase): [Your passphrase] Enter same passphrase again: [Your passphrase] Your identification has been saved in /home/e-smith/files/users/dummy/.ssh/id_rsa. Your public key has been saved in /home/e-smith/files/users/dummy/.ssh/id_rsa.pub. The key fingerprint is: aa:bb:cc:dd:ee:ff:aa:bb:cc:dd:ee:ff:aa:bb:cc:dd dummy@gatekeeper
On RedHat 8.0
To generate the public-private key pair on a RedHat 8.0 box is identical to the SME Server, as both use OpenSSH. In this example I have specified the comment field.
ssh-keygen -t rsa -C dummy@rh8
Generating public/private rsa key pair. Enter file in which to save the key (/home/dummy/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /home/dummy/.ssh/id_rsa. Your public key has been saved in /home/dummy/.ssh/id_rsa.pub. The key fingerprint is: aa:bb:cc:dd:ee:ff:aa:bb:cc:dd:ee:ff:aa:bb:cc:dd dummy@rh8
Installing the Public Key onto the Server
To make use of the Public-Private Key pair the Public keys must be put onto the server that will be accessed. The Public Key file and its contents do not need to be kept secret.
The Public Key needs to be saved in the file $HOME/.ssh/authorized_keys . For the user dummy on an SME Server it would be:
/home/e-smith/files/users/dummy/.ssh/authorized_keys
The directory .ssh should have permissions 700 and the file authorized_keys should have permissions either 644 or 600. If the directory does not exist it can be created as follows, which presumes that you are logged in as yourself, not root.
cd mkdir .ssh chmod 700 .ssh ls -al drwx------ 2 dummy dummy 4096 Feb 18 11:23 .ssh
The authorized_keys file can store multiple public keys, one on each line, so the following examples always append to the end of the file.
Public key from OpenSSH
Copying the Public Key generated by ssh-keygen, $HOME/.ssh/id_rsa.pub This example presumes that the key was generated on the server, or has been copied into the $HOME/.ssh directory.
cat id_rsa.pub >> authorized_keys ls -l -rw-r--r-- 1 dummy dummy 225 Feb 18 11:26 authorized_keys
Public key from PuTTYgen
There are two main ways of doing this, they each require that the "Public key for pasting into authorized_keys file" is copied to the clipboard (see Step 7 on the figure above). For more details read the PuTTY manual.
One method is to paste the key into a file (putty.pub in the example below). Then copy this file into the $HOME/.ssh directory on the server. This file can then be appended to the authorized_keys file.
cat putty.pub >> authorized_keys
The other method is simpler but more complicated to explain.
- Open a PuTTY terminal to the server
- Open the $HOME/.ssh/authorized_keys file with your favourite text editor (vi, pico etc)
- Paste in the public key from the clipboard
Installing the Private Key onto the Clients
The Private Key needs to be accessible from the clients that you use. The Private Key file should be kept secure, and should be protected by a pass phrase.
Private Key files cannot be directly shared between PuTTY and OpenSSH, however PuTTYgen can convert the files.
Converting the OpenSSH Private Key to work with PuTTY
1. Either press Load, or from the Conversions menu select Import Key. 2. Change the Files of Type to All Files 3. Select the Private Key, id_rsa, that was created with ssh-keygen. 4. Enter the passphrase to load the key. 5. The Key comment may be changed at this time. 6. Save the private key.
Converting the PuTTY Private Key to work with OpenSSH
1. Press Load and select the Private Key that was created with PuTTYgen. 2. Enter the passphrase to load the key. 3. From the Conversions menu select export OpenSSH key 4. Save the private key.
Using public keys for SSH authentication
In these examples the server is the SME Server, and the clients will be Windows and RedHat 8.0
In use with PuTTY
To start using PuTTY with SME Server see Tom Carroll's HowTo (Link broken 12-30-2023). How To Use Putty is a basic tutorial.
To use the Private Key go to the PuTTY Configuration and select the Connectio/n - SSH - Auth. Then in the Private key file for authentication: enter the path to the private key file, or find it using Browse.
When starting the PuTTY terminal the following is shown. You will need to enter the passphrase, if one was set.
Using username "dummy". Authenticating with public key "dummy@homepc" Using the private key generated on my windows machine Passphrase for key "dummy@homepc": Welcome to the Mitel Networks SME Server.
Using username "dummy". Authenticating with public key "dummy@gatekeeper" Using the private key generated on my SME Server Passphrase for key "dummy@gatekeeper": Welcome to the Mitel Networks SME Server.
In use with OpenSSH
This brief example shows the start of a SSH session where the username is specified using the -l option.
ssh -l dummy gatekeeper Enter passphrase for key '/home/dummy/.ssh/id_rsa': Last login: Tue Feb 18 11:38:43 2003 from somewhere Welcome to the Mitel Networks SME Server. bash-2.05a$
Changes on remote-access panel
-access SERVER-MANAGER -click REMOTE ACCESS (on left-hand side) -change "Secure Shell Access" to ALLOW PUBLIC ACCESS -change "Allow administrative command line..." to YES -change "Allow secure shell using..." to NO
Further Information
OpenSSH Files
Files used by OpenSSH, full details can be found from the ssh-keygen (1) and sshd (8) manual pages.
$HOME/.ssh/id_rsa This is the private key, it contains the protocol version 2 RSA authentication identity of the user. This file should not be readable by anyone but the user.
$HOME/.ssh/id_rsa.pub Contains the protocol version 2 RSA public key for authentication. The contents of this file should be added to the authorized_keys file on all machines where the user wishes to log in using public key authentication. There is no need to keep the contents of this file secret.
$HOME/.ssh/authorized_keys Lists the public keys that can be used to log into the user's account. This file must be readable by root. It is recommended that it not be accessible by others.
Each line of the file contains one key (empty lines and lines starting with a `#' are ignored as comments). Each protocol version 2 public key consists of: options, key-type, base64 encoded key, comment. The comment field is not used for anything (but may be convenient for the user to identify the key)./
Changing the passphrase
OpenSSH
You can change the passphrase at any time by using the -p option of ssh-keygen.
ssh-keygen -p
Enter file in which the key is (/home/e-smith/files/users/dummy/.ssh/id_rsa): [Enter to accept default key file] Enter old passphrase: [Old passphrase] Key has comment '/home/e-smith/files/users/dummy/.ssh/id_rsa' Enter new passphrase (empty for no passphrase): [New passphrase] Enter same passphrase again: [New passphrase] Your identification has been saved with the new passphrase.
PuTTY
To change the passphrase of a PuTTY key use PuTTYgen.
1. Load the Private Key 2. Type the new passphrase into Key Passphrase and Confirm Passphrase 3. Save the Private Key
Copyright © 2003 Ian Wells : The original can be found from http://www.wellsi.com/sme : Please send additions & corrections to me.
Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Text and no Back-Cover Text. A copy of the GNU Free Documentation License is available from the Free Software Foundation at http://www.fsf.org/copyleft/fdl.html.