Difference between revisions of "SME Server:Documentation:Administration Manual:Chapter11"
(→Telnet) |
(→SSH) |
||
| (20 intermediate revisions by 5 users not shown) | |||
| Line 1: | Line 1: | ||
| − | {{Languages}} | + | <noinclude>{{Languages}}</noinclude> |
| − | === | + | ===Security=== |
====Remote Access==== | ====Remote Access==== | ||
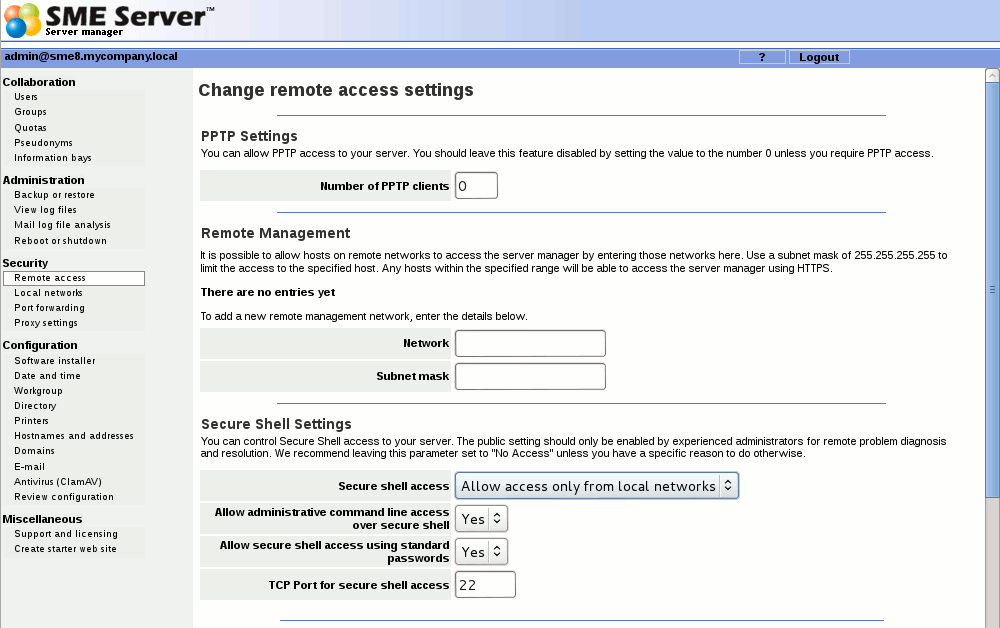
If you're an advanced user, the SME Server provides several different ways to access the underlying operating system, either from a computer on your internal network or from a computer outside your site on the Internet. Additionally, you have the ability to access your computer network securely from a remote computer. All of these operations are configured from the screen shown below in the server manager. | If you're an advanced user, the SME Server provides several different ways to access the underlying operating system, either from a computer on your internal network or from a computer outside your site on the Internet. Additionally, you have the ability to access your computer network securely from a remote computer. All of these operations are configured from the screen shown below in the server manager. | ||
| + | |||
| + | Each of these remote access methods is described below. | ||
[[Image:Remote-access-1.png]] | [[Image:Remote-access-1.png]] | ||
[[Image:Remote-access-2.png]] | [[Image:Remote-access-2.png]] | ||
| − | |||
| − | ===== | + | ===== VPN ===== |
| − | If you | + | |
| + | (awaiting full integration) | ||
| + | |||
| + | <!--The Point-to-Point Tunnelling Protocol (PPTP) is used to create client-to-server Virtual Private Networks (VPNs) and was developed by the PPTP Forum, an industry group which included Microsoft and several other companies. A VPN is a private network of computers that uses the public Internet to connect some nodes. PPTP allows users to connect to their corporate networks across the Internet. | ||
| + | |||
| + | Microsoft's PPTP implementation is widely used in the Windows world to provide remote access across the Internet. If you have a remote Windows system (for instance, a laptop or a home computer) that has access to the Internet, you can also access the information stored on your server. | ||
| + | |||
| + | If you wish to enable VPN access, you must decide how many individual PPTP clients you will allow to connect to your server simultaneously, and enter that number here. The simplest method is to enter the total number of remote PPTP clients in your organization. Alternatively, if you have a slow connection to the Internet and do not want all of those PPTP clients to connect at the same time, you can enter a lower number here. For instance, if you have five users who from time to time use PPTP to connect remotely, entering 5 here would allow all of them to connect at any time. Entering 2 would only allow two users to connect at any given time. If a third user tried to connect, he or she would receive an error message and would not be able to connect until one of the other users disconnected. If, on the other hand, you entered 0, no PPTP connections would be allowed. | ||
| + | |||
| + | Before the server is ready to accept PPTP connections each user that is to be allowed access is to be granted 'VPN Client Access' in the | ||
