Difference between revisions of "PHPki"
m |
|||
| (55 intermediate revisions by 11 users not shown) | |||
| Line 1: | Line 1: | ||
| − | {{Languages}} | + | {{Languages|PHPki}} |
| + | |||
| + | {{Note box| For v10 we have created a new update version of PHPKi called PHPKi-ng with fixes and higher security defaults. If you used the previous version you will need to create a new CA and certificates. We have imported the original version to contribs if you really need to use it, but it is not recommended, and will not be generally released.}} | ||
===Maintainer=== | ===Maintainer=== | ||
| − | [[User:VIP-ire|Daniel B.]] | + | Previous: |
| − | [http://www.firewall-services.com Firewall Services] | + | [mailto:daniel@firewall-services.com][[User:VIP-ire|Daniel B.]] from [http://www.firewall-services.com Firewall Services] |
| − | + | ||
| + | Now maintained by Koozali SME | ||
=== Version === | === Version === | ||
| + | Old version prior SME10:smeserver-phpki and phpki | ||
| + | |||
| + | New Version: | ||
| + | |||
| + | {{#smeversion: smeserver-phpki-ng }} | ||
| + | {{#smeversion: phpki-ng }} | ||
| − | + | Please follow the installation instructions below. The installation instructions will satisfy all dependencies and the latest versions of the above 2 RPMs will be installed automatically. | |
| − | |||
=== Description === | === Description === | ||
| − | [http://sourceforge.net/projects/phpki/ PHPki] is an Open Source Web application for managing a multi-agency PKI for HIPAA compliance. With it, you may create and centrally manage X.509 certificates for use with S/MIME enabled e-mail clients, SSL servers, and VPN applications. | + | [http://sourceforge.net/projects/phpki/ PHPki] is an Open Source Web application for managing a multi-agency PKI for HIPAA compliance. With it, you may create and centrally manage X.509 certificates for use with S/MIME enabled e-mail clients, SSL servers, and VPN applications. PHPki is now used to manage certificates with the latest release of the [[OpenVPN_Bridge|SME Server OpenVPN Bridge contrib]]. |
| + | |||
| + | You can see a demo installation [http://phpki.sourceforge.net/phpki/ here.] | ||
| + | |||
| + | === Requirements === | ||
| + | {{Warning box|This version of PHPki is a slightly modified version, so it can be used with certificates generated with previous release of smeserver-openvpn-bridge, plus some others minor modifications. | ||
| + | Starting phpki-ng-0.84, default_md has been upgraded to sha512 (previous was sha1). You can keep your existing CA working, but we strongly advise you to upgrade to a new instance, as the weak sha1 hash is a security issue. | ||
| + | }} | ||
| + | |||
| + | === Installation === | ||
| − | + | {{Warning box| If openvpn is not detected PHPKi cannot generate a TA Key and it should advise you during install. To generate a TA Key once you have openvpn installed do this (assuming this is the correct directory) | |
| + | openvpn --genkey --secret /opt/phpki/phpki-store/CA/private/takey.pem | ||
| + | chown phpki:phpki /opt/phpki/phpki-store/CA/private/takey.pem}} | ||
| − | + | <tabs container><tab name="SME 10"> | |
| + | *install the rpms | ||
| + | yum --enablerepo=smecontribs install smeserver-phpki-ng | ||
| − | + | go to the server-manager to the manage certificate menu and start creating your CA certificate | |
| − | + | ||
| + | Warning click only once and wait for the page to update it can be very long to create the 4096 certificate... | ||
| − | + | </tab> | |
| − | + | <tab name="SME 9"> | |
| + | you have to enable the [[epel]] repository | ||
| + | *install the rpms | ||
| + | yum --enablerepo=smecontribs,epel install smeserver-phpki | ||
| + | *and start/restart needed services: | ||
| + | expand-template /etc/httpd/conf/httpd.conf | ||
| + | expand-template /etc/httpd/pki-conf/httpd.conf | ||
| + | sv t /service/httpd-e-smith | ||
