Difference between revisions of "Email Whitelist-Blacklist Control/fr"
m (→Mainteneur) |
|||
| Line 4: | Line 4: | ||
[mailto:stephdl@de-labrusse.fr stephdl] Stéphane de Labrusse AKA [[User:stephdl|Stephdl]]<br /> | [mailto:stephdl@de-labrusse.fr stephdl] Stéphane de Labrusse AKA [[User:stephdl|Stephdl]]<br /> | ||
| + | |||
| + | === Version === | ||
| + | {{ #smeversion: smeserver-wbl }} | ||
| + | |||
| + | ===Description=== | ||
| + | |||
| + | This contrib provides a server-manager panel to designate user defined email whitelists and blacklists. | ||
| + | |||
| + | An email whitelist is a list of hosts, domains, or email addresses which will be accepted by SME Server regardless of possible spam content or origin. Administrators should use caution when using whitelists as email coming from whitelisted addresses will bypass many of the mechanisms that SME provides for identifying unsafe email messages. | ||
| + | |||
| + | An email blacklist is a list of hosts, domains, or email addresses that will be blocked all of the time. | ||
| + | |||
| + | ===Installation=== | ||
| + | Install of the lastest Email Whitelist-Blacklist package is from the smecontribs repo: | ||
| + | |||
| + | 1. Install package: | ||
| + | *'''For SME 8''' | ||
| + | yum --enablerepo smecontribs install smeserver-wbl | ||
| + | * '''For SME 9''' | ||
| + | yum install --enablerepo=smecontribs smeserver-wbl | ||
| + | |||
| + | 2. Reconfigure machine: | ||
| + | signal-event console-save | ||
| + | or if you prefer to reboot your server | ||
| + | signal-event post-upgrade; signal-event reboot | ||
| + | |||
| + | Once you do this a new menu item will be visable in the Server-Manager on the left hand side, called E-mail WBL. Clicking on this will present you with 3 buttons. | ||
| + | '''E-mail WBL''' | ||
| + | E-mail traffic is scanned and may be blocked due to the various screening methods enabled. | ||
| + | You may use this panel to define e-mail white/black lists. | ||
| + | Black lists are used for rejecting e-mail traffic. | ||
| + | '''[REJECT]''' | ||
| + | White lists are used for accepting e-mail traffic. | ||
| + | '''[ACCEPT]''' | ||
| + | When completed entering wbls above you must execute the email-update event to restart | ||
| + | services and load in your changes. | ||
| + | '''[UPDATE]''' | ||
| + | |||
| + | If you press the REJECT button you will see the following window. | ||
| + | [[File:email-Reject.jpg]] | ||
| + | |||
| + | If you press the Accept button you will see the following window. | ||
| + | [[File:Email-accept.jpg]] | ||
| + | |||
| + | And finally If you press the UPDATE button you will simply be presented with one button to; | ||
| + | Execute the email-update event now to restart services and load in your changes. | ||
| + | |||
| + | This will apply any of the changes you made in the Reject or Accept windows. | ||
| + | |||
| + | ===Usage Examples=== | ||
| + | |||
| + | Black Lists: REJECT | ||
| + | |||
| + | The '''qpsmtpd badhelo''' is effective in examining the SMTP HELO string and then block mail based on this string. Entries follow the following format. | ||
| + | something.a.somehost.com | ||
| + | To find the proper string to enter on the qpsmtp badhelo line. 1. Open an offending email. 2. Open the header of the email. 3. Look for a line that says, | ||
| + | (HELO something.a.somehost.com) | ||
| + | Partial strings will not work, E.G. in the previous example somehost.com will not work. It must be the complete HELO string. | ||