| + | [[:SME_Server:Documentation:Administration_Manual:Chapter9#Users |Users]] panel of the /server-manager. | ||
| − | + | To connect using PPTP, the protocol must be installed on each remote Windows client. Typically, this is done through the Network Control Panel (you may need to have your original Windows installation CD available). After it is installed (a reboot of your Windows system may be needed), you can create new connections through the Dial-Up Networking panel by entering the external IP address of the server you wish to connect to. Once you're finished, you should be able to initiate a PPTP connection by double-clicking the appropriate icon in the Dial-Up Networking window. When you then open up your Network Neighborhood window, you should see your server workgroup listed there. | |
| − | + | {{Note box|After changing the number of pptp clients allowed, the increased number of users is not updated until existing users have logged off.}} | |
| − | + | {{Note box|PPTP uses TCP port 1723 and the Generic Routing Encapsulation (GRE) protocol. If you are using an external router or gateway to your server, and require an inbound VPN connection to support external users, you will need both TCP port 1723 and the GRE protocol to be forwarded. | |
| − | + | However most PPTP passthrough routers only allow outbound connections. Not all allow inbound connections. Forwarding PPTP inbound is frequently unreliable due to the way PPTP works. | |
| − | + | The simple, reliable solution is to remove the router and let the SME Server handle the link directly. | |
| − | |||
| − | |||
| − | + | For a more detailed description of the PPTP protcol see http://en.wikipedia.org/wiki/Point-to-point_tunneling_protocol}} | |
| − | |||
| − | |||
| − | + | {{Warning box|To protect your network, the SME Server enforces the use of 128-bit encryption for PPTP connections, rather than the 40-bit encryption provided in earlier versions of Microsoft's PPTP software. If you are unable to establish a PPTP connection to your server, you should visit http://windowsupdate.microsoft.com/ and download the appropriate update. Due to the dynamic nature of Microsoft's web site, the page may appear differently depending upon the version of Windows you are using. In most cases, you will want to look or search for Virtual Private Networking or a Dial Up Networking 128-bit encryption update . You may need to install the 40-bit encryption update first, and then install the 128-bit encryption update. Note that with Microsoft's ActiveUpdate process, if you are not presented with the choice for this update, it is most likely already installed in your system.}}--> | |
| − | ===== | + | ===== Remote Management ===== |
| − | + | To allow access to the /server-manager from remote networks add allowed IP addresses to the Remote Management section. | |
| − | + | To allow a single computer (or network of computers behind a firewall) add its IP and the netmask. | |
| + | 223.102.19.24 255.255.255.255 | ||
| − | If you | + | ===== SSH ===== |
| + | If you need to connect directly to your server and login from a remote system belonging to you, we strongly encourage you to use ssh. In addition to UNIX and Linux systems, ssh client software is now also available for Windows and Macintosh systems. (See the section below.) | ||