| + | sv u /service/httpd-pki | ||
| − | + | * alternatively issue the following : | |
| − | + | signal-event post-upgrade; signal-event reboot | |
| − | + | on update you can issue | |
| + | expand-template /etc/httpd/conf/httpd.conf | ||
| + | expand-template /etc/httpd/pki-conf/httpd.conf | ||
| + | sv t /service/httpd-e-smith | ||
| + | sv t /service/httpd-pki | ||
| − | |||
| + | </tab> | ||
| + | <tab name="SME 8"> | ||
| + | For sme8 | ||
| + | *install the rpms | ||
yum --enablerepo=smecontribs install smeserver-phpki | yum --enablerepo=smecontribs install smeserver-phpki | ||
| + | |||
| + | *and start/restart needed services: | ||
expand-template /etc/httpd/conf/httpd.conf | expand-template /etc/httpd/conf/httpd.conf | ||
expand-template /etc/httpd/pki-conf/httpd.conf | expand-template /etc/httpd/pki-conf/httpd.conf | ||
| Line 39: | Line 78: | ||
sv u /service/httpd-pki | sv u /service/httpd-pki | ||
| + | * alternatively issue the following : | ||
| + | signal-event post-upgrade; signal-event reboot | ||
| + | </tab> | ||
| + | </tabs> | ||
| − | + | === Configure your new PKI === | |
Go in the server-manager, you'll find a new "Manage Certificates" menu (or you can use the URL https://server.domain.tld/phpki/ca) | Go in the server-manager, you'll find a new "Manage Certificates" menu (or you can use the URL https://server.domain.tld/phpki/ca) | ||
| Line 57: | Line 100: | ||
**URL of your PKI (https://my.domain.tld/phpki) | **URL of your PKI (https://my.domain.tld/phpki) | ||
| − | + | These two screenshots illustrate the first (and the most important) part of this configuration page: | |
| + | |||
| + | [[File:PHPki_CA_initial_setup_data_part_1.png|768px|thumb|center|First part of the initiale configuration page (above)]] | ||
| + | |||
| + | [[File:PHPki_CA_initial_setup_data_part_2.png|768px|thumb|center|First part of the initiale configuration page (low)]] | ||
| + | |||
| + | The second part is like this: | ||
| + | |||
| + | [[File:PHPki_CA_initial_setup_options.png|768px|thumb|center|Second part of the initiale configuration page]] | ||
| + | |||
| + | The default settings should be OK for most installations. You may just want to change the "Help Document Contact Info" part. | ||
| + | |||
| + | Once you have submitted this form (which can take several minutes, '''be patient''', as generating dh parameters can take a long time), you should have something like this: | ||
| + | |||
| + | |||
| + | [[File:Phpki_init_finish.png|768px|thumb|center|Second part of the initiale configuration page]] | ||
| − | + | Now you'll be able to start using PHPki. It's quite easy to use. | |
The administrative interface is available on the server-manager or directly https://my.domain.tld/phpki/ca | The administrative interface is available on the server-manager or directly https://my.domain.tld/phpki/ca | ||
| Line 66: | Line 124: | ||
Here, users can download the Master CA certificate, the CRL, or search for certificates of other users (public part only of course). | Here, users can download the Master CA certificate, the CRL, or search for certificates of other users (public part only of course). | ||
| − | {{ | + | {{Note box|If you just installed the [[OpenVPN_Bridge]] contrib and are installing PHPki as suggested by the wiki page, or you just want to use [[PHPki]] without [[OpenVPN_Bridge]] contrib, then you are done here, and you don't have to migrate any certificates}} |
| + | {{Note box|starting phpki-ng-0.84-14 new URL are available to access your CRL and request for certificate status | ||
| − | + | http://www.somewhere.com/phpki/ns_revoke_query.php? | |
| − | + | http://www.somewhere.com/phpki/dl_crl.php}} | |
| − | + | === Add another admin === | |
| − | + | if you happen to need to delegate certificate generation, you can use user-panel to add access to the panel, but you will also need to add the user manually to phpki config | |