| + | {{Note box|Using qpsmtpd badhelo will stop all mail at a domain that uses that specific HELO string. It's not looking at a specific email. This strategy isn't always effective as spammers generally change this field to stop this kind of detection. Also companies have several SMTP gateways so you may see mail from mail1.domain.com and mail2.domain.com . You will then need to add both of these. The advantage however is if you do want to stop all mail from one source, it can be effective. }} Alternatively you may use the ip address. Again look in the header for the Helo line. It may look something like this, | ||
| + | Received: from smtprelay0207.c.somehost.com (HELO smtprelay.c.somehost.com) '''(123.111.123.321''') | ||
| + | Now simply add the IP address you found in the HELO line. | ||
| + | 123.111.123.321 | ||
| + | |||
| + | White Lists: ACCEPT | ||
| + | |||
| + | Whitelisthosts - see this post http://forums.contribs.org/index.php/topic,51429.0.html | ||
| + | |||
| + | Single IP | ||
| + | 192.168.10.1 | ||
| + | |||
| + | Subnets | ||
| + | 192.168.10. (be careful - with no trailing . you match 192.168.100 - 192.168.109. ) | ||
| + | 192.168 | ||
| + | |||
| + | WhitelistHELO | ||
| + | host.domain.com | ||
| + | |||
| + | Whitelistsenders | ||
| + | joe@foo.com | ||
| + | @foo.com | ||
| + | |||
| + | |||
| + | === Known Issues === | ||
| + | qpsmptd dnsbl rejects mail despite sender being listed in whitelistsenders and whitelisthelo | ||
| + | [[bugzilla:8327]] | ||
| + | [[bugzilla:8747]] | ||
| + | |||
| + | === Bugs === | ||
| + | Please raise bugs under the SME Contribs section in {{BugzillaFileBug|product=SME%20Contribs|component=smeserver-wbl|title=bugzilla}}. | ||
| + | {{#bugzilla:columns=id,product,version,status,summary |sort=id |order=desc |component=smeserver-wbl |noresultsmessage="No open bugs found."}} | ||
| + | ---- | ||
| + | [[Category: Contrib]] | ||
| + | [[Category: Mail]] | ||
| + | [[Category: Administration:Content Spam Virus Blocking]] | ||
Revision as of 17:18, 19 September 2015
Mainteneur
Initialement développée par Darrell May.
stephdl Stéphane de Labrusse AKA Stephdl
Version
Description
This contrib provides a server-manager panel to designate user defined email whitelists and blacklists.
An email whitelist is a list of hosts, domains, or email addresses which will be accepted by SME Server regardless of possible spam content or origin. Administrators should use caution when using whitelists as email coming from whitelisted addresses will bypass many of the mechanisms that SME provides for identifying unsafe email messages.
An email blacklist is a list of hosts, domains, or email addresses that will be blocked all of the time.
Installation
Install of the lastest Email Whitelist-Blacklist package is from the smecontribs repo:
1. Install package:
- For SME 8
yum --enablerepo smecontribs install smeserver-wbl
- For SME 9
yum install --enablerepo=smecontribs smeserver-wbl
2. Reconfigure machine:
signal-event console-save
or if you prefer to reboot your server
signal-event post-upgrade; signal-event reboot
Once you do this a new menu item will be visable in the Server-Manager on the left hand side, called E-mail WBL. Clicking on this will present you with 3 buttons.
E-mail WBL E-mail traffic is scanned and may be blocked due to the various screening methods enabled. You may use this panel to define e-mail white/black lists. Black lists are used for rejecting e-mail traffic. [REJECT] White lists are used for accepting e-mail traffic. [ACCEPT] When completed entering wbls above you must execute the email-update event to restart services and load in your changes. [UPDATE]
If you press the REJECT button you will see the following window.
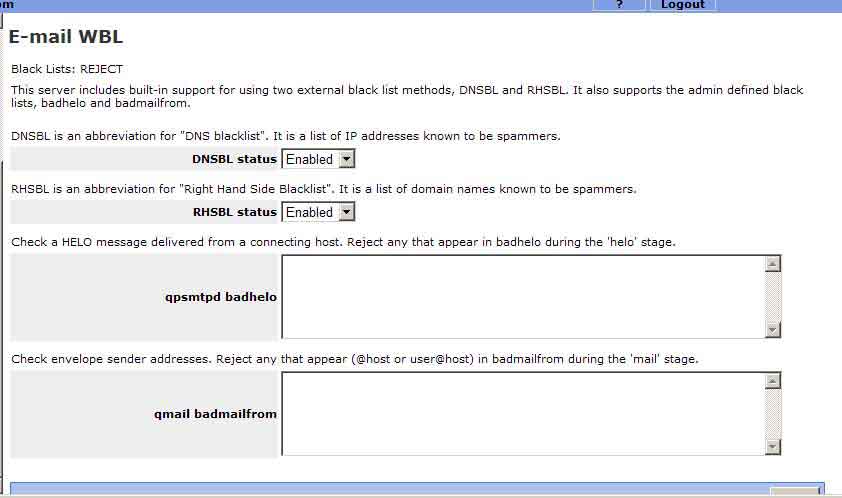
If you press the Accept button you will see the following window.