| − | + | {{Tip box|msg=Configuring SSH access as public will result in lots of script based login attempts which consume bandwidth, CPU and generate log noise. A new iptables rule which blocks repeated connection attempts to the configured sshd port. | |
| + | It is set to reject connections when there have been 3 or more requests in the previous 15 minutes. By design only IP outside your local network will blocked if too many attempts are done. See [[AutoBlock#Public_SSH_Acess|AutoBlock_SSH]]}} | ||
| − | + | If you do not have any reason to allow remote access, we suggest you set this to No access. | |
| − | + | SSH (secure shell) provides a secure, encrypted way to login to a remote machine across a network or to copy files from a local machine to a server. Many people do not realize that many programs such as telnet and ftp transmit your password in plain, unencrypted text across your network or the Internet. ssh and its companion program scp provide a secure way to login or copy files. The ssh protocol was originally invented by SSH Communications Security which sells commercial ssh servers, clients, and other related products. The protocol itself has two versions - SSH1 and SSH2 - both of which are supported by most clients and servers today. For more information about SSH Communications Security and its commercial products, visit http://www.ssh.com/. | |
| − | + | OpenSSH, included with the SME Server, is a free version of the ssh tools and protocol. The server provides the ssh client programs as well as an ssh server daemon and supports both the SSH1 and SSH2 protocols. For more information about OpenSSH, visit http://www.openssh.com/. | |
| − | + | Once ssh is enabled, you should be able to connect to your server simply by launching the ssh client on your remote system and ensuring that it is pointed to the external domain name or IP address for your server. In the default configuration, you should next be prompted for your user name. After you enter admin and your administrative password, you will be in the server console. From here you can change the server configuration, access the server manager through a text browser or perform other server console tasks. | |
| − | + | If you do enable ssh access, you have additional configuration options: | |
| + | * Allow administrative command line access over ssh - This allows someone to connect to your server and login as "root" with the administrative password. The user would then have full access to the underlying operating system. This can be useful if someone is providing remote support for your system. In most cases we recommend setting this to No. | ||
| + | * Allow ssh using standard passwords - If you choose Yes (the default), users will be able to connect to the server using a standard user name and password. This may be a concern from a security point of view, in that someone wishing to break into your system could connect to your ssh server and repeatedly enter user names and passwords in an attempt to find a valid combination. A more secure way to allow ssh access is called RSA Authentication and involves the copying of an ssh key from the client to the server. See the [[SME_Server:Documentation:User_Manual:Chapter1#Securing_SSH_With_Public_.2F_Private_Keys| User Manual ]] for details | ||
