Difference between revisions of "OpenVPN SiteToSite"
m |
m (→Configuration) |
||
| Line 75: | Line 75: | ||
* '''Remote Networks''': Enter in this field the networks reachable through the other end point. For example, on SME1, you'll enter the local networks of SME2: 192.168.11.0/255.255.255.0, on SME2, you'll enter the local network of SME1: 192.168.9.0/255.255.255.0 | * '''Remote Networks''': Enter in this field the networks reachable through the other end point. For example, on SME1, you'll enter the local networks of SME2: 192.168.11.0/255.255.255.0, on SME2, you'll enter the local network of SME1: 192.168.9.0/255.255.255.0 | ||
| + | |||
| + | Once both peers are configured, we'll get something like this: | ||
| + | [[File:Ovpn_s2s_rzo_apres_vpn.png|768px|thumb|center|After the VPN inter-connection]] | ||
| + | |||
| + | We are now able to ping hosts on the other side using their private IP. | ||
=== Additional options === | === Additional options === | ||
Revision as of 13:09, 20 October 2010
Maintainer
Daniel B.
Firewall Services
mailto:daniel@firewall-services.com
Version
Description
smeserver-openvpn-s2s lets you inter-connect several SME servers, and their local networks with secure VPN. It uses OpenVPN as backend, using either the simple shared secret method, or the stronger, but more complex TLS mechanism.
Installation
- install the rpms
yum --enablerepo=smecontribs install smeserver-openvpn-s2s
This contrib has been tested on SME 7.5.1 and SME 8b6
Configuration
This contrib lets you create as many servers and clients daemon. A server can only be used by one client (it's not a one server for multiple clients solution), so if you wan't to connect several SME to one central server, you'll need to create several server daemon, binding on different ports. Once conected, OpenVPN makes no difference between client and server, we just need to define which endpoint will bind on a local port waiting for a connection of the remote endpoint.
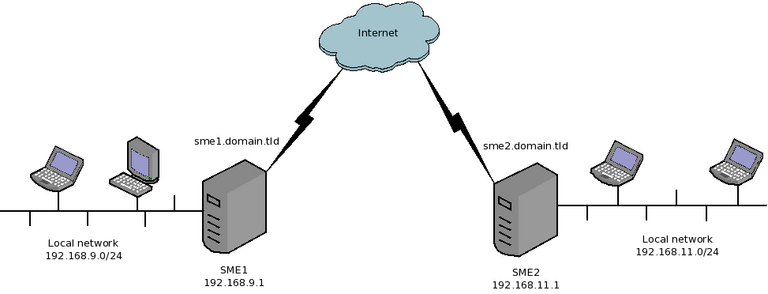
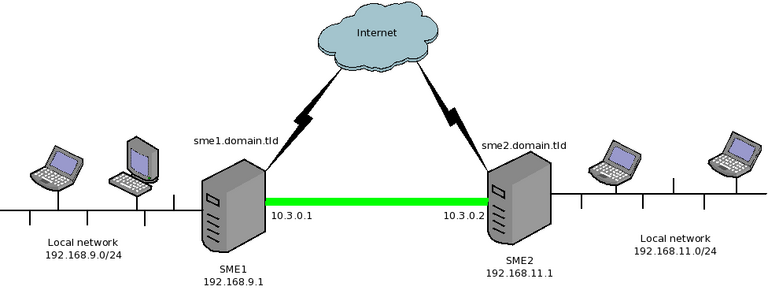
Lets take a simple example. We manage two SME servers
- SME1
- Local network: 192.168.9.0/24 (192.168.9.1 being the address of the internal interface of SME1)
- Public DNS domain name: sme1.domain.tld (resolves to the public IP of SME1)
- SME2
- Local network: 192.168.11.0/24 (192.168.11.1 being the address of the internal interface of SME2)
- Public DNS domain name: sme2.domain.tld (resolves to the public IP of SME2)
Now, we want to connect both servers, so that the two private networks can see each other.
We will configure SME1 as a OpenVPN client and SME2 as an OpenVPN server. We'll use the shared secret method as it's easier to configure.
