Difference between revisions of "Email Whitelist-Blacklist Control"
m (→Installation) |
m (→Known Issues) |
||
| (24 intermediate revisions by 6 users not shown) | |||
| Line 1: | Line 1: | ||
| + | {{Languages}} | ||
| + | |||
===Maintainer=== | ===Maintainer=== | ||
| − | Originally developed by Darrell May. | + | Originally developed by Darrell May.<br /> |
| + | |||
| + | [mailto:stephdl@de-labrusse.fr stephdl] Stéphane de Labrusse AKA [[User:stephdl|Stephdl]]<br /> | ||
| − | + | === Version === | |
| + | {{ #smeversion: smeserver-wbl }} | ||
===Description=== | ===Description=== | ||
| Line 17: | Line 22: | ||
Install of the lastest Email Whitelist-Blacklist package is from the smecontribs repo: | Install of the lastest Email Whitelist-Blacklist package is from the smecontribs repo: | ||
| − | + | =====Install package:===== | |
| − | + | <tabs container><tab name="For SME 10"> | |
| + | yum install --enablerepo=smecontribs smeserver-wbl | ||
| + | |||
| + | </tab> | ||
| + | <tab name="For SME 9"> | ||
| + | yum install --enablerepo=smecontribs smeserver-wbl | ||
| + | Reconfigure machine: | ||
| + | signal-event console-save | ||
| + | or if you prefer to reboot your server | ||
| + | signal-event post-upgrade; signal-event reboot | ||
| + | |||
| + | </tab> | ||
| + | <tab name="For SME 8"> | ||
yum --enablerepo smecontribs install smeserver-wbl | yum --enablerepo smecontribs install smeserver-wbl | ||
| − | + | Reconfigure machine: | |
| − | |||
| − | |||
| − | |||
| − | |||
signal-event console-save | signal-event console-save | ||
or if you prefer to reboot your server | or if you prefer to reboot your server | ||
signal-event post-upgrade; signal-event reboot | signal-event post-upgrade; signal-event reboot | ||
| + | </tab> | ||
| + | </tabs> | ||
| + | |||
| + | =====Configure:===== | ||
| + | |||
| + | Once you do this a new menu item will be visable in the Server-Manager on the left hand side, called '''E-mail WBL'''. Traffic is scanned and may be blocked due to the various screening methods enabled. Clicking on this will present you with 3 buttons. | ||
| + | |||
| + | You may use this panel to define e-mail white/black lists and RBLs. | ||
| + | |||
| + | RBL's List is used to adjust DNSBL and RHSBL. | ||
| + | '''[RBLs List]''' | ||
| − | |||
| − | |||
| − | |||
| − | |||
Black lists are used for rejecting e-mail traffic. | Black lists are used for rejecting e-mail traffic. | ||
| − | '''[ | + | '''[Black List]''' |
| + | |||
White lists are used for accepting e-mail traffic. | White lists are used for accepting e-mail traffic. | ||
| − | '''[ | + | '''[White List]''' |
| − | + | ||
| − | + | If you press the Black List button you will see the following window. | |
| − | |||
| − | |||
[[File:email-Reject.jpg]] | [[File:email-Reject.jpg]] | ||
| − | If you press the | + | If you press the White List button you will see the following window. |
| − | [[File:Email-accept.jpg]] | + | |
| + | [[File:Email-accept.jpg|842px]] | ||
| + | |||
| + | If you press the RBLs List button you will see the following window. | ||
| + | |||
| + | [[File:Wbl rbl.jpg|842px]] | ||
| − | And finally If you press the | + | And finally If you press the SAVE button this will apply any of the changes you made, wait for confirmation message. |
| − | |||
| − | |||
| − | |||
===Usage Examples=== | ===Usage Examples=== | ||
| − | Black Lists: REJECT | + | ====Black Lists: REJECT==== |
| + | |||
| + | =====Plugin: Helo===== | ||
| + | |||
| + | Format: | ||
| + | some.host.domain | ||
| + | |||