| + | * TCP Port for secure shell access - Change the port the ssh client connects to the server, choose a random free port eg. 822. This provides some protection from casual attacks on the usual port of 22 and reduce log noise, but will not deter a serious attacker. | ||
| − | + | {{Note box|By default, only two user names can be used to login remotely to the server: admin (to access the server console) and root (to use the Linux shell). Regular users are not permitted to login to the server itself. If you give another user the ability to login remotely to the server, you will need to access the underlying Linux operating system and manually change the user's shell.}} | |
| − | + | * SSH clients | |
| + | A number of different free software programs provide ssh clients for use in a Windows, Macintosh or Linux environment. Several are extensions of existing telnet programs that include ssh functionality. A list of known clients can be found online at https://www.ssh.com/ssh/client, [https://www.ssh.com/ssh/putty/download PuTTY] being the most popular for Windows as it meets most requirements and is regularly updated. Linux workstations normally have direct ssh capability. | ||
| + | A commercial ssh client is available from SSH Communications Security at: http://www.ssh.com/products/ssh/download.html. Note that the client is free for evaluation, academic and certain non-commercial uses. | ||
| − | + | Do note that the SSH protocol also supports SFTP (an alternate secure FTP) and SCP (secure copy). [https://winscp.net/eng/index.php WinSCP] is one example of a Windows client that supports both for GUI Files transfer via the shell. | |
| − | ===== | + | =====FTPs===== |
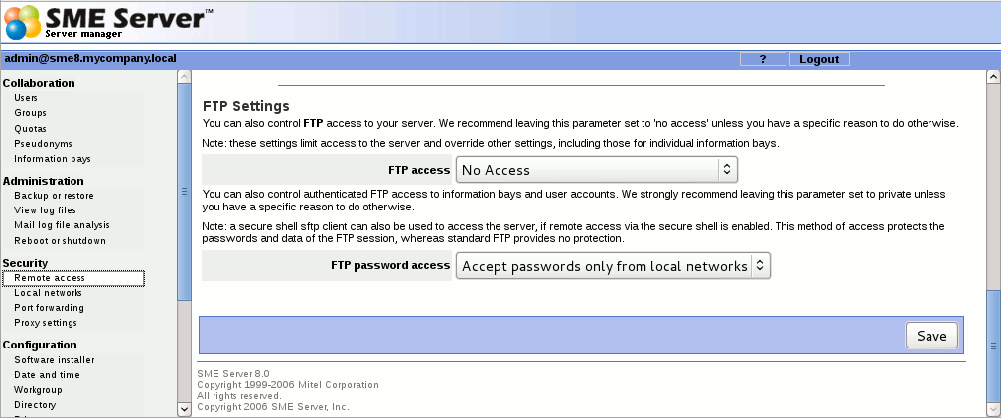
Another way to upload or download files to and from your server is to enable a protocol called FTP, or "file transfer protocol". This screen enables you to set your policy for FTP. Note that allowing liberal FTP access to your server does reduce your security. You have two options that you can set here. | Another way to upload or download files to and from your server is to enable a protocol called FTP, or "file transfer protocol". This screen enables you to set your policy for FTP. Note that allowing liberal FTP access to your server does reduce your security. You have two options that you can set here. | ||
| + | |||
| + | '''FTP is now FTPs by default''', or FTP over TLS, and this setting is forced. If for any reason you want or need to be less secure than that, then please check the wiki on how to do so. Plain FTP does not use encryption and so is trivially cracked, we strongly recommend you use the default FTPs. | ||
FTP user account access: Private FTP access allows only people on your internal network to write files to your server. Public FTP access allows users both inside and outside your local network to read or write files on your server, provided they have an account and password. If, for example, you want to be able to update your web site from home using FTP, you would choose the "Public" setting. We strongly recommend you leave this as Private unless you have a specific reason to do so. | FTP user account access: Private FTP access allows only people on your internal network to write files to your server. Public FTP access allows users both inside and outside your local network to read or write files on your server, provided they have an account and password. If, for example, you want to be able to update your web site from home using FTP, you would choose the "Public" setting. We strongly recommend you leave this as Private unless you have a specific reason to do so. | ||