| − | + | edit /opt/phpki/phpki-store/config/config.php<syntaxhighlight lang="php"> | |
| + | #$PHPki_admins = Array(md5('admin')); | ||
| + | $PHPki_admins = Array(md5('admin'),md5('user2')); | ||
| − | + | </syntaxhighlight> | |
| − | + | === Uninstall === | |
| + | To uninstall the contrib from your server, just run the following commands: | ||
| + | yum remove smeserver-phpki-ng phpki-ng | ||
| + | expand-template /etc/httpd/conf/httpd.conf | ||
| + | systemctl restart /service/httpd-e-smith | ||
| + | {{Note box|As with many other rpms, removing phpki won't remove everything from your server. Especially certificates will be kept, and some php files. PHPKi-ng will attempt to backup any old certificates. | ||
| + | }} | ||
| − | + | Certificates and PKI configuration are stored in /opt/phpki/phpki-store, php files are in /opt/phpki/html | |
| − | + | {{Warning box|To start from scratch after uninstallation you need to get rid of the html and pkpki-store directories before reinstalling. | |
| − | + | The files in phpki-store can be very important, so my recommendation is to let them remain here. If you really want to remove them, just backup them before: | |
| − | + | cd /opt/phpki | |
| − | + | tar cvzf ~/phpki-backup.tar.gz ./ | |
| − | + | Now you can remove the entire /opt/phpki directory | |
| − | + | rm /opt/phpki/{html,phpki-store} -rf | |
| − | + | }} | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| + | === Re-install === | ||
| − | + | ==== before phpki-ng 0.84-14 ==== | |
| + | If you have removed the contrib, and want to re-install it keeping your previous CA (assuming you restored /opt/phpki), you'll need to follow these steps after you have installed the rpms: | ||
| − | + | cd /opt/phpki/html/ | |
| − | + | rm -f index.php | |
| − | + | rm -f setup.php | |
| − | + | ln -s main.php index.php | |
| + | cat config.php.rpmsave > config.php | ||
| + | cd ca | ||
| + | rm -f index.php | ||
| + | ln -s main.php index.php | ||
| + | cd /opt/phpki/ | ||
| + | chown phpki:phpki -R phpki-store | ||
| + | chown root:phpki -R html/config.php | ||
=== Bugs === | === Bugs === | ||
| − | Please raise bugs under the SME-Contribs section in [http://bugs.contribs.org/enter_bug.cgi bugzilla] | + | Please raise bugs under the SME-Contribs section in [http://bugs.contribs.org/enter_bug.cgi bugzilla]. |
| − | + | ||
| + | ====smeserver-phpki-ng==== | ||
| + | |||
| + | For the new smeserver-phpki-ng, select the smeserver-phpki-ng component or use {{BugzillaFileBug|product=SME%20Contribs|component=smeserver-phpki-ng|title=this link}} | ||
| + | |||
| + | {{#bugzilla:columns=id,product,version,status,summary |sort=id |order=desc |component=smeserver-phpki-ng|noresultsmessage="No open bugs found."}} | ||
| + | |||
| + | |||
| + | ====phpki-ng==== | ||
| + | |||
| + | For the new phpki-ng itself select the phpki-ng component or use {{BugzillaFileBug|product=SME%20Contribs|component=phpki-ng|title=this link}} | ||
| + | |||
| + | {{#bugzilla:columns=id,product,version,status,summary |sort=id |order=desc |component=phpki-ng|noresultsmessage="No open bugs found."}} | ||
| + | |||
| + | === Changelog === | ||
| + | Only released version in smecontrib are listed here. | ||
| + | {{#smechangelog:smeserver-phpki-ng}} | ||
| + | {{#smechangelog:phpki-ng}} | ||
---- | ---- | ||
[[Category:Contrib]] | [[Category:Contrib]] | ||
| + | [[Category:Administration:Certificates]] | ||
Latest revision as of 20:30, 25 October 2023
Maintainer
Previous: [1]Daniel B. from Firewall Services
Now maintained by Koozali SME
Version
Old version prior SME10:smeserver-phpki and phpki
New Version:
Please follow the installation instructions below. The installation instructions will satisfy all dependencies and the latest versions of the above 2 RPMs will be installed automatically.