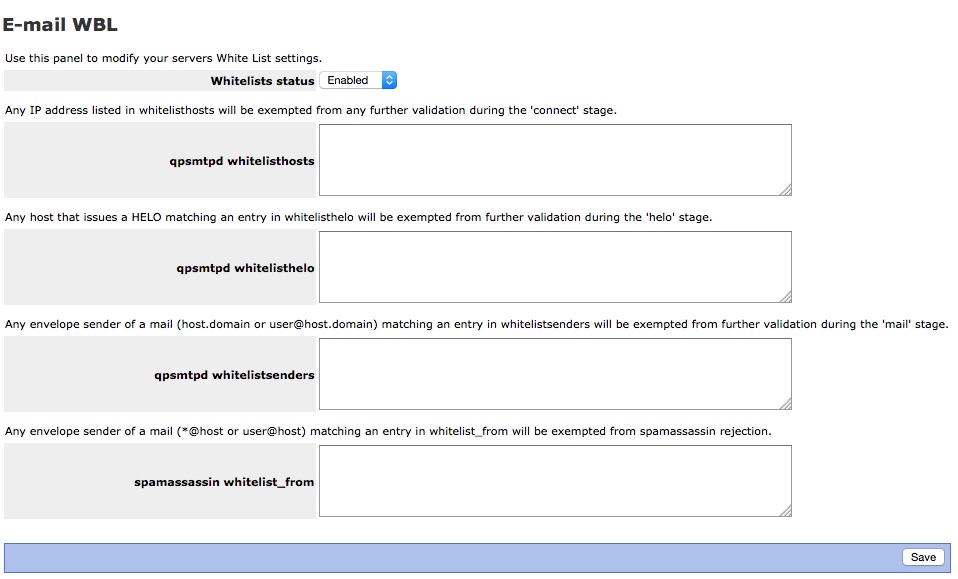
And finally If you press the UPDATE button you will simply be presented with one button to;
Execute the email-update event now to restart services and load in your changes.
This will apply any of the changes you made in the Reject or Accept windows.
Usage Examples
Black Lists: REJECT
The qpsmtpd badhelo is effective in examining the SMTP HELO string and then block mail based on this string. Entries follow the following format.
something.a.somehost.com
To find the proper string to enter on the qpsmtp badhelo line. 1. Open an offending email. 2. Open the header of the email. 3. Look for a line that says, (HELO something.a.somehost.com) Partial strings will not work, E.G. in the previous example somehost.com will not work. It must be the complete HELO string.
Alternatively you may use the ip address. Again look in the header for the Helo line. It may look something like this,
Received: from smtprelay0207.c.somehost.com (HELO smtprelay.c.somehost.com) (123.111.123.321) Now simply add the IP address you found in the HELO line.
123.111.123.321
White Lists: ACCEPT
Whitelisthosts - see this post http://forums.contribs.org/index.php/topic,51429.0.html
Single IP
192.168.10.1
Subnets
192.168.10. (be careful - with no trailing . you match 192.168.100 - 192.168.109. ) 192.168
WhitelistHELO
host.domain.com
Whitelistsenders
joe@foo.com @foo.com
Known Issues
qpsmptd dnsbl rejects mail despite sender being listed in whitelistsenders and whitelisthelo
bugzilla:8327
bugzilla:8747
Bugs
Please raise bugs under the SME Contribs section in bugzilla .
| ID | Product | Version | Status | Summary (6 tasks) ⇒ |
|---|---|---|---|---|
| 12649 | SME Contribs | 11.0 | CONFIRMED | SME11 remove /etc/e-smith/templates/var/service/qpsmtpd/config/badmailfrom |
| 10472 | SME Contribs | Futur | CONFIRMED | NFR Add subnet checking to whitelist hosts |
| 10117 | SME Contribs | Futur | CONFIRMED | add support for URIBL |
| 9276 | SME Contribs | 8.2 | CONFIRMED | design and documentation of qpsmtpd wbl vs spamassassin white or black lists |
| 9275 | SME Contribs | 8.2 | CONFIRMED | wbl whitelist status switch does nothing in server manager |
| 4664 | SME Contribs | 7.3 | CONFIRMED | Redesign wbl dbase to improve efficiency |