| Line 65: | Line 82: | ||
FTP access limits: This allows you to set an overall site-wide policy for FTP access. The setting you choose here will override all other FTP settings on your server . For example, if you choose "Disable public FTP access" here and then later configure an i-bay to allow public FTP access from the Internet, such access will be forbidden. Note that one of the choices here allows you to completely disable any use of FTP. | FTP access limits: This allows you to set an overall site-wide policy for FTP access. The setting you choose here will override all other FTP settings on your server . For example, if you choose "Disable public FTP access" here and then later configure an i-bay to allow public FTP access from the Internet, such access will be forbidden. Note that one of the choices here allows you to completely disable any use of FTP. | ||
| − | =====Telnet===== | + | <!--=====Telnet===== |
| − | Telnet has traditionally been one of the tools used to login remotely to other systems across a network or the Internet. However, when you use telnet, all user names and passwords are transmitted without any kind of encryption, dramatically reducing the security of your server. Because ssh usage has increased to an acceptable level, telnet access has been removed from the SME Server | + | Telnet has traditionally been one of the tools used to login remotely to other systems across a network or the Internet. However, when you use telnet, all user names and passwords are transmitted without any kind of encryption, dramatically reducing the security of your server. Because ssh usage has increased to an acceptable level, telnet access has been removed from the SME Server--> |
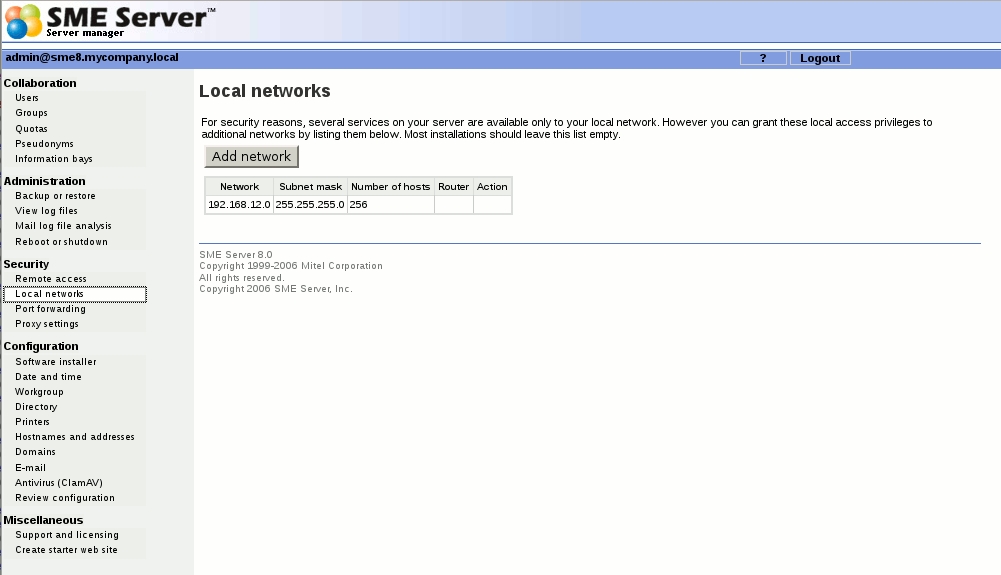
====Local networks==== | ====Local networks==== | ||
| Line 77: | Line 94: | ||
[[Image:Local-networks.png]] | [[Image:Local-networks.png]] | ||
| − | {{ | + | {{Note box|Depending on the architecture of your network infrastructure, the instructions for configuring the client machines on that additional network may be different than the instructions outlined in the chapter in this user guide. If you have questions regarding adding another network, you may wish to contact Contribs.org and visit the forums.}} |
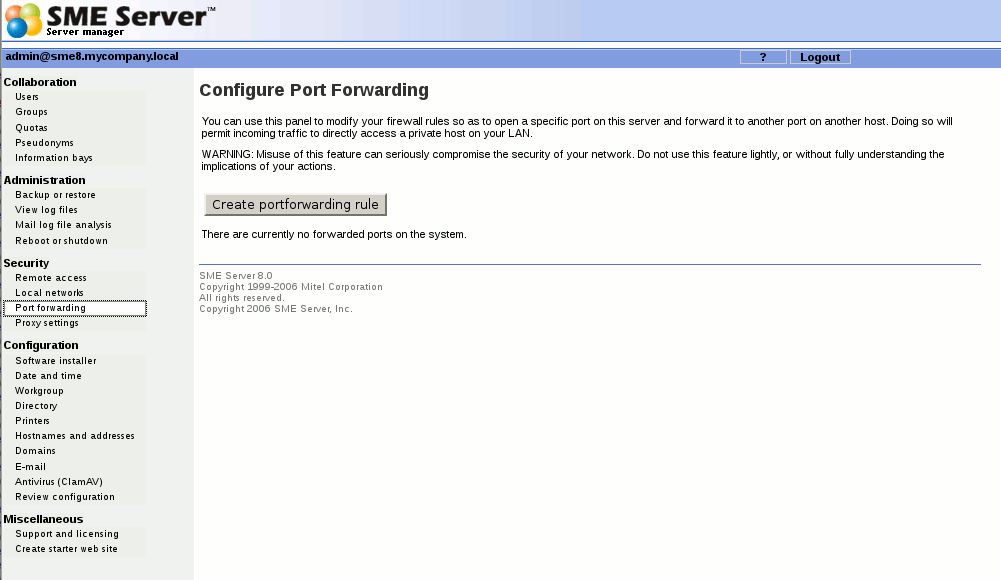
====Port forwarding==== | ====Port forwarding==== | ||
| Line 86: | Line 103: | ||
You can use the panel shown above to modify your firewall rules so as to open a specific port (or range of ports) on this server and forward it to another port on another host. Doing so will permit incoming traffic to directly access a private host on your LAN. | You can use the panel shown above to modify your firewall rules so as to open a specific port (or range of ports) on this server and forward it to another port on another host. Doing so will permit incoming traffic to directly access a private host on your LAN. | ||
| − | {{ | + | {{Warning box|Misuse of this feature can seriously compromise the security of your network. Do not use this feature lightly, or without fully understanding the implications of your actions.}} |