| + | Add domains, hostnames, or perl regexp patterns to the <badhelo> config file; one per line. | ||
| + | |||
| + | {{Note box|You cannot block HELO IP addresses with this plugin. It is not designed to do that. Please look at other methods such as direct IP blocking via the firewall, or contribs like Fail2ban, GeoIP, xt_tables}} | ||
| + | |||
| + | https://github.com/smtpd/qpsmtpd/blob/master/plugins/helo | ||
| + | |||
| + | Matches in the <badhelo> config file, including yahoo.com and aol.com, which neither the real Yahoo or the real AOL use, but which spammers use a lot. | ||
| + | Like qmail with the qregex patch, the <badhelo> file can also contain perl regular expressions. In addition to normal regexp processing, a pattern can start with a ! character, and get a negated (!~) match. | ||
| + | |||
| + | =====Plugin: Badmailfrom===== | ||
| + | |||
| + | Format: | ||
| + | @host or user@host | ||
| + | |||
| + | This plugin also supports regular expression matches. This allows special patterns to be denied (e.g. FQDN-VERP, percent hack, bangs, double ats). | ||
| + | Patterns are stored in the format pattern'''(\s+)'''response, where pattern is a Perl pattern expression. Don't forget to anchor the pattern (front ^ and back $) if you want to restrict it from matching anywhere in the string. | ||
| + | |||
| + | https://github.com/smtpd/qpsmtpd/blob/master/plugins/badmailfrom | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | White Lists: ACCEPT | + | ====White Lists: ACCEPT==== |
| − | Whitelisthosts | + | =====Whitelisthosts===== |
| + | |||
| + | see this post http://forums.contribs.org/index.php/topic,51429.0.html | ||
Single IP | Single IP | ||
| Line 77: | Line 115: | ||
192.168 | 192.168 | ||
| − | WhitelistHELO | + | =====WhitelistHELO===== |
host.domain.com | host.domain.com | ||
| − | Whitelistsenders | + | =====Whitelistsenders===== |
joe@foo.com | joe@foo.com | ||
| − | + | foo.com | |
| + | === Known Issues === | ||
| − | + | See bugs below. | |
| − | |||
| − | |||
| − | |||
=== Bugs === | === Bugs === | ||
Please raise bugs under the SME Contribs section in {{BugzillaFileBug|product=SME%20Contribs|component=smeserver-wbl|title=bugzilla}}. | Please raise bugs under the SME Contribs section in {{BugzillaFileBug|product=SME%20Contribs|component=smeserver-wbl|title=bugzilla}}. | ||
| + | {{#bugzilla:columns=id,product,version,status,summary |sort=id |order=desc |component=smeserver-wbl |noresultsmessage="No open bugs found."}} | ||
| + | |||
| + | ===Changelog=== | ||
| + | Only released version in smecontrib are listed here. | ||
| + | {{#smechangelog: smeserver-wbl}} | ||
---- | ---- | ||
[[Category: Contrib]] | [[Category: Contrib]] | ||
[[Category: Mail]] | [[Category: Mail]] | ||
[[Category: Administration:Content Spam Virus Blocking]] | [[Category: Administration:Content Spam Virus Blocking]] | ||
Latest revision as of 16:15, 27 August 2023
Maintainer
Originally developed by Darrell May.
stephdl Stéphane de Labrusse AKA Stephdl
Version
Description
This contrib provides a server-manager panel to designate user defined email whitelists and blacklists.
An email whitelist is a list of hosts, domains, or email addresses which will be accepted by SME Server regardless of possible spam content or origin. Administrators should use caution when using whitelists as email coming from whitelisted addresses will bypass many of the mechanisms that SME provides for identifying unsafe email messages.
An email blacklist is a list of hosts, domains, or email addresses that will be blocked all of the time.