Description
PHPki is an Open Source Web application for managing a multi-agency PKI for HIPAA compliance. With it, you may create and centrally manage X.509 certificates for use with S/MIME enabled e-mail clients, SSL servers, and VPN applications. PHPki is now used to manage certificates with the latest release of the SME Server OpenVPN Bridge contrib.
You can see a demo installation here.
Requirements
Installation
- install the rpms
yum --enablerepo=smecontribs install smeserver-phpki-ng
go to the server-manager to the manage certificate menu and start creating your CA certificate
Warning click only once and wait for the page to update it can be very long to create the 4096 certificate...
you have to enable the epel repository
- install the rpms
yum --enablerepo=smecontribs,epel install smeserver-phpki
- and start/restart needed services:
expand-template /etc/httpd/conf/httpd.conf expand-template /etc/httpd/pki-conf/httpd.conf sv t /service/httpd-e-smith sv u /service/httpd-pki
- alternatively issue the following :
signal-event post-upgrade; signal-event reboot
on update you can issue
expand-template /etc/httpd/conf/httpd.conf expand-template /etc/httpd/pki-conf/httpd.conf sv t /service/httpd-e-smith sv t /service/httpd-pki
For sme8
- install the rpms
yum --enablerepo=smecontribs install smeserver-phpki
- and start/restart needed services:
expand-template /etc/httpd/conf/httpd.conf expand-template /etc/httpd/pki-conf/httpd.conf sv t /service/httpd-e-smith sv u /service/httpd-pki
- alternatively issue the following :
signal-event post-upgrade; signal-event reboot
Configure your new PKI
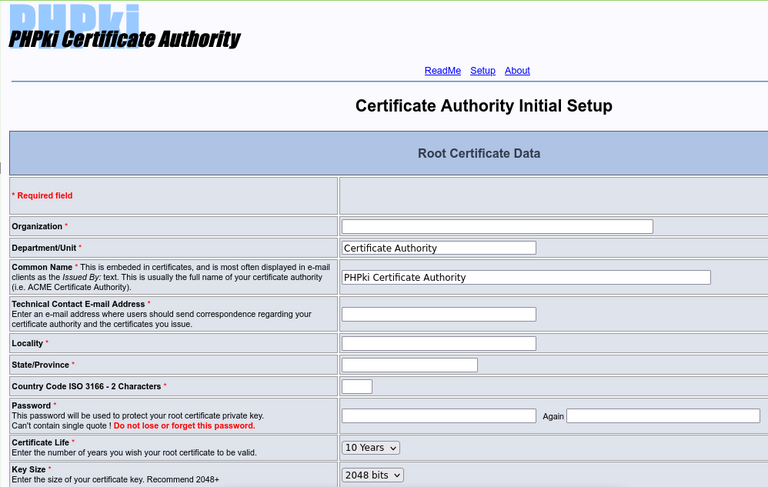
Go in the server-manager, you'll find a new "Manage Certificates" menu (or you can use the URL https://server.domain.tld/phpki/ca) Here you have to enter the following informations:
- Organisation
- Department
- Common Name of the Master CA
- E-mail (technical contact)
- City
- State
- Country Code
- Password (to protect the private key of the Master CA)
- Validity of the CA
- Keys size
- URL of your PKI (https://my.domain.tld/phpki)
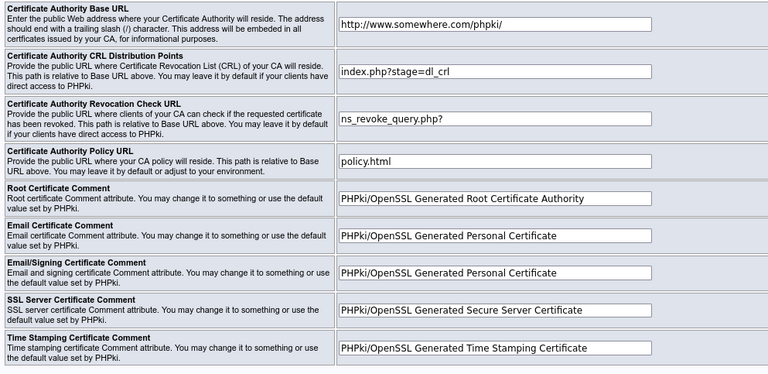
These two screenshots illustrate the first (and the most important) part of this configuration page:
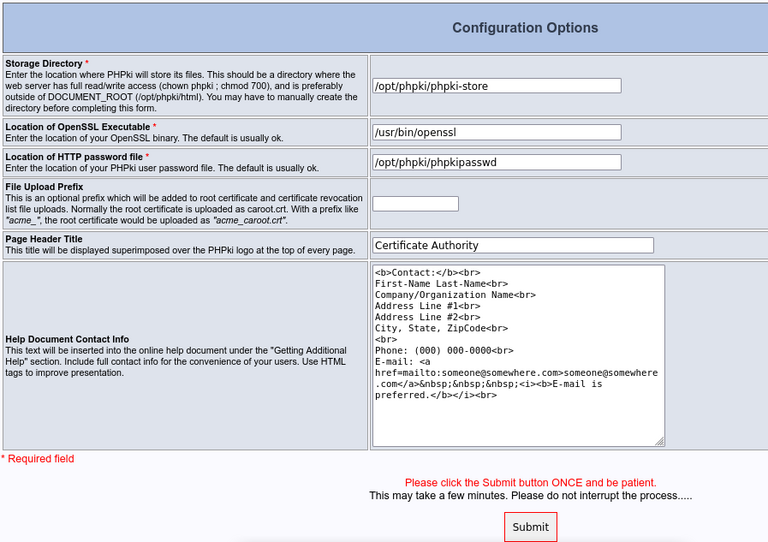
The second part is like this:
The default settings should be OK for most installations. You may just want to change the "Help Document Contact Info" part.
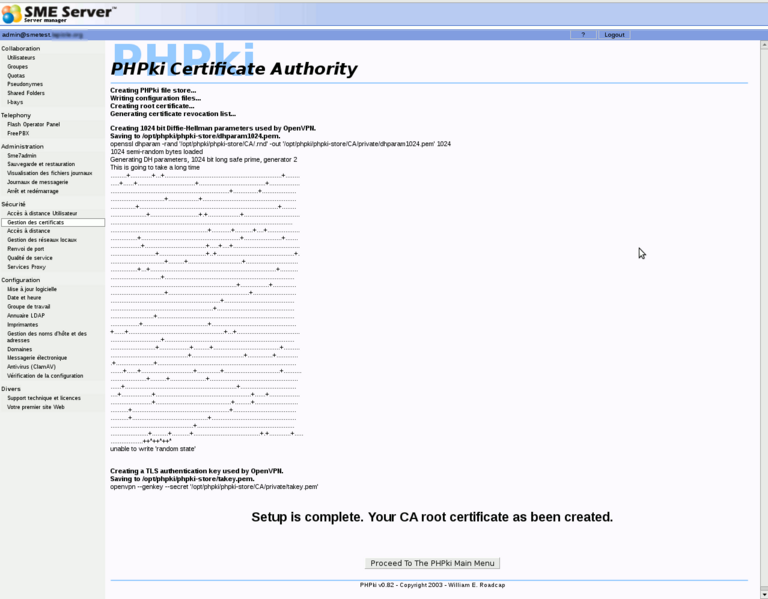
Once you have submitted this form (which can take several minutes, be patient, as generating dh parameters can take a long time), you should have something like this:
Now you'll be able to start using PHPki. It's quite easy to use.