====Proxy settings==== | ====Proxy settings==== | ||
Your SME Server has a transparent HTTP and SMTP proxy. | Your SME Server has a transparent HTTP and SMTP proxy. | ||
| + | =====HTTP Proxy===== | ||
The server's HTTP proxy works to reduce overall uplink usage by caching recently-visited pages. It is transparent to web browsers using this server as their gateway. | The server's HTTP proxy works to reduce overall uplink usage by caching recently-visited pages. It is transparent to web browsers using this server as their gateway. | ||
| + | =====SMTP Proxy===== | ||
The server's transparent SMTP proxy works to reduce virus traffic from infected client hosts by forcing all outgoing SMTP traffic through this server. If you wish to use an alternate SMTP server, and this server is your gateway to it, disable this proxy. | The server's transparent SMTP proxy works to reduce virus traffic from infected client hosts by forcing all outgoing SMTP traffic through this server. If you wish to use an alternate SMTP server, and this server is your gateway to it, disable this proxy. | ||
| + | |||
| + | - Disabled. Clients behind SME Server are allowed to connect to any SMTP | ||
| + | server anywhere in the world (that allow them to). | ||
| + | |||
| + | - Blocked. This forces all SMTP traffic to go through the server and be authenticated. | ||
| + | All attempts to connect to any SMTP Server other than the SME Server will be blocked | ||
| + | and treated as if there is no SMTP server on the other end. (This is the new default) | ||
| + | |||
| + | - Enabled. Any attempt to connect to an SMTP Server other than the | ||
| + | SME Server will be redirected to the SME Server. If someone attempts to connect to an | ||
| + | external smtp server (gmail for example) it will be redirected to the sme | ||
| + | server. If they then have it set to authenticate to that external server | ||
| + | instead of passing the user/pass to the external server it will pass it to the | ||
| + | sme server and fail. (This is the old default) | ||
| + | |||
| + | Note: The server (by default) now requires email clients (other than webmail) to authenticate and will not allow auth to occur over an unsecure link. If for example you are using thunderbird then you must set the authentication method to normal password. Leave the connection security at starttls or ssl/tls. | ||
[[Image:Proxy-settings.png]] | [[Image:Proxy-settings.png]] | ||
Latest revision as of 01:16, 24 April 2021
Security
Remote Access
If you're an advanced user, the SME Server provides several different ways to access the underlying operating system, either from a computer on your internal network or from a computer outside your site on the Internet. Additionally, you have the ability to access your computer network securely from a remote computer. All of these operations are configured from the screen shown below in the server manager.
Each of these remote access methods is described below.
VPN
(awaiting full integration)
Remote Management
To allow access to the /server-manager from remote networks add allowed IP addresses to the Remote Management section.
To allow a single computer (or network of computers behind a firewall) add its IP and the netmask.