Installation
Install of the lastest Email Whitelist-Blacklist package is from the smecontribs repo:
Install package:
yum install --enablerepo=smecontribs smeserver-wbl
yum install --enablerepo=smecontribs smeserver-wbl
Reconfigure machine:
signal-event console-save
or if you prefer to reboot your server
signal-event post-upgrade; signal-event reboot
yum --enablerepo smecontribs install smeserver-wbl
Reconfigure machine:
signal-event console-save
or if you prefer to reboot your server
signal-event post-upgrade; signal-event reboot
Configure:
Once you do this a new menu item will be visable in the Server-Manager on the left hand side, called E-mail WBL. Traffic is scanned and may be blocked due to the various screening methods enabled. Clicking on this will present you with 3 buttons.
You may use this panel to define e-mail white/black lists and RBLs.
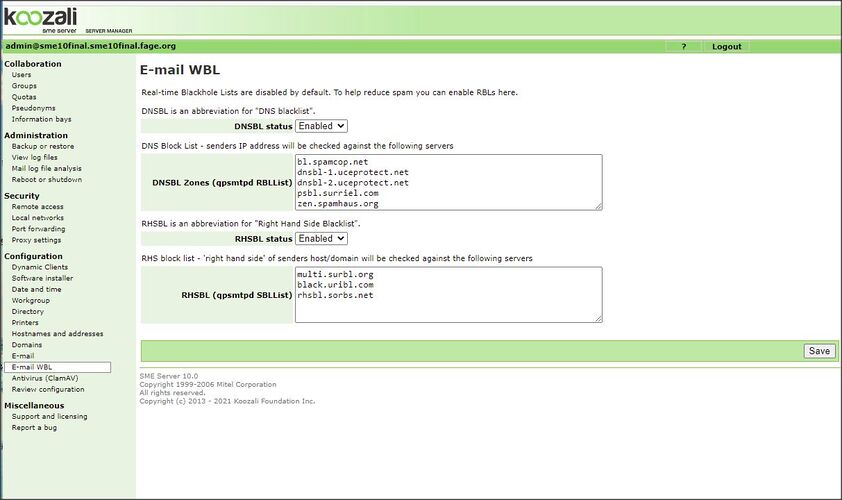
RBL's List is used to adjust DNSBL and RHSBL. [RBLs List]
Black lists are used for rejecting e-mail traffic. [Black List]
White lists are used for accepting e-mail traffic. [White List]
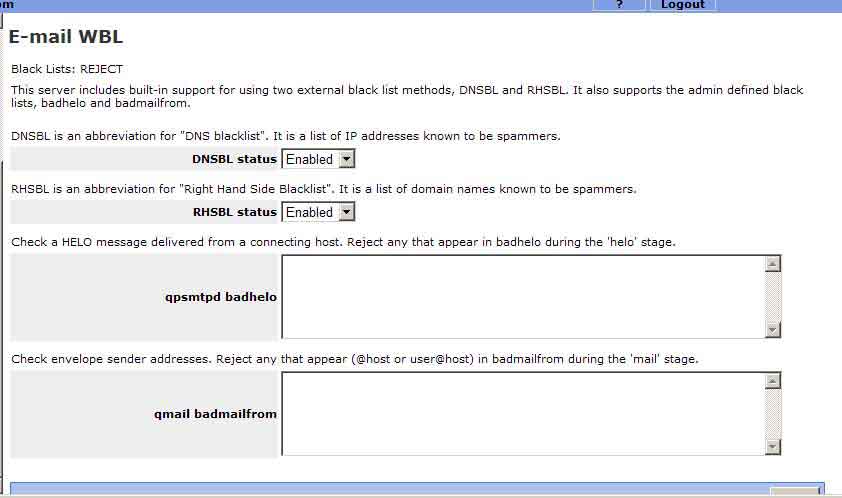
If you press the Black List button you will see the following window.