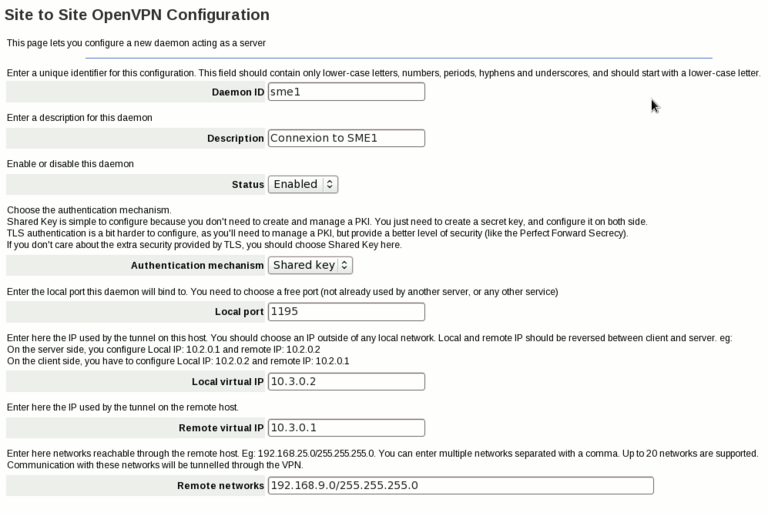
So, in SME1 server-manager, we'll have to add a new client (in OpenVPN Site to Site panel) and configure it like this:
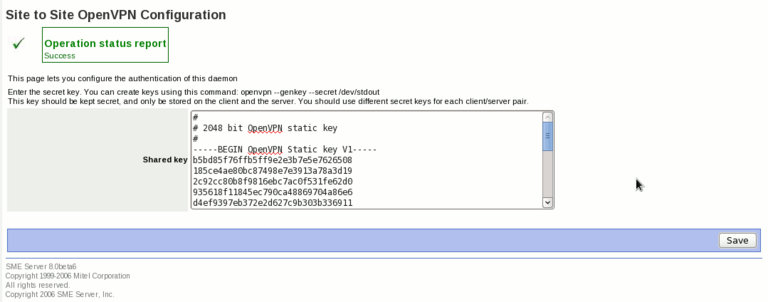
Then, click on the next button, we'll have a page to configure the shared secret key. We can generate such keys using openvpn command (on your SME Server, or on another linux box. I'm not sure if we can do the same under Windows). To create a new key, type the following command on your shell:
openvpn --genkey --secret /dev/stdout
And copy the output in the page of the server-manager, like this:
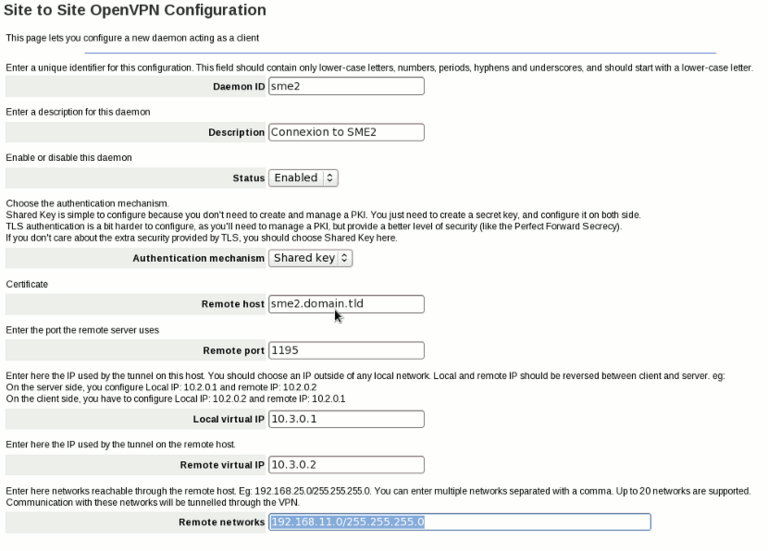
Now, on SME2, we add a new server, and configure it like this:
On the next page, we have to enter the same key we've used on SME1
Here are the explanation of some settings:
- Daemon ID: just a unique identifier for this connection.