223.102.19.24 255.255.255.255
SSH
If you need to connect directly to your server and login from a remote system belonging to you, we strongly encourage you to use ssh. In addition to UNIX and Linux systems, ssh client software is now also available for Windows and Macintosh systems. (See the section below.)
If you do not have any reason to allow remote access, we suggest you set this to No access.
SSH (secure shell) provides a secure, encrypted way to login to a remote machine across a network or to copy files from a local machine to a server. Many people do not realize that many programs such as telnet and ftp transmit your password in plain, unencrypted text across your network or the Internet. ssh and its companion program scp provide a secure way to login or copy files. The ssh protocol was originally invented by SSH Communications Security which sells commercial ssh servers, clients, and other related products. The protocol itself has two versions - SSH1 and SSH2 - both of which are supported by most clients and servers today. For more information about SSH Communications Security and its commercial products, visit http://www.ssh.com/.
OpenSSH, included with the SME Server, is a free version of the ssh tools and protocol. The server provides the ssh client programs as well as an ssh server daemon and supports both the SSH1 and SSH2 protocols. For more information about OpenSSH, visit http://www.openssh.com/.
Once ssh is enabled, you should be able to connect to your server simply by launching the ssh client on your remote system and ensuring that it is pointed to the external domain name or IP address for your server. In the default configuration, you should next be prompted for your user name. After you enter admin and your administrative password, you will be in the server console. From here you can change the server configuration, access the server manager through a text browser or perform other server console tasks.
If you do enable ssh access, you have additional configuration options:
- Allow administrative command line access over ssh - This allows someone to connect to your server and login as "root" with the administrative password. The user would then have full access to the underlying operating system. This can be useful if someone is providing remote support for your system. In most cases we recommend setting this to No.
- Allow ssh using standard passwords - If you choose Yes (the default), users will be able to connect to the server using a standard user name and password. This may be a concern from a security point of view, in that someone wishing to break into your system could connect to your ssh server and repeatedly enter user names and passwords in an attempt to find a valid combination. A more secure way to allow ssh access is called RSA Authentication and involves the copying of an ssh key from the client to the server. See the User Manual for details
- TCP Port for secure shell access - Change the port the ssh client connects to the server, choose a random free port eg. 822. This provides some protection from casual attacks on the usual port of 22 and reduce log noise, but will not deter a serious attacker.
- SSH clients
A number of different free software programs provide ssh clients for use in a Windows, Macintosh or Linux environment. Several are extensions of existing telnet programs that include ssh functionality. A list of known clients can be found online at https://www.ssh.com/ssh/client, PuTTY being the most popular for Windows as it meets most requirements and is regularly updated. Linux workstations normally have direct ssh capability.
A commercial ssh client is available from SSH Communications Security at: http://www.ssh.com/products/ssh/download.html. Note that the client is free for evaluation, academic and certain non-commercial uses.
Do note that the SSH protocol also supports SFTP (an alternate secure FTP) and SCP (secure copy). WinSCP is one example of a Windows client that supports both for GUI Files transfer via the shell.
FTPs
Another way to upload or download files to and from your server is to enable a protocol called FTP, or "file transfer protocol". This screen enables you to set your policy for FTP. Note that allowing liberal FTP access to your server does reduce your security. You have two options that you can set here.
FTP is now FTPs by default, or FTP over TLS, and this setting is forced. If for any reason you want or need to be less secure than that, then please check the wiki on how to do so. Plain FTP does not use encryption and so is trivially cracked, we strongly recommend you use the default FTPs.
FTP user account access: Private FTP access allows only people on your internal network to write files to your server. Public FTP access allows users both inside and outside your local network to read or write files on your server, provided they have an account and password. If, for example, you want to be able to update your web site from home using FTP, you would choose the "Public" setting. We strongly recommend you leave this as Private unless you have a specific reason to do so.