The administrative interface is available on the server-manager or directly https://my.domain.tld/phpki/ca
There's also a public interface, available only from the local networks, but without password at https://my.domain.tld/phpki. Here, users can download the Master CA certificate, the CRL, or search for certificates of other users (public part only of course).
Add another admin
if you happen to need to delegate certificate generation, you can use user-panel to add access to the panel, but you will also need to add the user manually to phpki config
edit /opt/phpki/phpki-store/config/config.php
#$PHPki_admins = Array(md5('admin'));
$PHPki_admins = Array(md5('admin'),md5('user2'));
Uninstall
To uninstall the contrib from your server, just run the following commands:
yum remove smeserver-phpki-ng phpki-ng expand-template /etc/httpd/conf/httpd.conf systemctl restart /service/httpd-e-smith
Certificates and PKI configuration are stored in /opt/phpki/phpki-store, php files are in /opt/phpki/html
Re-install
before phpki-ng 0.84-14
If you have removed the contrib, and want to re-install it keeping your previous CA (assuming you restored /opt/phpki), you'll need to follow these steps after you have installed the rpms:
cd /opt/phpki/html/ rm -f index.php rm -f setup.php ln -s main.php index.php cat config.php.rpmsave > config.php cd ca rm -f index.php ln -s main.php index.php cd /opt/phpki/ chown phpki:phpki -R phpki-store chown root:phpki -R html/config.php
Bugs
Please raise bugs under the SME-Contribs section in bugzilla.
smeserver-phpki-ng
For the new smeserver-phpki-ng, select the smeserver-phpki-ng component or use this link
| ID | Product | Version | Status | Summary (4 tasks) ⇒ |
|---|---|---|---|---|
| 12436 | SME Contribs | 10.0 | CONFIRMED | failure to download crl |
| 12426 | SME Contribs | 10.0 | CONFIRMED | smeserver-phpki-ng Setting httpd-pki PHPVersion does not alter template |
| 12228 | SME Contribs | 10.0 | RESOLVED | wrong uid and gid |
| 10903 | SME Contribs | Futur | CONFIRMED | NFR: Save certificate bundle for ovpn configs |
phpki-ng
For the new phpki-ng itself select the phpki-ng component or use this link
| ID | Product | Version | Status | Summary (2 tasks) ⇒ |
|---|---|---|---|---|
| 12420 | SME Contribs | 10.0 | CONFIRMED | phpki-ng Create and download file has no name |
| 12275 | SME Contribs | 10.0 | CONFIRMED | PHP Warning: Use of undefined constant |
Changelog
Only released version in smecontrib are listed here.
- fix httpd needs QSD in place of ? [SME: 12354]
2022/12/28 Jean-Philippe Pialasse 0.3-21.sme
- fix chop isntead of chomp for config.php [SME: 12293]
- small fixes for config.php and httpd
2022/12/14 Jean-Philippe Pialasse 0.3-18.sme
- revert log/phpki [SME: 12266]
- phpki-ng autopopulate base info from ldap [SME: 11440]
- ensure user are seen by php-pool [SME: 12268]
- safe remote access for crl [SME: 11439]
- fix typo preventing httpd-pki to start 2
- add dl_crl_pem.php [SME: 12272]
- fix regex and potential code injection [SME: 12274]
2022/12/14 Jean-Philippe Pialasse 0.84-14.sme
- add easy and safe access to crl download [SME: 12272]
- fix revoke certificate failing on whitespace pass [SME: 12273]
- fix missing default_md in config.php from previous versions [SME: 12267]
- remove extra space in URL in search.php [SME: 12232]
- Attempt to fix the final reload after CA creation [SME: 11192]