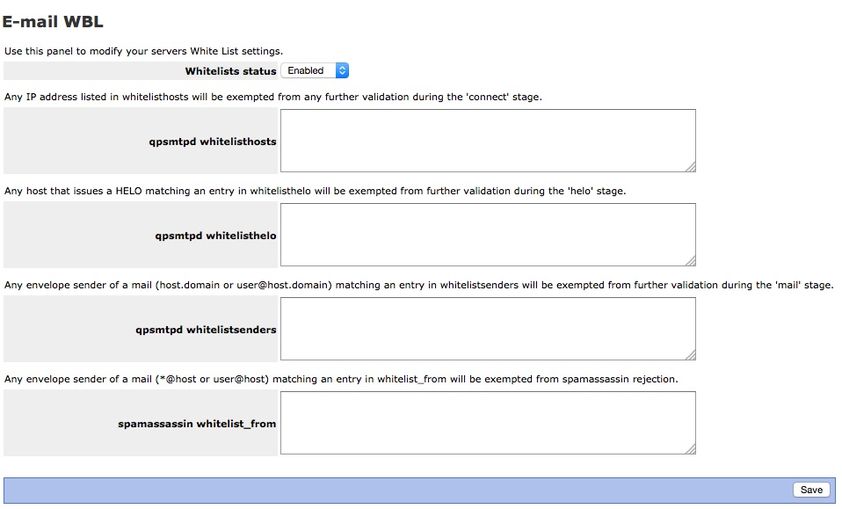
If you press the White List button you will see the following window.
If you press the RBLs List button you will see the following window.
And finally If you press the SAVE button this will apply any of the changes you made, wait for confirmation message.
Usage Examples
Black Lists: REJECT
Plugin: Helo
Format: some.host.domain
Add domains, hostnames, or perl regexp patterns to the <badhelo> config file; one per line.
https://github.com/smtpd/qpsmtpd/blob/master/plugins/helo
Matches in the <badhelo> config file, including yahoo.com and aol.com, which neither the real Yahoo or the real AOL use, but which spammers use a lot. Like qmail with the qregex patch, the <badhelo> file can also contain perl regular expressions. In addition to normal regexp processing, a pattern can start with a ! character, and get a negated (!~) match.
Plugin: Badmailfrom
Format: @host or user@host
This plugin also supports regular expression matches. This allows special patterns to be denied (e.g. FQDN-VERP, percent hack, bangs, double ats). Patterns are stored in the format pattern(\s+)response, where pattern is a Perl pattern expression. Don't forget to anchor the pattern (front ^ and back $) if you want to restrict it from matching anywhere in the string.
https://github.com/smtpd/qpsmtpd/blob/master/plugins/badmailfrom
White Lists: ACCEPT
Whitelisthosts
see this post http://forums.contribs.org/index.php/topic,51429.0.html
Single IP
192.168.10.1
Subnets
192.168.10. (be careful - with no trailing . you match 192.168.100 - 192.168.109. ) 192.168
WhitelistHELO
host.domain.com
Whitelistsenders
joe@foo.com foo.com
Known Issues
See bugs below.
Bugs
Please raise bugs under the SME Contribs section in bugzilla .
| ID | Product | Version | Status | Summary (6 tasks) ⇒ |
|---|---|---|---|---|
| 12649 | SME Contribs | 11.0 | CONFIRMED | SME11 remove /etc/e-smith/templates/var/service/qpsmtpd/config/badmailfrom |
| 10472 | SME Contribs | Futur | CONFIRMED | NFR Add subnet checking to whitelist hosts |
| 10117 | SME Contribs | Futur | CONFIRMED | add support for URIBL |
| 9276 | SME Contribs | 8.2 | CONFIRMED | design and documentation of qpsmtpd wbl vs spamassassin white or black lists |
| 9275 | SME Contribs | 8.2 | CONFIRMED | wbl whitelist status switch does nothing in server manager |
| 4664 | SME Contribs | 7.3 | CONFIRMED | Redesign wbl dbase to improve efficiency |
Changelog
Only released version in smecontrib are listed here.
- Edit Menu entry to conform to new arrangements [SME: 12493]
2024/02/25 Jean-Philippe Pialasse 0.5.0-8.sme
- reload qpsmtpd config on panel update [SME: 12490]
2022/04/17 Jean-Philippe Pialasse 0.5.0-7.sme
- fix multiple rpm owned files [SME: 11678]
- Add in class def in overall div in ep file [SME: 11828]
- fix reference update in server manager [SME: 11687]