FTP access limits: This allows you to set an overall site-wide policy for FTP access. The setting you choose here will override all other FTP settings on your server . For example, if you choose "Disable public FTP access" here and then later configure an i-bay to allow public FTP access from the Internet, such access will be forbidden. Note that one of the choices here allows you to completely disable any use of FTP.
Local networks
Your SME Server provides services to machines on the local network and it gives machines on that network special privileges and access. For example, only machines connected to the local network can access the mail server on your server to send mail. When you configured your server, you provided it with sufficient information to deduce its own local network. Machines on the network are automatically identified by the server as being eligible for these privileges and access.
If your company only has one network that is being serviced by the server, you do not need to add any information here.
Some advanced users may wish to extend privileges to more than one network of computers. If you would like your server to identify one or more additional networks for those privileges, you will be asked to enter those network IDs and the subnet mask for each network here.
Port forwarding
Your SME Server provides the ability to forward its ports to other machines.
You can use the panel shown above to modify your firewall rules so as to open a specific port (or range of ports) on this server and forward it to another port on another host. Doing so will permit incoming traffic to directly access a private host on your LAN.
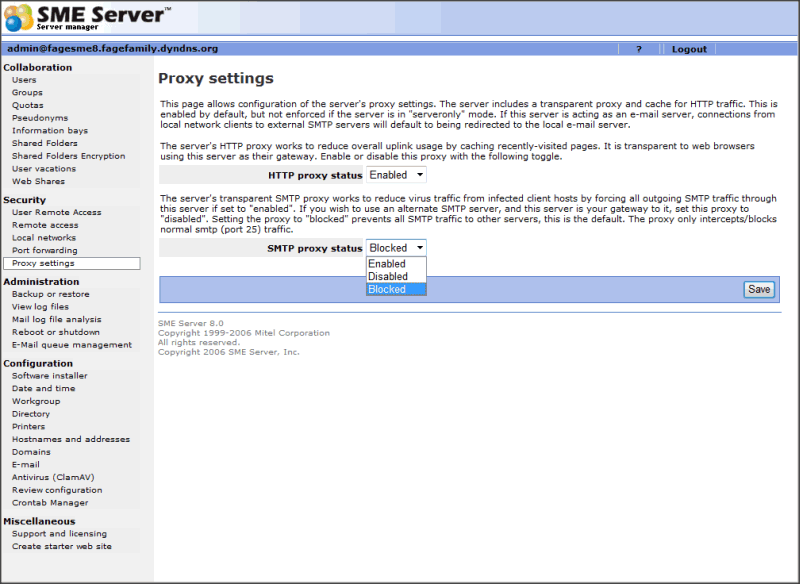
Proxy settings
Your SME Server has a transparent HTTP and SMTP proxy.
HTTP Proxy
The server's HTTP proxy works to reduce overall uplink usage by caching recently-visited pages. It is transparent to web browsers using this server as their gateway.
SMTP Proxy
The server's transparent SMTP proxy works to reduce virus traffic from infected client hosts by forcing all outgoing SMTP traffic through this server. If you wish to use an alternate SMTP server, and this server is your gateway to it, disable this proxy.
- Disabled. Clients behind SME Server are allowed to connect to any SMTP server anywhere in the world (that allow them to).
- Blocked. This forces all SMTP traffic to go through the server and be authenticated. All attempts to connect to any SMTP Server other than the SME Server will be blocked and treated as if there is no SMTP server on the other end. (This is the new default)
- Enabled. Any attempt to connect to an SMTP Server other than the SME Server will be redirected to the SME Server. If someone attempts to connect to an external smtp server (gmail for example) it will be redirected to the sme server. If they then have it set to authenticate to that external server instead of passing the user/pass to the external server it will pass it to the sme server and fail. (This is the old default)
Note: The server (by default) now requires email clients (other than webmail) to authenticate and will not allow auth to occur over an unsecure link. If for example you are using thunderbird then you must set the authentication method to normal password. Leave the connection security at starttls or ssl/tls.