- Description: a human readable description (eg link between SME1 and SME2)
- Status: you can disable a VPN connection if you want, but most of the time you'll want it enabled
- Authentication mechanism: How both ends will authenticate. The easier solution is the Shared Key. You can also use TLS if you want, but it's usually for power users (you need to manage a PKI, you can use PHPki for this if you want)
- Remote Host (available on client only): IP or FQDN to the remote peer
- Remote Port (available on client only): port used by the remote server
- Local Port (available on server only): port on which the openvpn server will bind, waiting for connection of the remote peer. Remote Port on the client and Local Port on the server should be the same
- Local Virtual IP: the IP used internally by OpenVPN. You should choose a IP outside of any local networks
- Remote Virtual IP: the IP used internally by OpenVPN on the other side. Those two virtual IP should be reversed between the client and the server
- Remote Networks: Enter in this field the networks reachable through the other end point. For example, on SME1, you'll enter the local networks of SME2: 192.168.11.0/255.255.255.0, on SME2, you'll enter the local network of SME1: 192.168.9.0/255.255.255.0
Once both peers are configured, we'll get something like this:
We are now able to ping hosts on the other side using their private IP.
Additional options
Some advanced settings are not available on the panel, but only with db commands:
- LogLevel: if you want to increase the verbosity of a daemon (either client or server), you set the LogLevel property. Valid LogLevel value are numbers between 0 (no output except fatal errors) to 11 (really verbose)
- Protocol: can be tcp or udp. The default is to use udp. You shouldn't change this setting unless you have good reason to do so. This setting should match the other endpoint.
- Cipher: The cipher used. The default is to use the BlowFish algorithm. This setting should match on both the server and the client. You can get a list of available ciphers using this command:
openvpn --show-ciphers | egrep '^[A-Z]{2}' | awk {'print $1'}
- Compression: can be enabled or disabled. Toggle the internal compression used by OpenVPN. The default is enabled. This setting should match on both the server and the client
If you use TLS as authentication mechanism, you can set some other properties:
- RemoteCommonName: The connection will be accepted only if the remote endpoint has a valid certificate, with this common name
- CheckCertificateUsage: can be enabled or disabled (default is disabled). If enabled, a server daemon will only accept the connection if the remote endpoint present a client certificate, and a client daemon will only accept the connection if the remote endpoint present a server certificate.
example:
db openvpn-s2s setprop sme1 LogLevel 5 Cipher AES-256-CBC Compression disabled signal-event openvpn-s2s-update
Templates for all the daemon (client and server) are in /etc/e-smith/templates/etc/openvpn/s2s/openvpn-s2s.conf/ You can create custom templates in /etc/e-smith/templates-custom/etc/openvpn/s2s/openvpn-s2s.conf/, the change will affect all the daemons. If you want to add special options only for one particular daemon, you can create a special file. For example, you want to add special OpenVPN options for a daemon called myvpn (daemon ID), and these options are not available with DB properties. Just create a file /etc/openvpn/s2s/myvpn.conf.custom, and add your options here. It'll be automatically loaded on templates expansion. example:
echo "no-replay" > /etc/openvpn/s2s/myvpn.conf.custom echo "reneg-sec 900" >> /etc/openvpn/s2s/myvpn.conf.custom signal-event openvpn-s2s-update
Backup and Restore
You should backup the directories /etc/openvpn/s2s/priv and /etc/openvpn/s2s/pub keys and certificates used by this contrib are stored there.
Uninstall
If you want to remove the contrib, just run:
yum remove smeserver-openvpn-s2s
You can then remove the directory /etc/openvpn/s2s if you really want to remove everything (including the private keys and certificates)
Source
The source for this contrib can be found in the smeserver CVS on sourceforge.
Bugs
Please raise bugs under the SME-Contribs section in bugzilla and select the smeserver-openvpn-s2s component or use this link